Ransom.BSM
Short bio
Ransom.BSM is Malwarebytes” detection name for a type of ransomwarethat renames all files in available drives with the .FRSextension. Although it claims that it encrypts files, it really doesn’t; however, it removes permissions set on all files and denies anyone access to them.Below is the English section of the message it shows affected users:
Is the content of your files not readable? It is normal,because your important files have been encrypted by the “FRS Ransomware”. It means your files are NOT DAMAGED!Your files are just encrypted. From now it is not possible to use your files until they will be decrypted. The only way to decrypt your files safely is use special decryption tool “FRS Decryptor”. Please wait for “FRS Decryptor” to start automatically. If “FRS Decryptor” does not start automatically, open “FRS Decryptor” on the desktop.
It’s possible that there are various versions of this ransomware in the wild, using different addresses to where affected users can send Bitcoins to.
Protection
Malwarebytes protects users from Ransom.BSM by using Anti-Ransomware technology.
Home remediation
Malwarebytes can detect and remove Ransom.BSM without further user interaction.
- Please download Malwarebytesto your desktop.
- Double-click MBSetup.exeand follow the prompts to install the program.
- When your Malwarebytes for Windowsinstallation completes, the program opens to the Welcome to Malwarebytes screen.
- Click on the Get started button.
- Click Scan to start a Threat Scan.
- Click Quarantineto remove the found threats.
- Reboot the system if prompted to complete the removal process.
Take note, however, that removing this ransomware does not decrypt your files.Affected users can use the activation code or key below to “decrypt” your files:
T72KM-WFGWX-FRT9J-4J6C9-7WT2B
Business remediation
How to remove Ransom.BSM with the Malwarebytes Nebula console
You can use the Malwarebytes Anti-Malware Nebula console to scan endpoints.

Nebula endpoint tasks menu
Choose the Scan + Quarantine option. Afterwards you can check the Detections pageto see which threats were found.
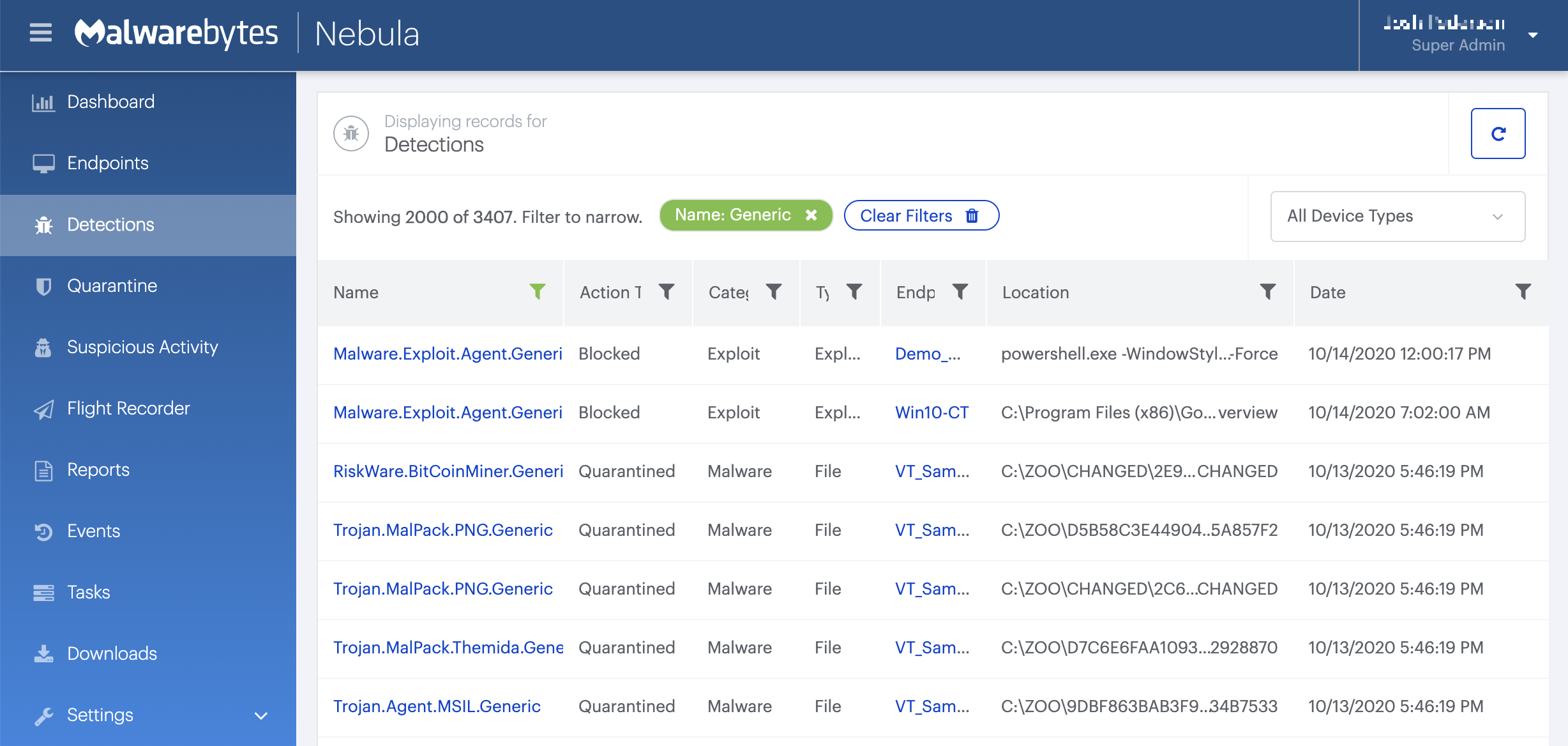
On the Quarantine pageyou can see which threats were quarantined and restore them if necessary.
Affected users can use the activation code or key below to “decrypt” their files:
T72KM-WFGWX-FRT9J-4J6C9-7WT2B





