Security Level: High / Hardcore
Purpose: To hide who you are while performing research through your browser AND protecting your host system from drive-by download attacks AND being able to perform dynamic malware analysis and capture malicious traffic moving between the malware and the C&C. (Whew, that’s a lot of ANDs. =D)
Benefits:
- Hide your IP
- Protect the host system by running in a virtual environment
- Execute malware in a safe environment /w traffic capture
- One time setup, no Windows VPN necessary
- Ability to revert to snapshots, restart the system without losing anonymity.
Drawbacks:
- It’s downright difficult to set up if not familiar with the technology
- Need more things to start with than previous solutions.
- Requires occasional VPN re-initialization / DHCP re-connection
What you’ll need:
- VMWare Player – https://www.vmware.com/products/player/
- JanusVM – http://janusvm.com/
- Another Virtualization Application (Vmware / VirtualBox / etc.)
- An operating system to run on said virtualization application
- Note: If you are already a malware researcher, chances are you are already running some kind of virtual environment for analysis, etc.
- A Linux virtual environment
- Your Linux system will need the following utilities:
- Net-tools
- IPTables
- Dnsmasq
- Note: You can use whatever you want but in this tutorial I use a specific VMware image of Mint Linux, it is available free here:
- Your Linux system will need the following utilities:
Situation:
Your research has paid off, you got your hands on some new and exciting malware samples which could be the connection between two criminal organizations, and you think the traffic might give away some clues into who built this malware. You could send it to an online analysis service but you don’t want it leaked to anyone just yet. You want to maintain your anonymity so you execute the malware while connected to the VPN in Windows, you set up two instances of Wireshark, one on the inside VM and one on the outside connection on your host system.
You execute the malware and it immediately restarts the system. Drat. When the system comes back up, even though you have configured your VPN to start automatically, it takes a little while to connect, you know that this malware checks for a connection at startup and if it can’t find one, it won’t beacon. You decide that maybe the outside Wireshark caught something before the system restarted, only to discover that all you captured was encrypted VPN traffic! Oh noes!
What are we doing?
We are going to connect to the Janus VPN via our Linux image, which is also working as a DHCP server that the Windows analysis system automatically connects to. To top it all off all three are on the same private network with the only outside access only being available to one of JanusVM’s interfaces. This means that there is no possible way that any traffic can get out of your analysis VM without first being masked, encrypted and redirected.
How:
- Download and set up JanusVM (see the previous section)
- Set up your Windows Analysis VM
- Download a Linux Image or ISO file and install Linux in VMware Player (If you haven’t already)
- It is recommended to use the Linux Mint Image referenced above, it comes pre-installed with VMware Tools
- Download and install all the utilities listed above.
- Set the Windows VM to use VMnet3 in its network interface settings and ensure DHCP is running on the interface. Set your Linux VM to use vmnet3 as well.
- VMnet3 is one of the private networks used by VMware. There are multiple other types of VMnet networks available but I recommend VMnet3.
- If you aren’t using VMware for your analysis platform, set both the Linux and JanusVM to NAT so that you could connect with a different virtual environment application.
- If you are using VirtualBox, make sure the JanusVM isn’t bridged to the VirtualBox interface.
- Set the JanusVM NAT connection to VMnet3 and restart to gain a new IP.
- The same way you would modify the network interface settings for a normal VM.
- Set the Linux interface to a static IP address based upon the DHCP subnet used by VMware.
