Cyber-criminals continue to impersonate brands via well-crafted phishing websites. We previously covered attacks on both consumers and businesses via online searches for popular brands leading to scams or malware.
Digital assets such as cryptocurrencies or NFTs are highly coveted by threat actors due to the high gains that can be made, even via a simple phishing attack. The FBI released an advisory on August 4 warning about such attacks that often target users via social media.
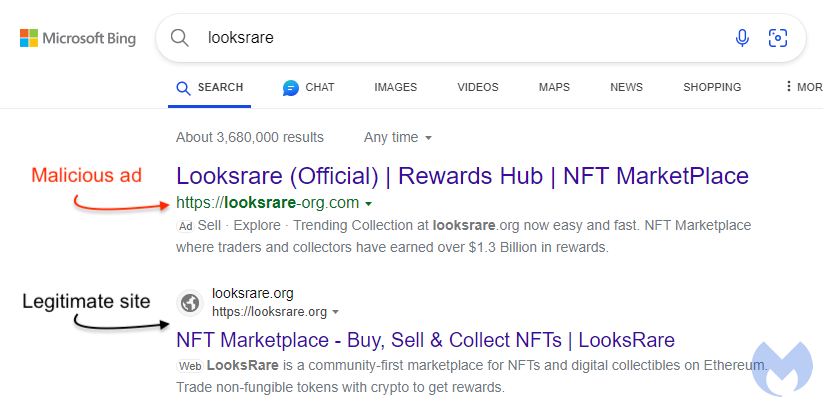
However, malicious ads can also be used to lure potential victims. In this blog post, we investigate a malvertising campaign targeting LooksRare, an NFT marketplace. The ad was shown on Google and Bing and helped scammers to phish users with added credibility, allegedly defrauding one of them for $300K worth of NFTs.
Malicious ads for NFT marketplace
Non-fungible tokens (NFTs) are assets that have been tokenized via a blockchain. Some popular examples include images that become collectibles and often involve substantial amounts of money.
In a post on social media, one user claimed to have lost $300K worth of NFTs because they clicked on a Google ad. We could not immediately find the same ad on Google, but we did see one on Microsoft Bing that is likely tied to the same campaign:
The “why you’re seeing this ad?” dialog shows the advertiser as being from China and the ad by a company named Fantacy Click Limited:
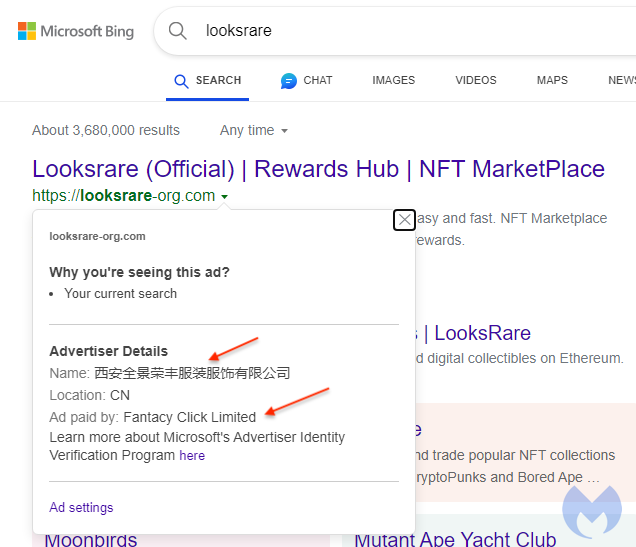
Microsoft’s Advertiser Identity Verification Program states that when ads don’t pass policy checks, they either stop serving the ads or suspend the advertiser’s account. In this example of brand impersonation, the phishing domain (looksrare-org[.]com) was freshly registered on August 7th 2023. While we can’t expect companies to track every possible brand out there, a simple domain registration check could easily reveal risky advertisers.
