PUP.Optional.JetMedia
Short bio
PUP.Optional.JetMedia is Malwarebytes’ detection name for a potentially unwanted program (PUP) that behaves like adware and taregets Windows systems.
Symptoms
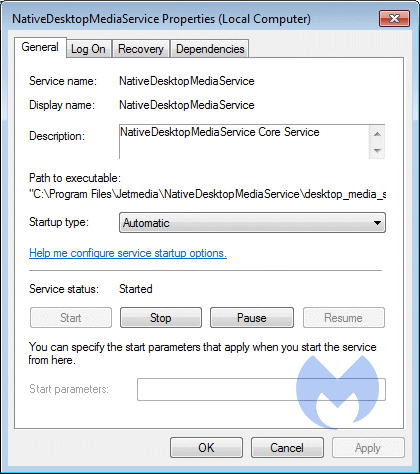
properties of JetMedia service
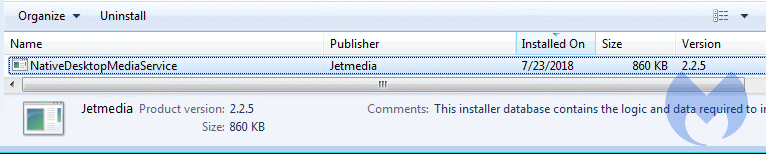
listing for JetMedia in installed Programs and Features





