We wrote about the adult site xtube.com being compromised, redirecting visitors to a landing page for the Neutrino Exploit kit last week on the Malwarebytes Unpacked blog,
The malware that dropped from the exploit was found here and was called xtube.exe.
This file was a .NET assembly, which was cleaned up using de4dot, a popular .NET deobfuscator.
Using ILspy, one of the many .NET decompilers, source code for the cleaned assembly can be viewed.
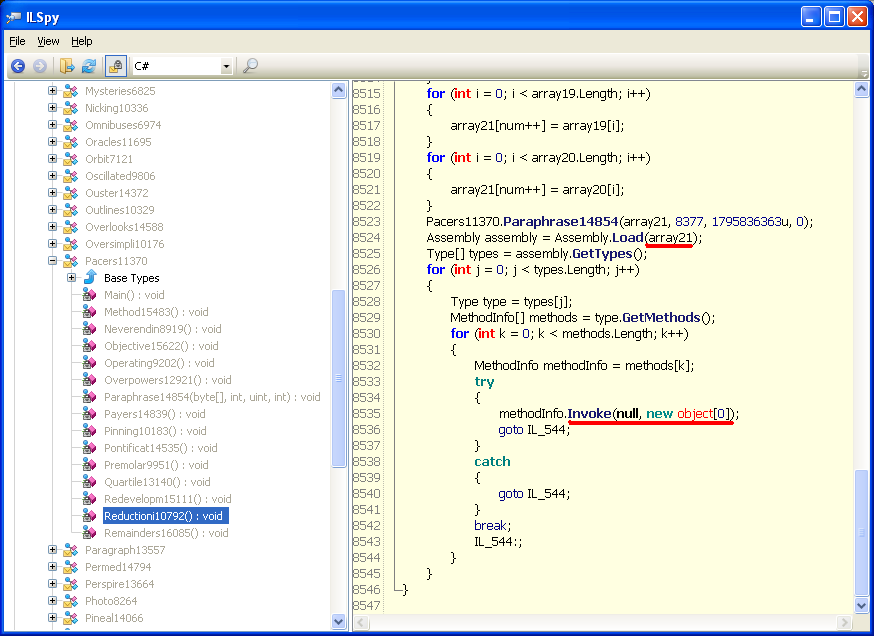
Several arrays are visible, with one of them (array21) containing another small .NET assembly. The assembly itself is deobfuscated with the call Pacers11370.Paraphrase14854 and then loading using Assembly.Load. Afterward, the main procedure is located and executed.
We extracted the loader from array21 and took another look at it using ILspy.
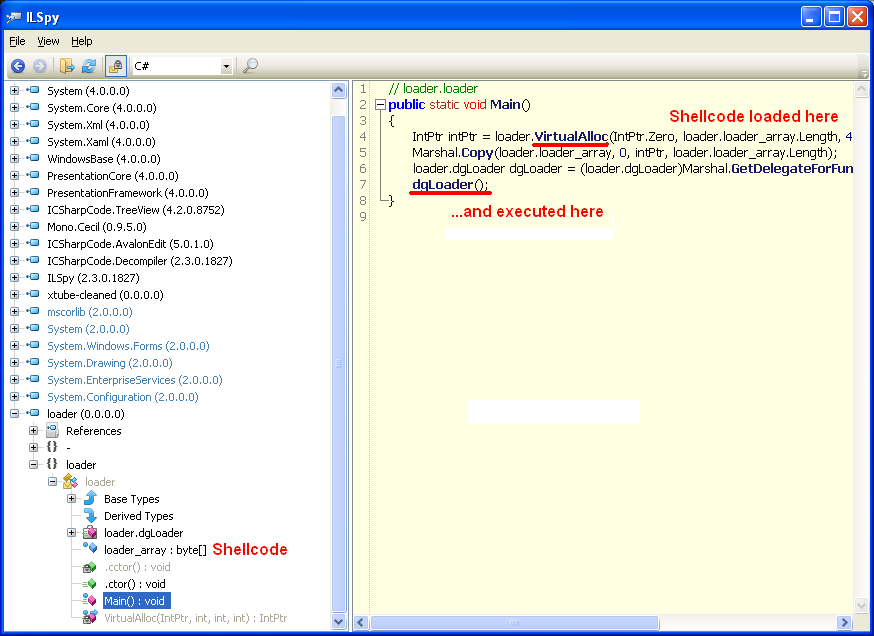
In order to run the shellcode properly, it was added as a PE section along with xtube.exe and then executed (thanks to @hasherezade for assisting on this). The shellcode looks for a byte pattern in xtube.exe: 87 81 62 4E 2E 45 A3 7F 6D DC 45 51 15 13 34 F4 0F 9E 3D 0E and begins to deobfuscate another binary, which turns out to be Cryptowall 3.0 (md5: 372c14f9fe472e5a4175f0f9ffc8aecc). Cryptowall is another Cryptovirus that was born from the success of Cryptolocker.
