Ransom.Mespinoza
Short bio

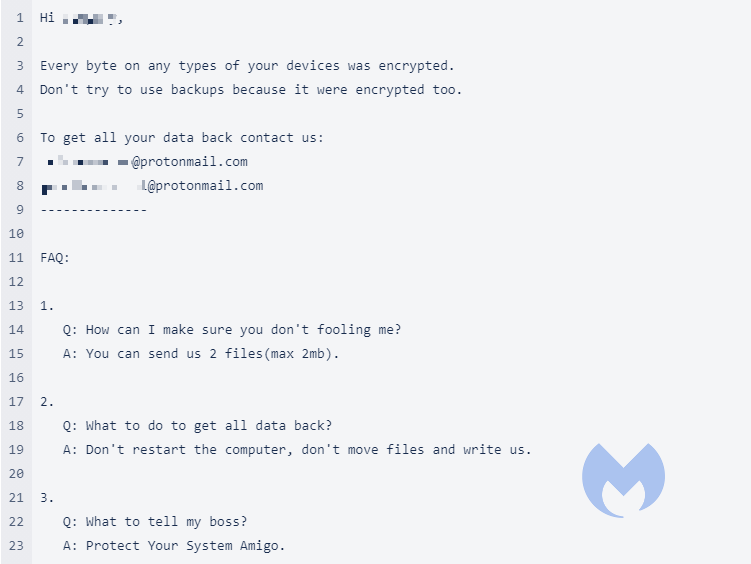
PYSA is short for Protect – Your – Systems – Amigo
Symptoms
Victims will find the ransom note called Readme.README
Type and source of infection
Ransom.Mespinoza is ransomware. Ransomware in general makes files on the victims system unusable until the ransom is payed. Ransom.Mespinoza is believed to be spread using RDP brute force attacks. Once a network is breached it uses tools like mimikatz and psexec for lateral movement.
Protection
Malwarebytes protects business and home users from Ransom.Mespinoza by using Anti-Ransomware technology and real-time protection.

Home remediation
Malwarebytes can detect and remove Ransom.Mespinoza without further user interaction.
- Please download Malwarebytes to your desktop.
- Double-click MBSetup.exe and follow the prompts to install the program.
- When your Malwarebytes for Windows installation completes, the program opens to the Welcome to Malwarebytes screen.
- Click on the Get started button.
- Click Scan to start a Threat Scan.
- Click Quarantine to remove the found threats.
- Reboot the system if prompted to complete the removal process.
Take note, however, that removing this ransomware does not decrypt your files. You can only get your files back from backups you made before the infection happened.
Business remediation
How to remove Ransom.Mespinoza with the Malwarebytes Nebula console
You can use the Malwarebytes Anti-Malware Nebula console to scan endpoints.