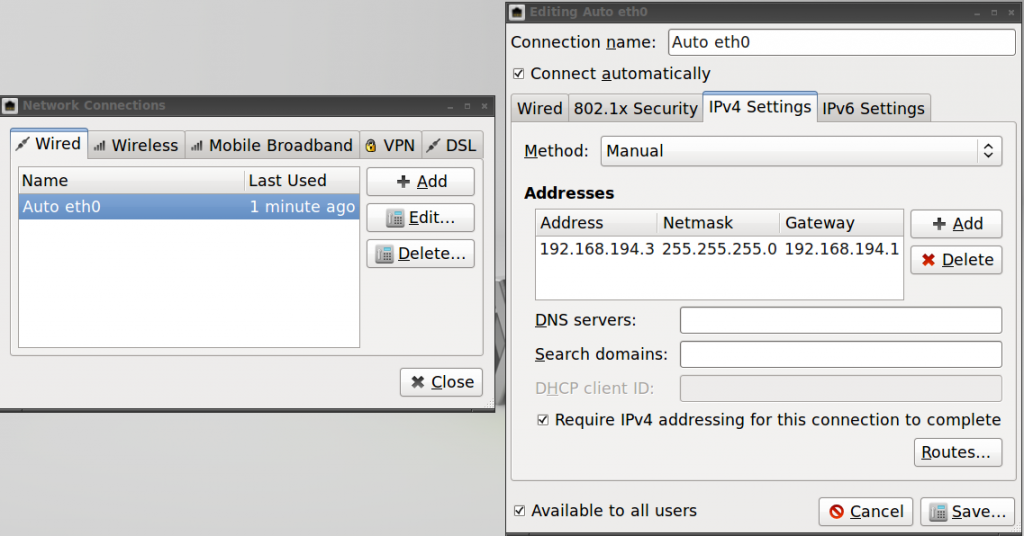
- If JanusVM is currently set to VMnet3, then the local IP address will reveal the subnet being used by that private network, for example if the address was 192.168.194.132, then “192.168.194” would be the subnet being used.
- Click the network connections icon on the right side of the taskbar:
- Click on Edit Connections
- Select the primary connection and click Edit
- In the IPv4 Settings tab, change the type of connection from DHCP (Automatic) to manual
- Enter an IP address matching the subnet mentioned previously, make the last number 2 or 3, if not already taken.
- Enter the gateway as .1
- Save and close the network connections window, then restart the connection by clicking on the connection name in the network connections menu.
- Open a VPN connection between the Linux VM and JanusVM
- This requires using the built-in VPN client for Mint Linux (or whatever flavor you are using)
- Click on the network connections icon on the taskbar.
- Select VPN Connections -> Configure VPN from the pop-up menu
- Click the Add button to create a new VPN connection
- You will need to manually configure it using the following settings:
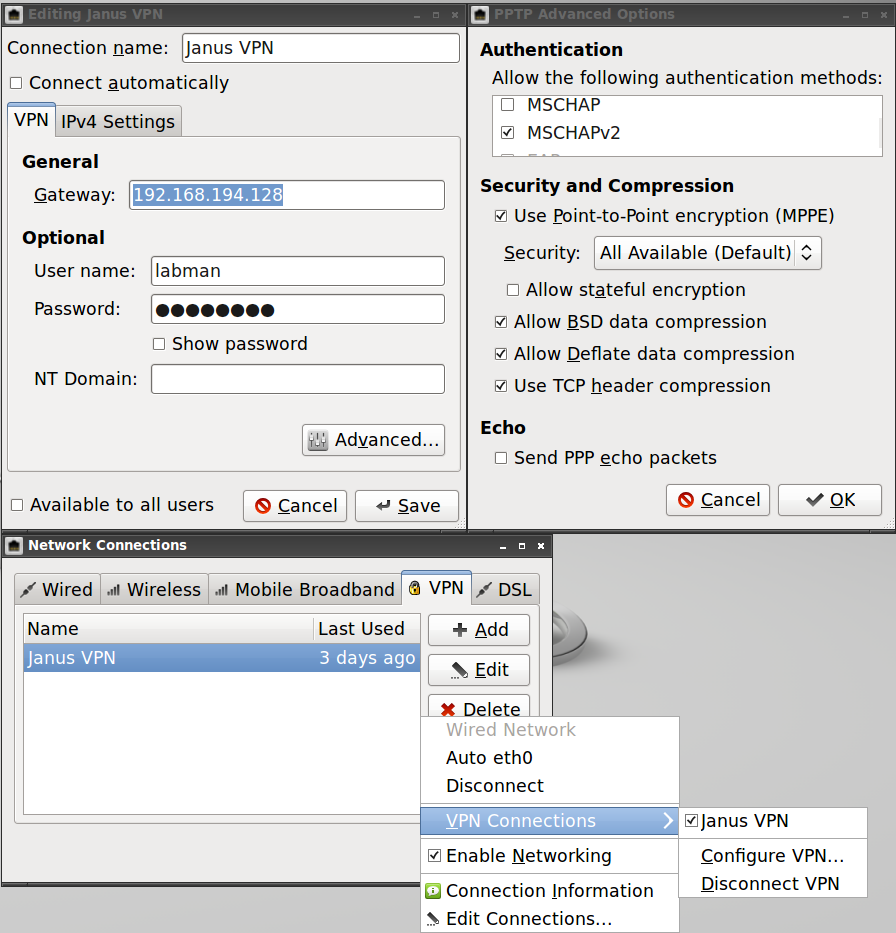
- Name: Doesn’t really matter, JanusVPN works.
