Backdoor.Hafnium
Short bio
Backdoor.Hafnium is Malwarebytes’ detection name for malicious web shells used in the ProxyLogon attacks instigated by the Hafnium group.
Type and source of infection
Backdoor.Hafnium is a detection name for web shells on Microsoft Exchange servers. A web shell is a malicious script used by an attacker with the intent to escalate and maintain persistent access on an already compromised web application. Backdoor.Hafnium web shells were dropped by using the ProxyLogon vulnerability (CVE-2021-26855) as part of an APT attack to gather information about the organizations running the affected servers.
Business remediation
How to remove Backdoor.Hafnium with the Malwarebytes Nebula console
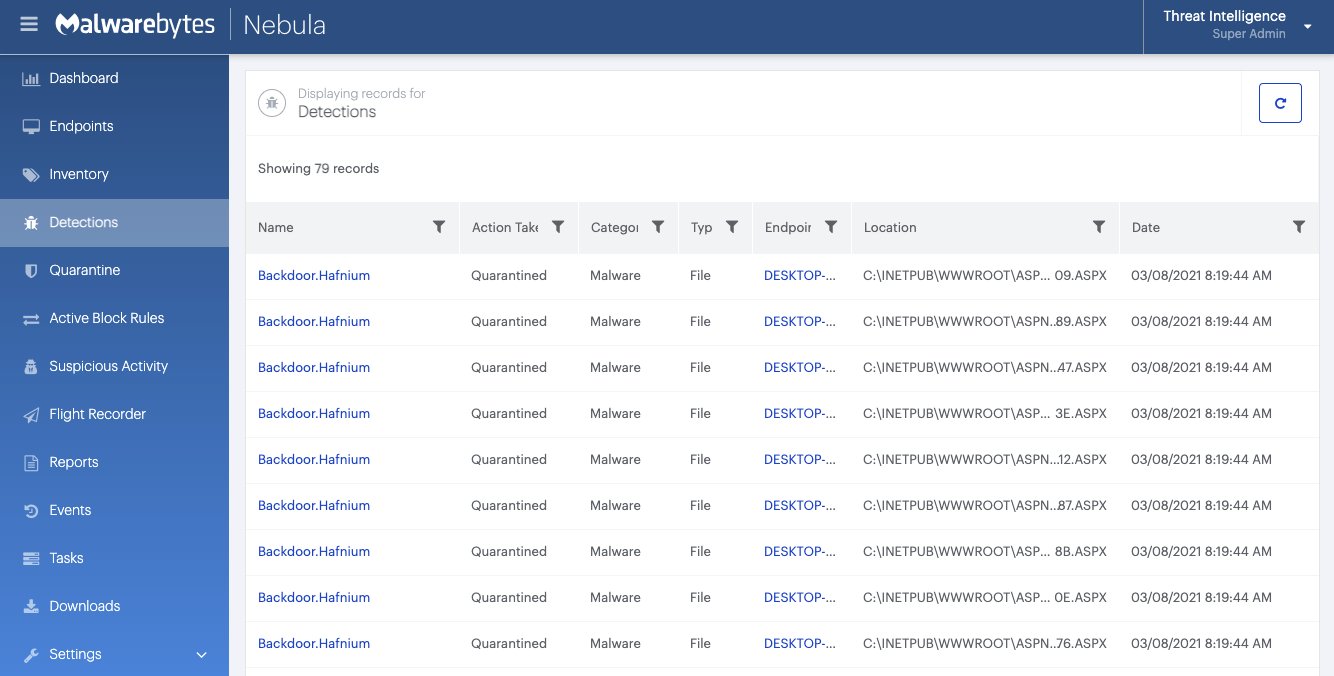
You can use the Malwarebytes Anti-Malware Nebula console to scan endpoints.

Nebula endpoint tasks menu
Choose the Scan + Quarantine option. Afterwards you can check the Detections page to see which threats were found.
On the Quarantine page you can see which threats were quarantined and restore them if necessary.