In this post I will explain UEFI (Unified Extensible Firmware Interface) and its predecessor, the BIOS/MBR, as well as the challenges to get a dual boot environment with an alternative operating system, such as Linux.
The Master Boot Record
To really understand what the whole fuss is about, you have to realize that until UEFI was proposed, computers relied on a rather archaic system called “MBR”, that stands for Master Boot Record, working in tandem with the BIOS to achieve the bootstrap process, that is the initialization of a computer.
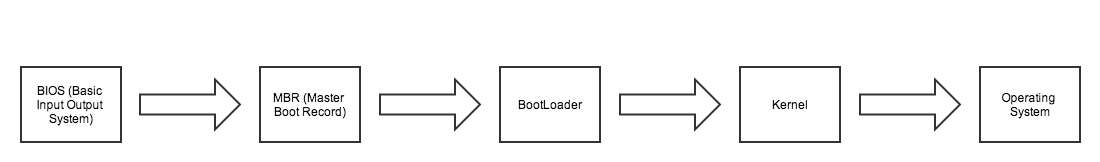
A bios and MBR bootstrap process.
The Master Boot Record contains information on how the disk is partitioned, it is located at the very beginning of the disk, and the MBR isn’t typically accessible by the operating system. It is the one of the first thing accessed, making it ideal for malicious stuff to hide in.
In the early days of MSDOS, the Master Boot Record was plagued with virii. Infected MBR’s of floppies disks were one of the original way computers were infected.
As a result, restrictions to accessing the MBR were implemented. Some of these were through the BIOS, some through advances in Antivirus software, and some through more stringent Operating System controls. All of these mitigations had appeared to have relegated MBR threats to the dustbin.
But old threat vectors die hard, and a few years ago we saw a resurgence of MBR threats. Rootkits were taking advantage of the MBR and placing themselves ahead of the operating system. By subverting the MBR, these threats made themselves essentially invisible. (If the Rootkit is loaded before the Operating System, It has a definite advantage.)
Add to this some legacy limitations inherent to the BIOS/MBR system, users complaining of sluggish boot times, and you can see why it was time to find some other way.
Enter UEFI, the Unified Extensible Firmware Interface
UEFI, the evolution of EFI, replaces both the BIOS and does away with the MBR all together, with the GPT (Guid Partition Table). It introduces a wealth of new features, better support for large disks, the possibility of having a mini operating system to troubleshoot a broken main one, and dramatically improved bootup speeds.
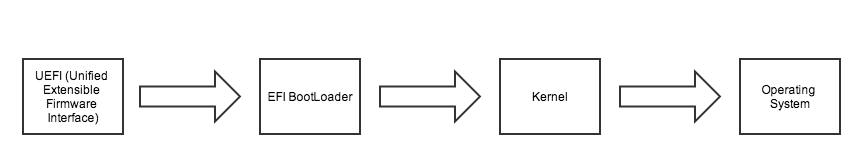
A UEFI bootstrap process.
While this method has many benefits, it made Dual Boot configurations very difficult, essentially making running any other Operating System a complicated proposition. It also made many diagnostic tools, such as the ones based on live CD’s ineffective.
And so for a period, dual booting in UEFI just was so esoterically complex, that running in legacy mode, by disabling features of UEFI was the easier way to dual boot. This was provided you could even disable these settings, as some more “budget minded” hardware manufacturers did not include this option.
Enter Secure Boot.
Later versions of UEFI introduced a concept called “Secure Boot”
“Secure Boot is a security standard developed by members of the PC industry to help make sure that your PC boots using only software that is trusted by the PC manufacturer.”
This additional feature, introduced by members of the PC industry, and more widely adopted by Microsoft for Windows 8 PC’s, threatened to make running anything other than an “authorized” Operating system impossible! While in the PC world this would be an anathema, if you look at tablets and mobiles, it’s not that uncommon of a practice. iPhones are locked, most android handsets are locked also, tablets as well, as are most game consoles…
Microsoft elaborated on this new feature here.
So where does this leave the enthusiast and tinkerers at?
Luckily for us, the dust settled. The linux foundation announced efforts to address UEFI and Secure Boot issues, Live cd’s started offering the option to boot in UEFI mode, major Linux Distributions, such as Suse, Fedora, Ubuntu, and the Unix like FreeBSD operating system as well followed suite. Most of the hardware manufacturers started including the option to disable Secure Boot, and howto’s sprung on many forums explaining what needed to be done in a step by step manner.
Many enthusiasts still think that Secure Boot was an underhanded attempt at locking out older Microsoft Operating Systems, or alternatives, such as Linux.
While this new way of doing things has certainly added a layer of complexity to Dual booting, UEFI is still a worthy and long overdue upgrade.










