Rogue.RegistrySmart
Short bio
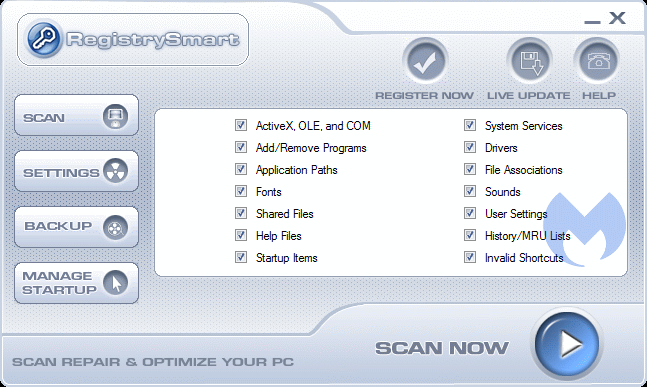
GUI RegistrySmart
Symptoms

Rogue.RegistrySmart Scheduled Task
Users of affected machine may have seen these warnings during install:
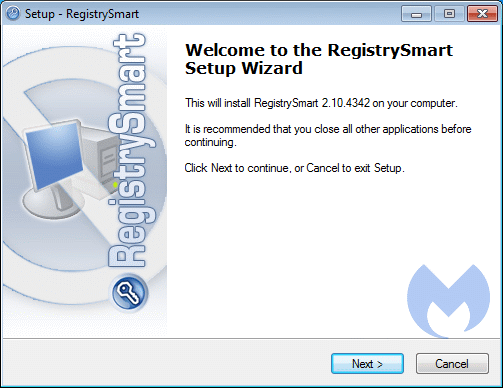
Rogue.RegistrySmart installer
and may see this entry in their list of installed Programs and Features:
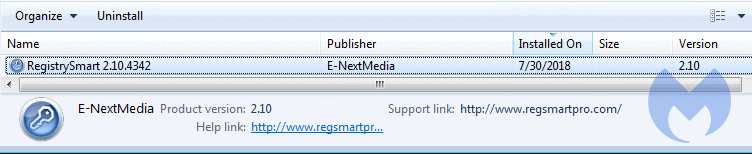
and this warning after a scan with the rogue scanner:
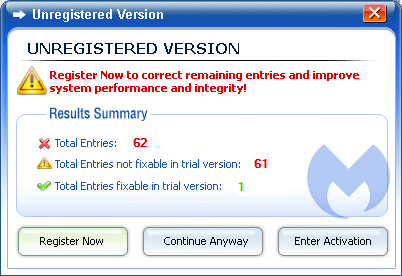
Rogue.RegistrySmart scanresults
Type and source of infection
Rogue.RegistrySmart is a typical rogue that produces false positives in an attempt to convince users they need to buy the software. It is often installed by Trojans or bundlers.
Protection
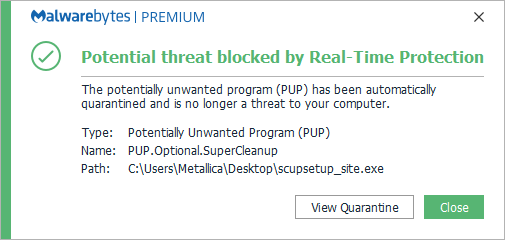
Malwarebytes blocks Rogue.RegistrySmart
Remediation
Malwarebytes can detect and remove Rogue.RegistrySmart without further user interaction.
- Please download Malwarebytes to your desktop.
- Double-click MBSetup.exe and follow the prompts to install the program.
- When your Malwarebytes for Windows installation completes, the program opens to the Welcome to Malwarebytes screen.
- Click on the Get started button.
- Click Scan to start a Threat Scan.
- Click Quarantine to remove the found threats.
- Reboot the system if prompted to complete the removal process.
