While leaving your back door open while you are working from home may be something you do without giving it a second thought, having unnecessary ports open on your computer is a security risk that is sometimes underestimated. That’s because an open port can be subject to brute force attacks.
What are brute force attacks?
A brute force attack is where an attacker tries every way he can think of to get in. Including throwing the kitchen sink at it. In cases where the method they are trying is to get logged in to your system, they will try endless combinations of usernames and passwords until a combination works.
Brute force attacks are usually automated, so it doesn’t cost the attacker a lot of time or energy. Certainly not as much as individually trying to figure out how to access a remote system. Based on a port number or another system specific property, the attacker picks the target and the method and then sets his brute force application in motion. He can then move on to the next target and will get notified when one of the systems has swallowed the hook.
Brute force methods
When trying to gain access to a remote system, an attacker will use one of these different types of attacks:
- Reverse brute force attack. This type uses a common password or collection of passwords against many possible usernames. Sometimes the attacker may have an idea about the username or a part thereof. For example, they may know that a specific organization uses {first name}@{organization} as the default username for their employees. The attacker can then try a specific list of usernames and random passwords.
- Credential stuffing is a type of attack where the criminal has a database of valid username and password combinations (usually stolen from other breaches) and tries out all these combinations on different systems. This is why it is never a good idea to reuse your passwords.
- A hybrid brute force attack starts with the most feasible combinations and then keeps on trying from there. It often uses a dictionary attack where the application tries usernames or passwords using a dictionary of possible strings or phrases.
- Rainbow table attacks only work when the attacker has some knowledge about the password they are trying to guess. In these attacks rainbow tables are used to recover a password based on its hash value. A rainbow table is a hash function used in cryptography for storing important data such as passwords in a database.
Brute forcing RDP ports
RDP attacks are one of the main entry points when it comes to targeted ransomware operations. To increase effectiveness, ransomware attacks are getting more targeted and one of the primary attack vectors is the Remote Desktop Protocol (RDP). Remote desktop is exactly what the name implies, an option to remotely control a computer system. It almost feels as if you were actually sitting behind that computer. Which is exactly what makes an attacker with RDP access so dangerous.
Because of the current pandemic, many people are working from home and may be doing so for a while to come. Working from home has the side effect of more RDP ports being opened. Not only to enable the workforce to access company resources from home, but also to enable IT staff to troubleshoot problems on the workers’ devices. A lot of enterprises rely on tech support teams using RDP to troubleshoot problems on employee’s systems.
But ransomware, although prevalent, is not the only reason for these types of attacks. Cybercriminals can also install keyloggers or other spyware on target systems to learn more about the organization they have breached. Other possible objectives might be data theft, espionage, or extortion.
Protect against brute force attacks
We’ve posted recommendations to protect against RDP attacks before. You can read more details in that post but basically the protection measures come down to:
- Limit the number of open ports
- Restrict the access to those that need it
- Enhance security of the port and the protocol
The same basic security measures apply to other ports. In cybersecurity, the term open port refers to a TCP or UDP port number that is configured to accept packets. In contrast, a port which rejects connections or ignores all packets, is a closed port. The less open ports you have facing the internet, the safer it is. Limiting the number of open ports is a good start but closing all of them is almost never feasible.
For the ports that need to remain open and where you do expect visitors, it’s a good idea to disable legacy usernames, rotate passwords, and use 2FA if you can.
Security software guarding the entire network should raise alarm bells when a great number of attempts are detected. Anything that behaves like a brute force attack will look so different from normal login attempts that it shouldn’t be a problem if it is blocked. When a brute force attacker gets locked out for a few minutes after a few failed attempts, this will slow them down a lot and give you ample opportunity to take corrective and defensive measures.
It’s a numbers game
Many open ports can be used in a brute force attack, but RDP ports are the most desirable for anyone trying to gain access. RDP is easier because the attacker may have a reasonable idea about the username and only needs to brute force the password. It also offers a successful attacker a good chance to infiltrate the organization’s network further.
As mentioned earlier, the shift to working from home has caused a big raise in the number of open RDP ports around the globe. The number of RDP ports exposed to the Internet grew from about three million in January 2020 to over four and a half million in March. At Malwarebytes we noticed a similar surge in compromised servers that are used to run brute force tools or scan the Internet for vulnerable ports. Malwarebytes protects its customers by blocking the traffic from these IP addresses.
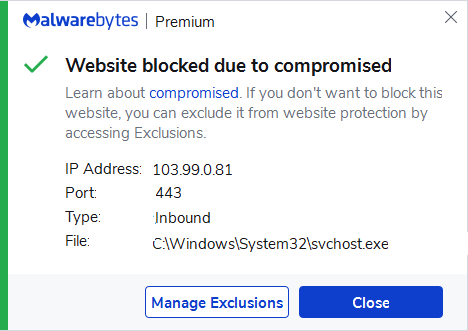
And please don’t think this can’t happen to your organization. We’ve seen high profile companies fall victim to ransomware where the suspected point of entry was an open RDP port.
Stay safe everyone!