Decoy redirect
The threat actor invested minim efforts to deceive crawlers and other automation tools by setting up the usual cloaking page. In this example, you get redirected to an “about us” decoy page:
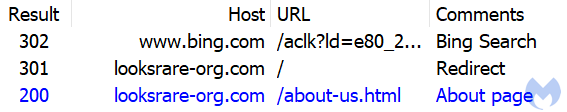
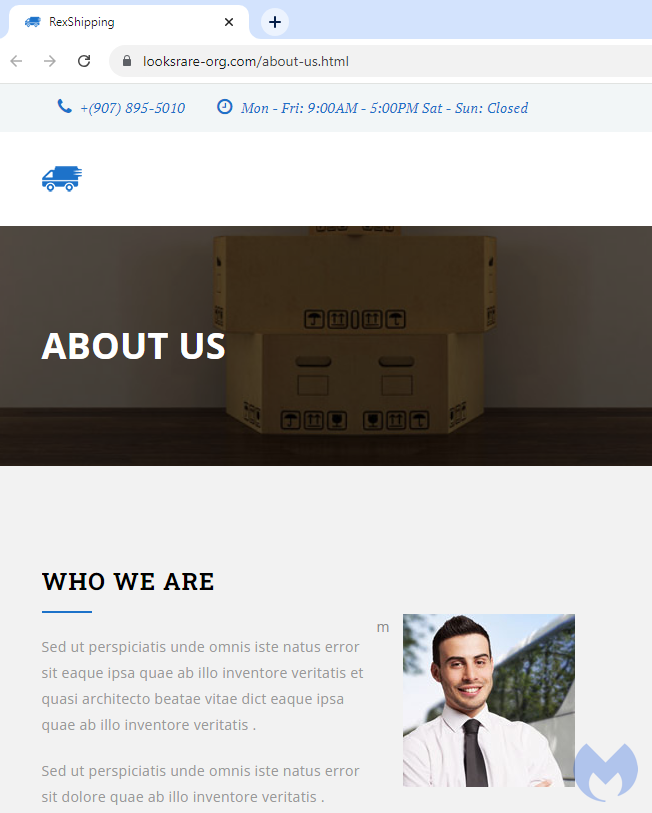
Unfortunately, while it is easy for humans to see that this site is completely fake, machines will find no security issue and validate it:
Redirect and phishing page
Legitimate users and intended victims clicking on the ad will get a different experience. They are redirected to a second website (www-market-lookshare[.]com) that was also registered very recently and that acts as the phishing site:
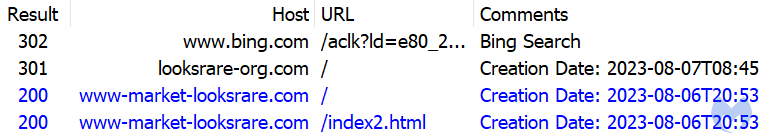
This site is a close replica of the official looksrare[.]org domain:
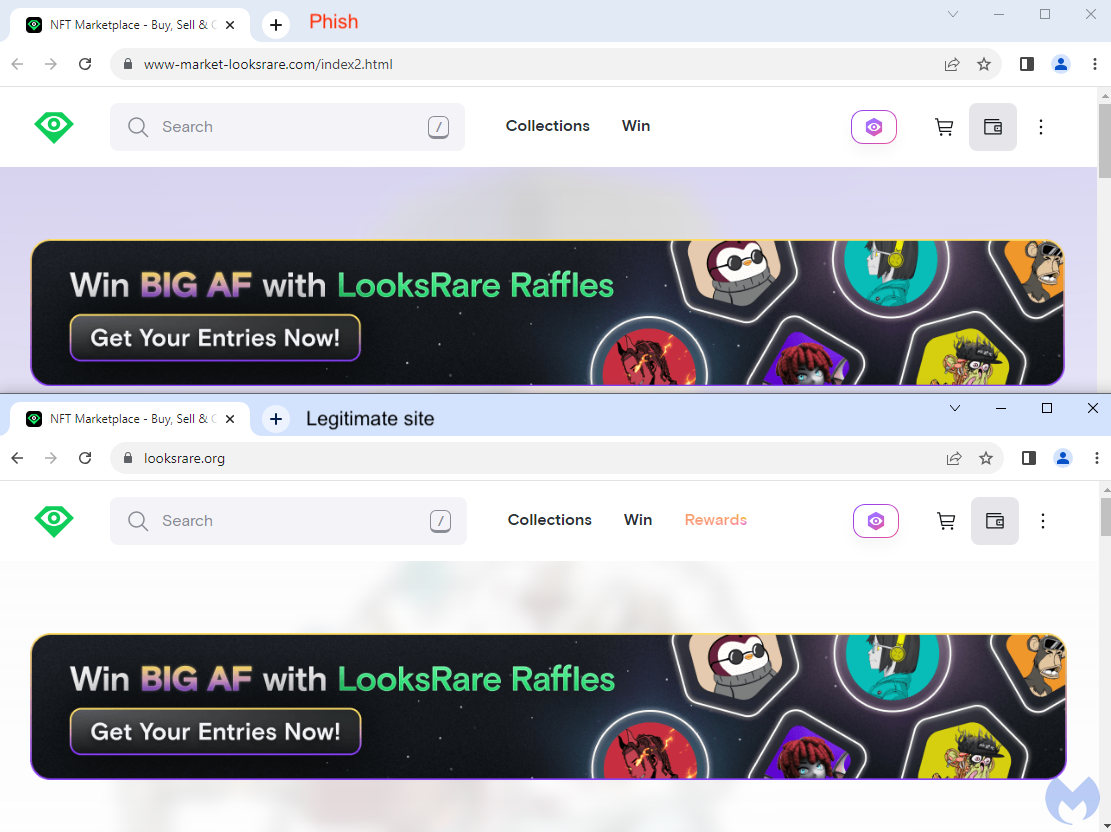
Draining wallets
The phishing site invites victims to connect their wallet by scanning a QR code:
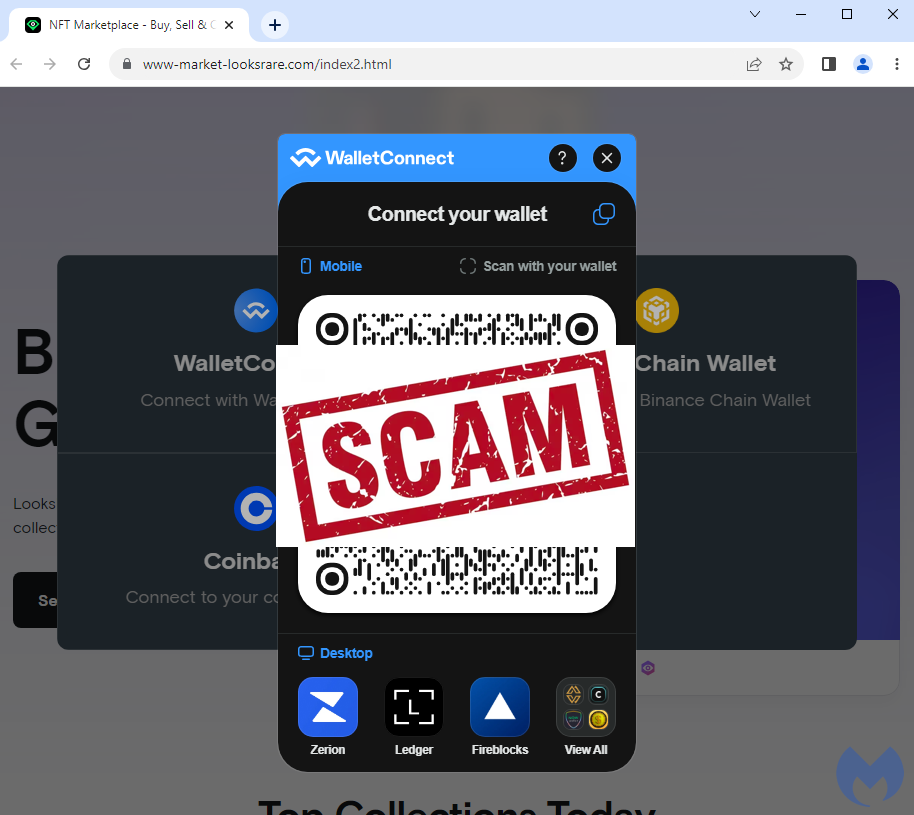
If you are running the Coinbase extension, you will get a request such as the one below:
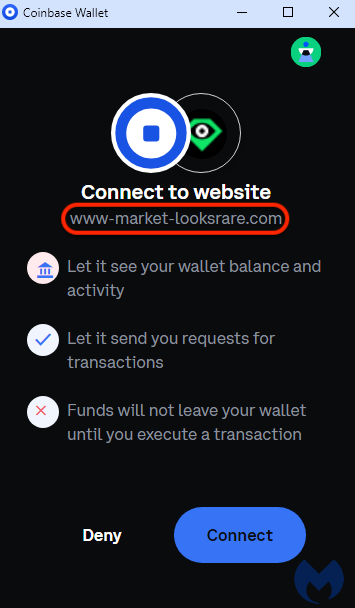
After connecting to the victim’s wallet, the threat actor will run a few queries and eventually prompt the user to sign a message, granting them access to their NFTs. Someone has analyzed the transactions associated with this campaign in a thread here.
Phishing and crypto assets
Many people have expressed concerns about cryptocurrencies and other digital assets due to how many scams there are, but also because of how easy it can be to lose very large sums of money with just a few wrong clicks.
Phishing sites can be very convincing especially if the user visited them via a paid Google or Bing search ad that they expect has already been verified as legitimate.
There are a number of tools that can help to protect your wallets and gain better visibility over incoming transactions. Malwarebytes Browser Guard can block those phishing websites and malicious ads to keep you out of harm’s way.
We have reported this malicious ad to Microsoft via their low quality ad submission & escalation form. An automated response informed us that Microsoft will review and take action on any ads found to be in violation within 3-5 days. Unfortunately, this gives criminals enough time to run their malvertising campaigns uninterrupted and switch accounts by the time they are caught.
Indicators of compromise
looksrare-org[.]info
looksrare-org[.]com
www-market-looksrare[.]com