Malwarebytes removal log
A Malwarebytes log of removal will look similar to this:
Malwarebytes
www.malwarebytes.com
-Log Details-
Scan Date: 7/30/18
Scan Time: 11:59 AM
Log File: 34ec19fe-93df-11e8-add8-00ffdcc6fdfc.json
Administrator: Yes
-Software Information-
Version: 3.5.1.2522
Components Version: 1.0.374
Update Package Version: 1.0.6123
License: Premium
-System Information-
OS: Windows 7 Service Pack 1
CPU: x64
File System: NTFS
User: {computername}\{username}
-Scan Summary-
Scan Type: Threat Scan
Scan Initiated By: Manual
Result: Completed
Objects Scanned: 251110
Threats Detected: 29
Threats Quarantined: 29
Time Elapsed: 3 min, 29 sec
-Scan Options-
Memory: Enabled
Startup: Enabled
Filesystem: Enabled
Archives: Enabled
Rootkits: Enabled
Heuristics: Enabled
PUP: Detect
PUM: Detect
-Scan Details-
Process: 1
Rogue.RegistrySmart, C:\Program Files (x86)\RegistrySmart\RegistrySmart.exe, Quarantined, [1364], [171220],1.0.6123
Module: 1
Rogue.RegistrySmart, C:\Program Files (x86)\RegistrySmart\RegistrySmart.exe, Quarantined, [1364], [171220],1.0.6123
Registry Key: 6
Rogue.RegistrySmart, HKLM\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\SCHEDULE\TASKCACHE\TREE\RegistrySmart Scheduled Scan, Quarantined, [1364], [171220],1.0.6123
Rogue.RegistrySmart, HKLM\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\SCHEDULE\TASKCACHE\TASKS\{17BA9627-AFC4-4A8A-A2AE-E0331FA6372D}, Quarantined, [1364], [171220],1.0.6123
Rogue.RegistrySmart, HKLM\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\SCHEDULE\TASKCACHE\PLAIN\{17BA9627-AFC4-4A8A-A2AE-E0331FA6372D}, Quarantined, [1364], [171220],1.0.6123
Rogue.RegistrySmart, HKLM\SOFTWARE\WOW6432NODE\MICROSOFT\WINDOWS\CURRENTVERSION\UNINSTALL\RegistrySmart_is1, Quarantined, [1364], [171220],1.0.6123
Rogue.RegistrySmart, HKLM\SOFTWARE\WOW6432NODE\RegistrySmart, Quarantined, [1364], [212840],1.0.6123
Rogue.RegistrySmart, HKCU\SOFTWARE\RegistrySmart, Quarantined, [1364], [210497],1.0.6123
Registry Value: 0
(No malicious items detected)
Registry Data: 0
(No malicious items detected)
Data Stream: 0
(No malicious items detected)
Folder: 4
Rogue.RegistrySmart, C:\Users\{username}\AppData\Roaming\RegistrySmart\Log, Quarantined, [1364], [170329],1.0.6123
Rogue.RegistrySmart, C:\USERS\{username}\APPDATA\ROAMING\REGISTRYSMART, Quarantined, [1364], [170329],1.0.6123
Rogue.RegistrySmart, C:\PROGRAM FILES (X86)\REGISTRYSMART, Quarantined, [1364], [171220],1.0.6123
Rogue.RegistrySmart, C:\PROGRAMDATA\MICROSOFT\WINDOWS\START MENU\PROGRAMS\REGISTRYSMART, Quarantined, [1364], [171858],1.0.6123
File: 17
Rogue.RegistrySmart, C:\USERS\{username}\APPDATA\ROAMING\Microsoft\Windows\Recent\RegistrySmart - Changes.txt.lnk, Quarantined, [1364], [199824],1.0.6123
Rogue.RegistrySmart, C:\USERS\{username}\DESKTOP\RegistrySmart - Changes.txt, Quarantined, [1364], [199824],1.0.6123
Rogue.RegistrySmart, C:\USERS\{username}\DESKTOP\RegistrySmart.exe, Quarantined, [1364], [199824],1.0.6123
Rogue.RegistrySmart, C:\USERS\{username}\DESKTOP\RegistrySmart.lnk, Quarantined, [1364], [199824],1.0.6123
Rogue.RegistrySmart, C:\Users\{username}\AppData\Roaming\RegistrySmart\Log\2018 Jul 30 - 11_52_27 AM_094.log, Quarantined, [1364], [170329],1.0.6123
