Worm.PasswordStealer
Short bio
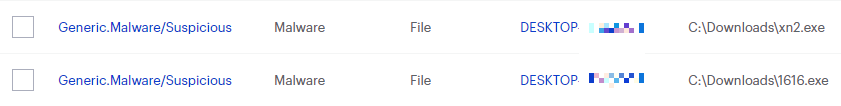
Worm.PasswordStealer is Malwarebytes’ generic detection name for applications that may run in the background and silently collect information about the system, connected users, and network activity. Worm.PasswordStealer may attempt to steal stored credentials, usernames and passwords and other personal and confidential information. This information may be transmitted to a destination specified by the author. Worm.PasswordStealer may allow an attacker to install additional software to the infected machine, or may direct the infected machine to participate in a malicious botnet for the purposes of sending spam or other malicious activities.
Symptoms
Worm.PasswordStealer may run silently in the background and may not provide any indication of infection to the user. Worm.PasswordStealer may also disable Antivirus programs and other Microsoft Windows security features.
Type and source of infection
Worm.PasswordStealer may be distributed using various methods. This software may be packaged with free online software, or could be disguised as a harmless program and distributed by email. Alternatively, this software may be installed by websites using software vulnerabilities. Infections that occur in this manner are usually silent and happen without user knowledge or consent.
Protection
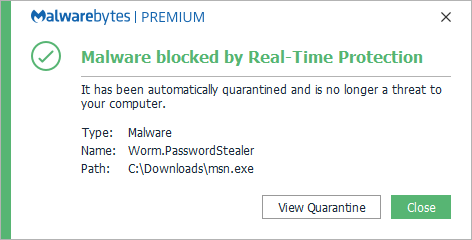
Malwarebytes blocks Worm.PasswordStealer
Home remediation
Malwarebytes can detect and remove many Worm.PasswordStealer infections without further user interaction.
- Please download Malwarebytesto your desktop.
- Double-click MBSetup.exeand follow the prompts to install the program.
- When your Malwarebytes for Windowsinstallation completes, the program opens to the Welcome to Malwarebytes screen.
- Click on the Get started button.
- Click Scan to start a Threat Scan.
- Click Quarantineto remove the found threats.
- Reboot the system if prompted to complete the removal process.
Business remediation
How to remove Worm.PasswordStealer with the Malwarebytes Nebula console
You can use the Malwarebytes Anti-Malware Nebula console to scan endpoints.

Nebula endpoint tasks menu
Choose the Scan + Quarantine option. Afterwards you can check the Detections pageto see which threats were found.
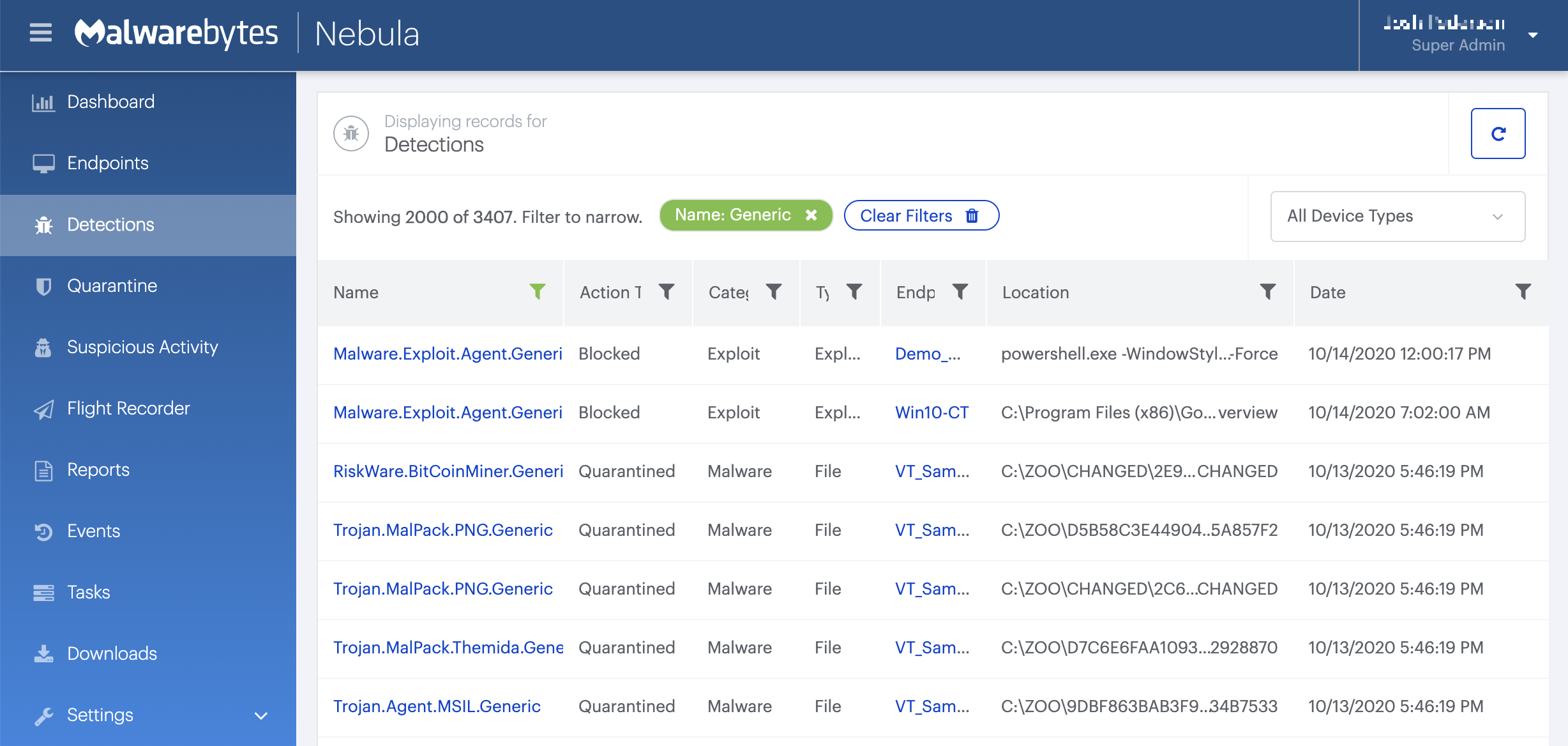
On the Quarantine pageyou can see which threats were quarantined and restore them if necessary.