PUP.Optional.WinNetSvc
Short bio
PUP.Optional.WinNetSvc is Malwarebytes’ detection name for a potentially unwanted program (PUP) that displays advertisements on affected Windows systems.
Symptoms
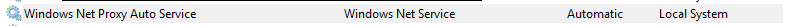
Windows Net Proxy Auto Service
with these properties:
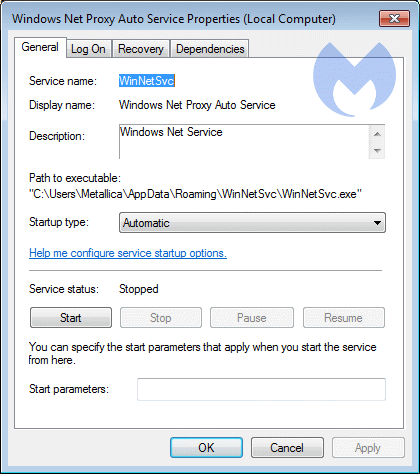
service properties