Rogue.RegistrySmart, C:\Program Files (x86)\RegistrySmart\DataBase.ref, Quarantined, [1364], [171220],1.0.6123
Rogue.RegistrySmart, C:\Program Files (x86)\RegistrySmart\license.rtf, Quarantined, [1364], [171220],1.0.6123
Rogue.RegistrySmart, C:\Program Files (x86)\RegistrySmart\RegistrySmart.exe, Quarantined, [1364], [171220],1.0.6123
Rogue.RegistrySmart, C:\Program Files (x86)\RegistrySmart\RegistrySmart.url, Quarantined, [1364], [171220],1.0.6123
Rogue.RegistrySmart, C:\Program Files (x86)\RegistrySmart\unins000.dat, Quarantined, [1364], [171220],1.0.6123
Rogue.RegistrySmart, C:\Program Files (x86)\RegistrySmart\unins000.exe, Quarantined, [1364], [171220],1.0.6123
Rogue.RegistrySmart, C:\WINDOWS\SYSTEM32\TASKS\RegistrySmart Scheduled Scan, Quarantined, [1364], [171220],1.0.6123
Rogue.RegistrySmart, C:\USERS\{username}\APPDATA\ROAMING\Microsoft\Internet Explorer\Quick Launch\RegistrySmart.lnk, Quarantined, [1364], [171220],1.0.6123
Rogue.RegistrySmart, C:\WINDOWS\TASKS\RegistrySmart Scheduled Scan.job, Quarantined, [1364], [207855],1.0.6123
Rogue.RegistrySmart, C:\ProgramData\Microsoft\Windows\Start Menu\Programs\RegistrySmart\RegistrySmart on the Web.lnk, Quarantined, [1364], [171858],1.0.6123
Rogue.RegistrySmart, C:\ProgramData\Microsoft\Windows\Start Menu\Programs\RegistrySmart\RegistrySmart.lnk, Quarantined, [1364], [171858],1.0.6123
Rogue.RegistrySmart, C:\ProgramData\Microsoft\Windows\Start Menu\Programs\RegistrySmart\Uninstall RegistrySmart.lnk, Quarantined, [1364], [171858],1.0.6123
Physical Sector: 0
(No malicious items detected)
WMI: 0
(No malicious items detected)
(end)Add an exclusion
Should users wish to keep this program and exclude it from being detected in future scans, they can add the program to the exclusions list. Here’s how to do it.
- Open Malwarebytes for Windows.
- Click the Detection History
- Click the Allow List
- To add an item to the Allow List, click Add.
- Select the exclusion type Allow a file or folder and use the Select a folder button to select the main folder for the software that you wish to keep.
- Repeat this for any secondary files or folder(s) that belong to the software.
If you want to allow the program to connect to the Internet, for example to fetch updates, also add an exclusion of the type Allow an application to connect to the internet and use the Browse button to select the file you wish to grant access.
Traces/IOCs
You may see these entries in FRST logs:
(E-NextMedia) C:\Program Files (x86)\RegistrySmart\RegistrySmart.exe
C:\Windows\System32\Tasks\RegistrySmart Scheduled Scan
C:\Users\{username}\Desktop\RegistrySmart.lnk
C:\Windows\Tasks\RegistrySmart Scheduled Scan.job
C:\Users\{username}\AppData\Roaming\RegistrySmart
C:\ProgramData\Microsoft\Windows\Start Menu\Programs\RegistrySmart
C:\Program Files (x86)\RegistrySmart
RegistrySmart 2.10.4342 (HKLM-x32\...\RegistrySmart_is1) (Version: 2.10 - E-NextMedia)
Task: {17BA9627-AFC4-4A8A-A2AE-E0331FA6372D} - System32\Tasks\RegistrySmart Scheduled Scan => C:\Program Files (x86)\RegistrySmart\RegistrySmart.exe [2011-11-11] (E-NextMedia)
Task: C:\Windows\Tasks\RegistrySmart Scheduled Scan.job => C:\Program Files (x86)\RegistrySmart\RegistrySmart.exe
scheduled C:\Program Files (x86)\RegistrySmart {username}.Run




