Update (08/16/2016): The Pseudo Darkleech campaign redirects to Neutrino EK again but EITest still points to RIG EK.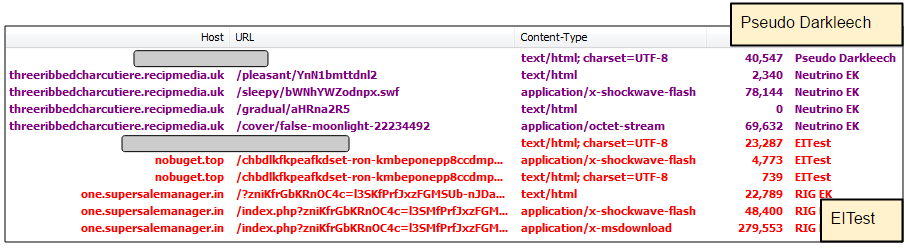
Exploit kits are going through some strange phases these days. Two major malware distribution campaigns, namely Pseudo Darkleech and EITTest traditionally reserved for Neutrino EK were redirecting to underdog RIG EK. Several security researchers (Oddly_Normal, @malware_traffic, BroadAnalysis) pointed out this unexpected behaviour on Twitter.

Our telemetry records only show a few instances of Neutrino via what we earlier described on this blog as the jQueryGate while the fingerprinting pre-gate itself was nowhere near as active.
Time will tell if this is a temporary blip or not. While we have seen some switches between EKs in the past, the Pseudo Darkleech and EITest campaigns which were once part of Angler’s distribution channels, have always been very coveted.
We will keep monitoring this situation and update this post accordingly.
IOCs:
Payload from Pseudo Darkleech:
c4daadcbb525b96644f672025f3a4f3261a40a7b6250f3c726de3f4566cb6cf3
Payload from EITest:
446a639371b060de0b4edaa8789f101eaeae9388b6389b4c852cd8323ec6757c










