It recently came to pass that about 15 percent of the Malwarebytes blog team flew into London for Infosec Europe, Bsides London and the EU Security Blogger Awards.

It also came to pass that I had to wait to get my hands on some photographs and bash some of my Writey Writer Workshop into something approaching blog format (that hasn’t quite happened yet, but it’s on the way). We can’t mention London without some photographs, so here are some vaguely touristy shots of the Tower, London Eye, Buckingham Palace and the Houses of Parliament with weather ranging from “Amazing” to “First plane out of the country, please”:
I did try to take a picture of the large, cavernous space that is the Olympia, home of this year’s event, but a combination of poor photograph lighting and “not knowing how you brighten an image in Gimp” has resulted in the following JJ Abrams moment:

I mean…it’s definitely brighter.
The Malwarebytes team & booth at Infosec Europe were very busy indeed, so here’s a couple of shots (including obligatory t-shirts and a rather nice webcam cover):
Some observations about Infosec Europe this year:
1) The shift from April to June unfortunately nudges temperatures the wrong side of “I’M MELLLTIIIIING”, with all manner of hotels and public transport cranking their heating up accordingly. Why do public services turn the heating up in hot temperatures, anyway?
2) There were a lot of non-infosec events taking place at the same time, which meant it was a bit of a nightmare to get a hotel room, and that was despite booking in advance. In previous years, my Infosec hotels have included:
* A Bed & Breakfast where nobody spoke English and breakfast was served in the basement. There were no windows. * A hotel whose room was a box roughly the size of a double bed, with a single bed up against a bare wall and an empty oil heater. There was no window. * What I can only describe as “some guy’s flat”, complete with pictures hung sideways and a collection of scary characters hanging around outside at 1AM. I had a window; I was rather hoping there wouldn’t be.
I guess what I’m trying to say is, book early. Top tip: the date for next year’s Infosec Europe is 7-9th June, which means there’s a good chance unrelated events such as BSides and RSA Unplugged may take place somewhere alongside it.
Book early, book often (well, book once. Don’t book often, that’d be silly).
3) We won the EU Security Blogger Award for Best Corporate Blog, which is great! Thanks for all of your votes.
Unfortunately, the awards took place at 5:30 PM at the Infosec Europe venue – which is the exact time BSides London finished, a brisk(ish) walk or a train hop away. As a result, many of the attendees for the Blogger event were found racing out of the BSides building before half past. We also had a bit of a challenge in terms of finding the venue, which was nestled inside the London Olympia. We almost ended up at the John McAfee party by mistake, and turned up just as the awards were getting started.

I was actually trying to work out what kind of gherkin was on my free cheeseburger when the announcement that we’d won flashed up on the screen. I never found out what kind of gherkin it was, but that didn’t matter because lots of cheers and clapping.

L to R: Brian Honan, Jovi, Chris and Jack Daniel (Thanks to Infosec Europe for both pics)
Here I am next to Alan Shimel as I attempt to make some sort of acceptance speech that wasn’t just excited babble: I think I failed miserably, to be honest. It’s allowed just the once, right?
4) My Writey Writer’s Workshop at BSides London seemed to go very well, and thanks to everyone for coming along.
The bulk of it was advice on working in Infosec (specifically, the part involving blogs and how to work best with everyone you’ll meet along the way) along with a couple of “Try to avoid this” moments. There were also some prizes for the quiz, kept safely under lock and key:

I can neither confirm nor deny that some of the uneaten prizes vanished mysteriously after the event.
The quiz took the form of a fake blog, giving examples lots of common Infosec writing practices which tend to go horribly wrong if the writer isn’t careful.
Here’s one of the questions posed during the Workshop: what would you think is wrong with this blog post about a phishing email?
You might have wondered at some point why we upload a screenshot of an email then type it all out anyway. Well, the answer is that without the copy / paste text blast, readers with limited vision or no vision at all will have zero idea what the specific wording of the threat is.
On a similar note:
This is a very basic thing, but something which probably doesn’t occur to a lot of writers (I did the screenshot / no text thing for a long time until someone who read one of my blogs became exasperated with my screenshot habits, and rightly so). Alt text on images is also good for screen readers.
Can you spot the good thing in the above post? That would be the large “This is fake” warning we’ve plastered onto the screenshot. I’m a bit particular about the “clean” look of a screenshot – I find additions to the basic image a little unsightly, but the alternative isn’t very appealing either.
Elsewhere in the quiz, I covered a seemingly harmless looking blog entry. What could go wrong with a written URL in the title? Quite a lot, as it happens. Once your blog goes out into the big wide world, it’s at the mercy of linking, social networks and all the curious quirks they bring with them. If you’re writing about an exploit site and place the URL in the title “as is” – even without any http or www – this is what will happen once it hits Twitter:
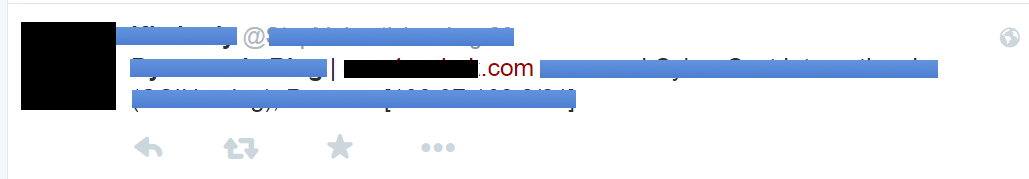
Buried under all of the redactions (no name and shame here) is a fully functional URL which is now also clickable, and attached to Tweets with your name or company on it.
To coin a phrase, “Whoops.”
My final extract from Writey Writer’s fake Infosec blog would be one of my shorter blog posts. Can you guess what’s wrong (and why I am indeed on Page 30 of “The Googles”?)
URL bar, left hand side. What’s missing?
A little green padlock:
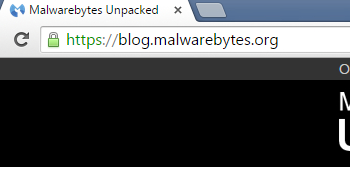
That little green padlock is very important on websites where you make payments or send personal data. Why is this a sensible thing to have on your blog? Well, apart from it being a good idea for a security company to have HTTPS on offer in general, more and more search engines are penalising websites for being plain old HTTP.
Google may drop you in rankings in favour of sites touting a padlock; FireFox is starting to deprecate websites which are non HTTPS (ie portions of the website are going to stop working in their browser over time). Chrome has a bit of a thing about insecure pages. However you look at it, HTTPS is definitely the way to go if you have a blog – doubly so if you’re involved in Infosec.
These are just a few of the things covered in the Workshop, but hopefully the general takeaway was that there’s always something you can improve on, and more often than not, bad habits which need to be ditched. We work hard to ensure the blog is as interesting and readable as it can be, and we hope you enjoy the content we continue to produce.
Farewell, London – we’ll see you again!
Christopher Boyd










