Ransom.RobbinHood
Short bio
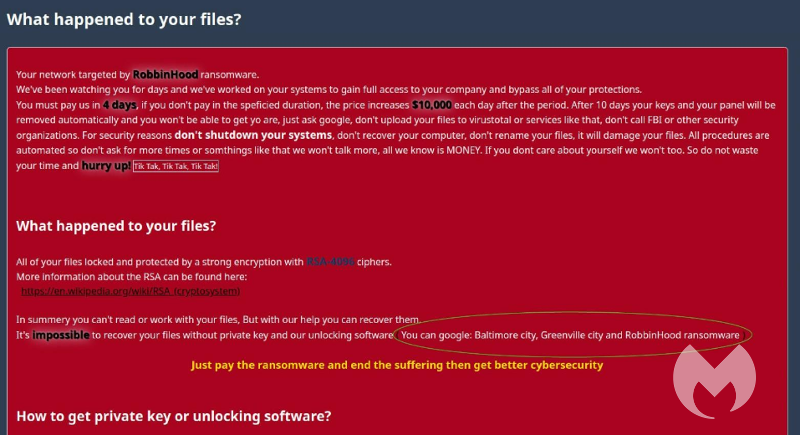
Ransom.RobbinHood ransom note
Type and source of infection
Ransomware is a category of malware that holds files or systems hostage for ransom. When encrypting files, an AES key is created for each file. The ransomware will then encrypt the AES key and the original filename with the public RSA encryption key and append it to the encrypted file. Ransom.RobbinHood is used in targeted attacks, where the threat actors make sure that essential files are encrypted so they can ask for large ransom amounts. Ransom.RobbinHood has been know to use a digitally signed driver and exploit a vulnerability in this legitimate driver to gain kernel access.
Aftermath
Because of the targeted nature of this ransomware, it is advised to do a full network scan to find any backdoors or other tools that the threat actors may have left behind, and which may enable them to regain access to the network.
Protection
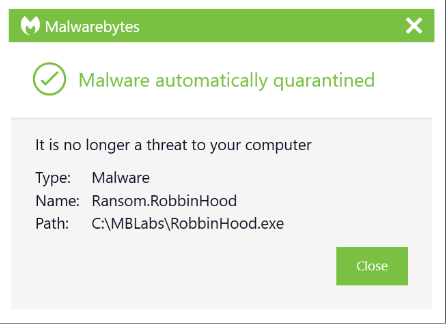
Malwarebytes Real-time protection blocks Ransom.RobbinHood
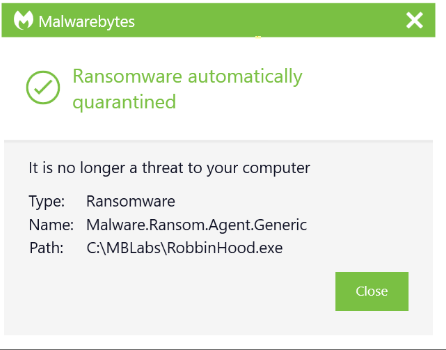
Malwarebytes Anti-Ransomware recognizes and stops ransomware behavior.





