Ransom.LockerGoga
Short bio
Ransom.LockerGoga is Malwarebytes’ detection name for a ransomware that is primarily used in targeted, and very disruptive attacks.
Symptoms
Ransom.LockerGoga encrypts files on the affected system and adds the .locked extension to the encrypted files. Ransom.LockerGoga shows a ransom note called README_LOCKED.txt

Users of affected systems may also find themselves locked out because their login credentials were changed.
Type and source of infection
Ransomware is a form of malware that locks you out of your device and/or encrypts your files, then forces you to pay a ransom to get them back. Ransom.LockerGoga is typically delivered by a targeted attack using login credentials that the threat actor somehow got hold of.
Aftermath
Besides the encrypted files of the filetypes:
.doc, .dot, .docx, .docb, .dotx, .wkb, .xlm, .xml, .xls, .xlsx, .xlt, .xltx, .xlsb, .xlw, .ppt, .pps, .pot, .ppsx, .pptx, .posx, .potx, .sldx, .pdf, .db, .sql, .cs, .ts, .js, and .py
users my find that they have been locked out of their systems because their credentials were changed by the threat actor.
Protection
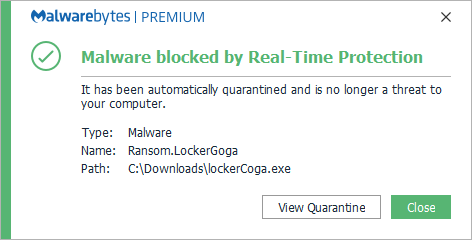
Malwarebytes blocks Ransom.LockerGoga
Business remediation
Malwarebytes can detect and remove Ransom.LockerGoga on business machines without further user interaction. To remove Ransom.LockerGoga using Malwarebytes business products, follow the instructions below.
How to remove Ransom.LockerGoga with Malwarebytes Endpoint Protection
- Go to the Malwarebytes Cloud console.
- To allow you to invoke a scan while the machine is off the network, go to Settings > Policies > your policy > General.
- Under Endpoint Interface Options, turn ON:
If you have infected machines that are not registered endpoints in Malwarebytes Endpoint Protection, you can remove Ransom.LockerGoga with our Breach Remediation tool (MBBR).
- Log into your My Account page and copy your license key. The key is needed to activate MBBR tool.
- Open your Cloud console.
- From a clean and safe machine, go to Endpoints > Add > Malwarebytes Breach Remediation. This will download the MBBR zip package.
- Unzip the package.
- Access a Windows command line prompt and issue the following commands: mbbr register –key:
mbbr update Note: You must substitute your license key for . - Copy the MBBR folder to a flash drive.
- From an infected, offline machine, copy the MBBR folder from the flash drive.
- Start a scan using the following command: mbbr scan –full –ark –remove –noreboot
- Refer to the Malwarebytes Breach Remediation Windows Administrator Guide for all supported scanning commands.
If the ransomware has encrypted some files before the behavioral detection kicked in, you can use the rollback feature (if available) to retrieve the files.
Consumer remediation
Malwarebytes can detect and remove Ransom.LockerGoga without further user interaction.
- Please download Malwarebytes to your desktop.
- Double-click MBSetup.exe and follow the prompts to install the program.
- When your Malwarebytes for Windows installation completes, the program opens to the Welcome to Malwarebytes screen.
- Click on the Get started button.
- Click Scan to start a Threat Scan.
- Click Quarantine to remove the found threats.
- Reboot the system if prompted to complete the removal process.
Take note, however, that removing this ransomware does not decrypt your files. You can only get your files back from backups you made before the infection happened.
Traces/IOCs
Mutex: MX-tgytutrc
Files: %APPDATA%\Local\Temp\tgytutrc8.exe %APPDATA%\Local\Temp\tgytutrc{4 Random Numbers}.exe
E-mail addresses used: AbbsChevis@protonmail.com AperywsQaroci@o2.pl AsuxidOruraep1999@o2.pl CottleAkela@protonmail.com CouwetIzotofo@o2.pl DharmaParrack@protonmail.com DutyuEnugev89@o2.pl IjuqodiSunovib98@o2.pl MayarChenot@protonmail.com PhanthavongsaNeveyah@protonmail.com QicifomuEjijika@o2.pl QyavauZehyco1994@o2.pl RezawyreEdipi1998@o2.pl RomanchukEyla@protonmail.com SayanWalsworth96@protonmail.com SchreiberEleonora@protonmail.com SuzuMcpherson@protonmail.com wyattpettigrew8922555@mail.com