- Connection Type: PPTP
- Gateway: Whatever JanusVM is set to for its local PC address.
- Authentication: Only MSCHAPv2
- Select Use Point-to-Point encryption (MPPE)
- Allow BSD, Deflate and TCP Compression
- Enter your username and password for JanusVM (See the previous section)
- Once completed, save and close the VPN and network configuration windows.
- Select the network connections icon again and go to the VPN connections sub-menu. You should see your new VPN connection available to select. If not, try to reset your eth0 connection and see if that does the trick.
- Select the Janus VPN connection
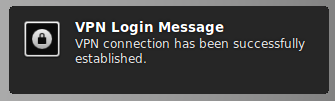
- You should eventually see a notice in the upper right part of the screen (Mint Linux) that says “Connection Successful”
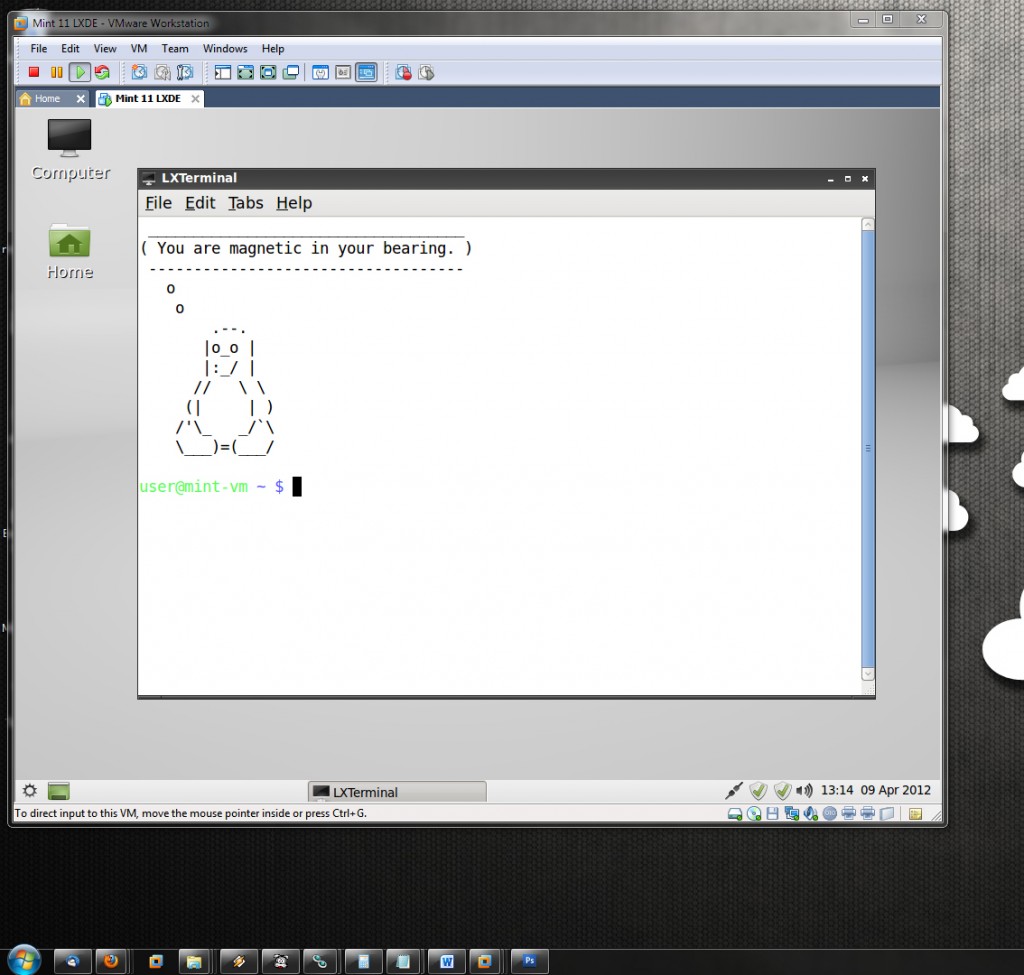
- Type the command ifconfig into a console window to ensure that ppp0 exists; this is your VPN interface.
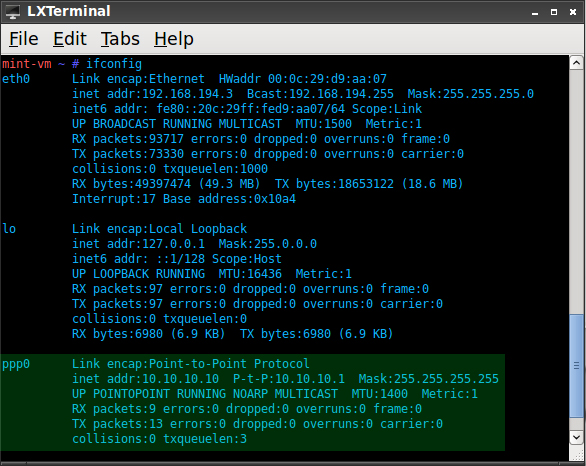
- Turn your Linux system into a router by typing in the following command:
- echo 1 > /proc/sys/net/ipv4/ip_forward
- Configure DNSMasq to run a DNS & DHCP server from eth0 by opening /etc/dnsmasq.conf as ROOT in a text editor
- Line 14: Uncomment “domain-needed”
- Line 16: Uncomment “bogus-priv”
