Adware.SearchEngineHijack
Short bio
Adware.SearchEngineHijack is Malwarebytes’ detection name for a family of search hijackers that display advertisements in their search results.
Symptoms

Adware.SearchEngineHijack as promoted in the webstore
Type and source of infection
Adware.SearchEngineHijack is usually installed by users due to promises of improved searching. The installer then hijacks the search results to a domain that belongs to the threat-actors, which will show sponsored results.
Protection
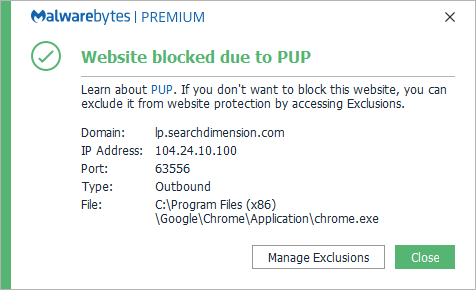
Malwarebytes blocks the domain searchdimension.com
Remediation
Malwarebytes can detect and remove Adware.SearchEngineHijack without further user interaction.
- Please download Malwarebytes to your desktop.
- Double-click MBSetup.exe and follow the prompts to install the program.
- When your Malwarebytes for Windows installation completes, the program opens to the Welcome to Malwarebytes screen.
- Click on the Get started button.
- Click Scan to start a Threat Scan.
- Click Quarantine to remove the found threats.
- Reboot the system if prompted to complete the removal process.
Malwarebytes removal log
A Malwarebytes log of removal will look similar to this:
Malwarebytes
www.malwarebytes.com
-Log Details-
Scan Date: 9/24/18
Scan Time: 11:21 AM
Log File: 48e4d27b-bfdb-11e8-a4f1-00ffdcc6fdfc.json
-Software Information-
Version: 3.5.1.2522
Components Version: 1.0.441
Update Package Version: 1.0.6983
License: Premium
-System Information-
OS: Windows 7 Service Pack 1
CPU: x64
File System: NTFS
User: {computername}\{username}
-Scan Summary-
Scan Type: Threat Scan
Scan Initiated By: Manual
Result: Completed
Objects Scanned: 252029
Threats Detected: 17
Threats Quarantined: 17
Time Elapsed: 4 min, 1 sec
-Scan Options-
Memory: Enabled
Startup: Enabled
Filesystem: Enabled
Archives: Enabled
Rootkits: Enabled
Heuristics: Enabled
PUP: Detect
PUM: Detect
-Scan Details-
Process: 0
(No malicious items detected)
Module: 0
(No malicious items detected)
Registry Key: 0
(No malicious items detected)
Registry Value: 0
(No malicious items detected)
Registry Data: 0
(No malicious items detected)
Data Stream: 0
(No malicious items detected)
Folder: 4
Adware.SearchEngineHijack, C:\Users\{username}\AppData\Local\Google\Chrome\User Data\Default\Extensions\mfeigfdafonjkmbpfaidpkmenggohpjo\1.1.2_0\_metadata, Quarantined, [336], [570731],1.0.6983
Adware.SearchEngineHijack, C:\Users\{username}\AppData\Local\Google\Chrome\User Data\Default\Extensions\mfeigfdafonjkmbpfaidpkmenggohpjo\1.1.2_0\icons, Quarantined, [336], [570731],1.0.6983
Adware.SearchEngineHijack, C:\Users\{username}\AppData\Local\Google\Chrome\User Data\Default\Extensions\mfeigfdafonjkmbpfaidpkmenggohpjo\1.1.2_0, Quarantined, [336], [570731],1.0.6983
Adware.SearchEngineHijack, C:\USERS\{username}\APPDATA\LOCAL\GOOGLE\CHROME\USER DATA\DEFAULT\EXTENSIONS\MFEIGFDAFONJKMBPFAIDPKMENGGOHPJO, Quarantined, [336], [570731],1.0.6983
File: 13