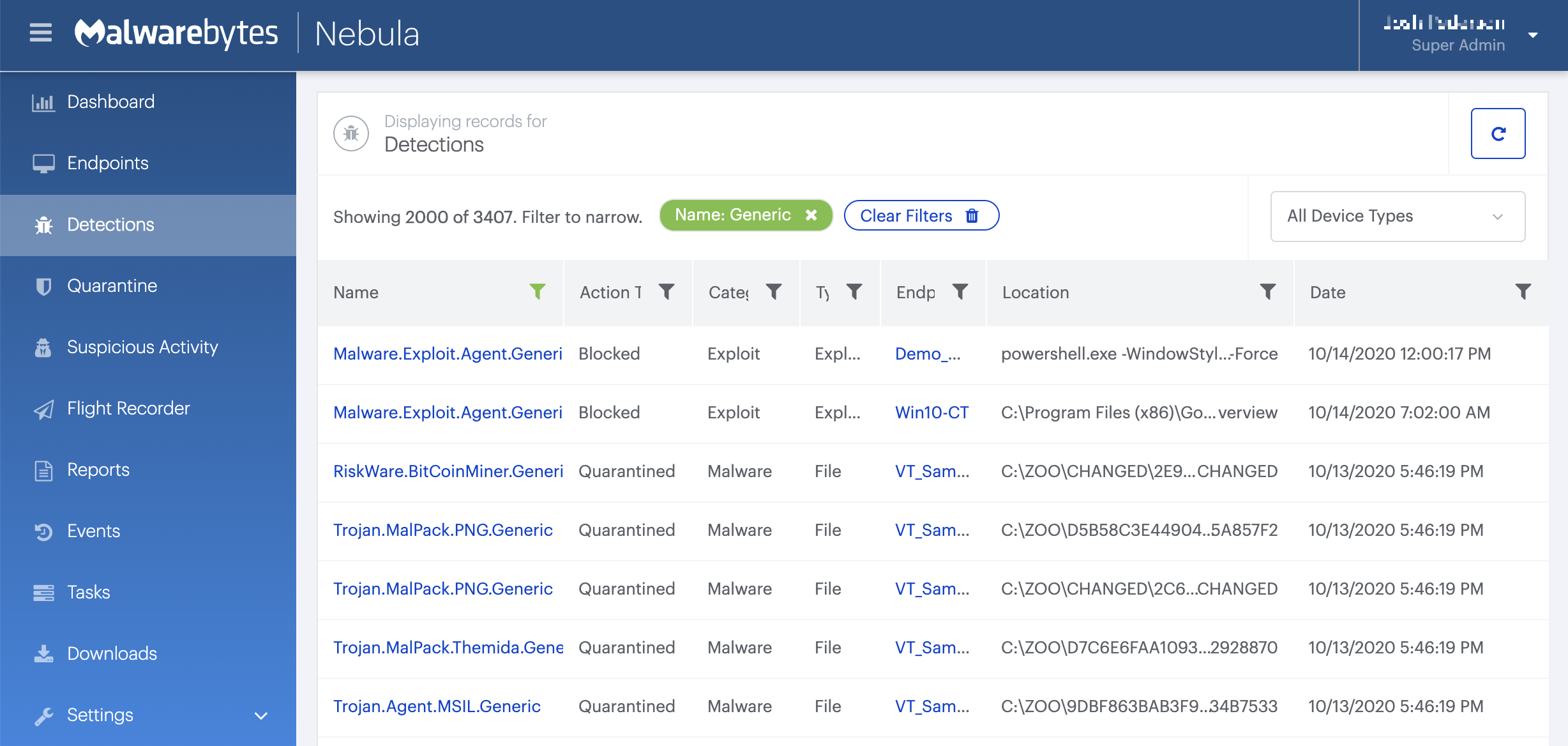
Nebula endpoint tasks menu
Choose the Scan + Quarantine option. Afterwards you can check the Detections page to see which threats were found.
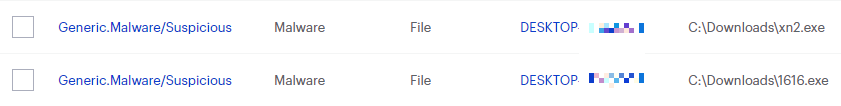
On the Quarantine page you can see which threats were quarantined and restore them if necessary.
All component/technology detections are passed to the remediation engine for complete removal from infected systems. This industry leading technology uses patented techniques in identifying all cohorts or associated files for a single threat and removes them all together to prevent malware from resuscitating itself. If you are using Malwarebytes Ransomware Rollback technology, it allows you to wind back the clock to negate the impact of ransomware by leveraging just-in-time backups.
Traces/IOCs
-
7fd3000a3afbf077589c300f90b59864ec1fb716feba8e288ed87291c8fdf7c3
-
e4287e9708a73ce6a9b7a3e7c72462b01f7cc3c595d972cf2984185ac1a3a4a8
-
327934c4c11ba37f42a91e1b7b956d5a4511f918e63047a8c4aa081fd39de6d9