To unpack fully, Cryptowall runs explorer.exe process, then svchost.exe, which is hollowed out and resumed. This is a common practice seen in malware.
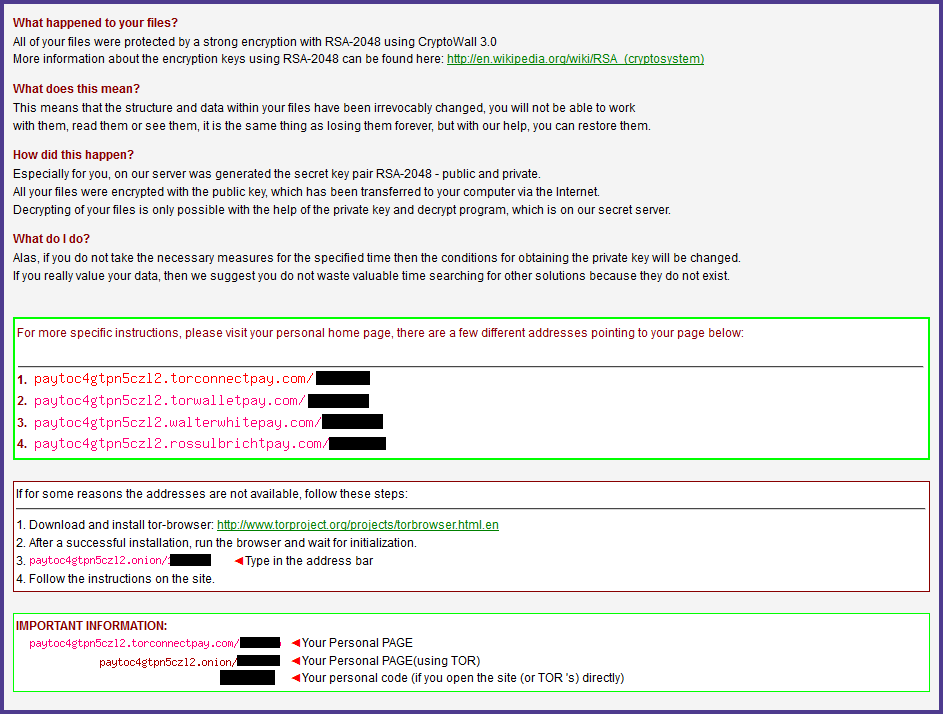
All user files are encrypted using “RSA-2048” encryption. In order to pay the ransom, victims are instructed to visit paytoc4gtpn5cz12.torconnectpay.com. A separate address is also provided over the tor network.
It’s always good to remember that highly ranked websites (including adult content) are a prime target for hackers due to the traffic they get.
Malwarebytes Anti-Malware protects users against this Cryptowall variant and other by detecting it as Trojan.Ransom.ED. Also, Malwarebytes Anti-Exploit users were also protected from the exploiting leading to infection.