Adware.SearchEngineHijack, C:\USERS\{username}\APPDATA\LOCAL\GOOGLE\CHROME\USER DATA\Default\Secure Preferences, Replaced, [336], [570731],1.0.6983
Adware.SearchEngineHijack, C:\USERS\{username}\APPDATA\LOCAL\GOOGLE\CHROME\USER DATA\Default\Preferences, Replaced, [336], [570731],1.0.6983
Adware.SearchEngineHijack, C:\USERS\{username}\APPDATA\LOCAL\GOOGLE\CHROME\USER DATA\DEFAULT\EXTENSIONS\MFEIGFDAFONJKMBPFAIDPKMENGGOHPJO\1.1.2_0\MANIFEST.JSON, Quarantined, [336], [570731],1.0.6983
Adware.SearchEngineHijack, C:\Users\{username}\AppData\Local\Google\Chrome\User Data\Default\Extensions\mfeigfdafonjkmbpfaidpkmenggohpjo\1.1.2_0\icons\icon128.png, Quarantined, [336], [570731],1.0.6983
Adware.SearchEngineHijack, C:\Users\{username}\AppData\Local\Google\Chrome\User Data\Default\Extensions\mfeigfdafonjkmbpfaidpkmenggohpjo\1.1.2_0\icons\icon48.png, Quarantined, [336], [570731],1.0.6983
Adware.SearchEngineHijack, C:\Users\{username}\AppData\Local\Google\Chrome\User Data\Default\Extensions\mfeigfdafonjkmbpfaidpkmenggohpjo\1.1.2_0\_metadata\computed_hashes.json, Quarantined, [336], [570731],1.0.6983
Adware.SearchEngineHijack, C:\Users\{username}\AppData\Local\Google\Chrome\User Data\Default\Extensions\mfeigfdafonjkmbpfaidpkmenggohpjo\1.1.2_0\_metadata\verified_contents.json, Quarantined, [336], [570731],1.0.6983
Adware.SearchEngineHijack, C:\Users\{username}\AppData\Local\Google\Chrome\User Data\Default\Extensions\mfeigfdafonjkmbpfaidpkmenggohpjo\1.1.2_0\background.js, Quarantined, [336], [570731],1.0.6983
Adware.SearchEngineHijack, C:\USERS\{username}\APPDATA\LOCAL\GOOGLE\CHROME\USER DATA\Default\Web Data, Replaced, [336], [570730],1.0.6983
Adware.SearchEngineHijack, C:\USERS\{username}\APPDATA\LOCAL\GOOGLE\CHROME\USER DATA\Default\Web Data, Replaced, [336], [460701],1.0.6983
Adware.SearchEngineHijack, C:\USERS\{username}\APPDATA\LOCAL\GOOGLE\CHROME\USER DATA\Default\Web Data, Replaced, [336], [460701],1.0.6983
Adware.SearchEngineHijack, C:\USERS\{username}\APPDATA\LOCAL\GOOGLE\CHROME\USER DATA\Default\Web Data, Replaced, [336], [460701],1.0.6983
Adware.SearchEngineHijack, C:\USERS\{username}\APPDATA\LOCAL\GOOGLE\CHROME\USER DATA\Default\Web Data, Replaced, [336], [460701],1.0.6983
Physical Sector: 0
(No malicious items detected)
WMI: 0
(No malicious items detected)
(end)Traces/IOCs
You may see these entries in FRST logs:
CHR DefaultSearchURL: Default -> hxxps://searchprivacyplus.com/results.php?p=6000&v=400&q={searchTerms}&source=default
CHR DefaultSearchKeyword: Default -> Secure
CHR DefaultSuggestURL: Default -> hxxps://searchprivacyplus.com/gjson.php?q={searchTerms}
CHR Extension: (Secure) - C:\Users\{username}\AppData\Local\Google\Chrome\User Data\Default\Extensions\mfeigfdafonjkmbpfaidpkmenggohpjoChrome extensions: mfeigfdafonjkmbpfaidpkmenggohpjo dgldcllfgcheelimlbmilnkilnamlhbd ggnceihnaabghbfmifjmofepelnahpjb
Domains: searchprivacyplus.com elastisearch.com securedsearch.xyz bettersearch.co searchdimension.com