- Line 85: Uncomment “Interface=” and type in eth0 as the interface
- Line 136: Uncomment “dhcp-range=…” modify the range to match the range that VMNet3 is using.
- For example if the VMware DHCP service issues an IP address of 192.168.194.130, then you modify the dnsmasq DHCP range to 192.168.194.50-192.168.194.200 . This is so we can still gain an IP address from VMware for JanusVM but take over DHCP service using dnsmasq so our third system can connect to it.
- Restart DNSMasq
- Type “/etc/init.d/dnsmasq restart” as root in the console window to restart DNSMasq with the new settings
- You can test our new DHCP server by releasing and renewing your IP address on your Windows analysis system, if the gateway matches the IP you assigned for eth0, it works!
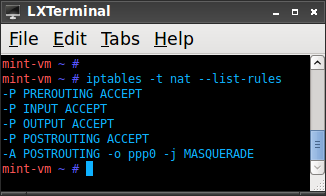
- Using IPTables, forward all traffic coming into eth0 to ppp0 and vice verse
- Type the following command into the console as root
- iptables –t nat –A POSTROUTING –o ppp0 –j MASQUERADE
- After which you should see the following after typing:
- iptables –t nat –-list-rules
- Type the following command into the console as root
- Take a snapshot of the Linux VM & the JanusVM
- Set the Windows VM to use DHCP (if you haven’t done that yet) and restart the system.
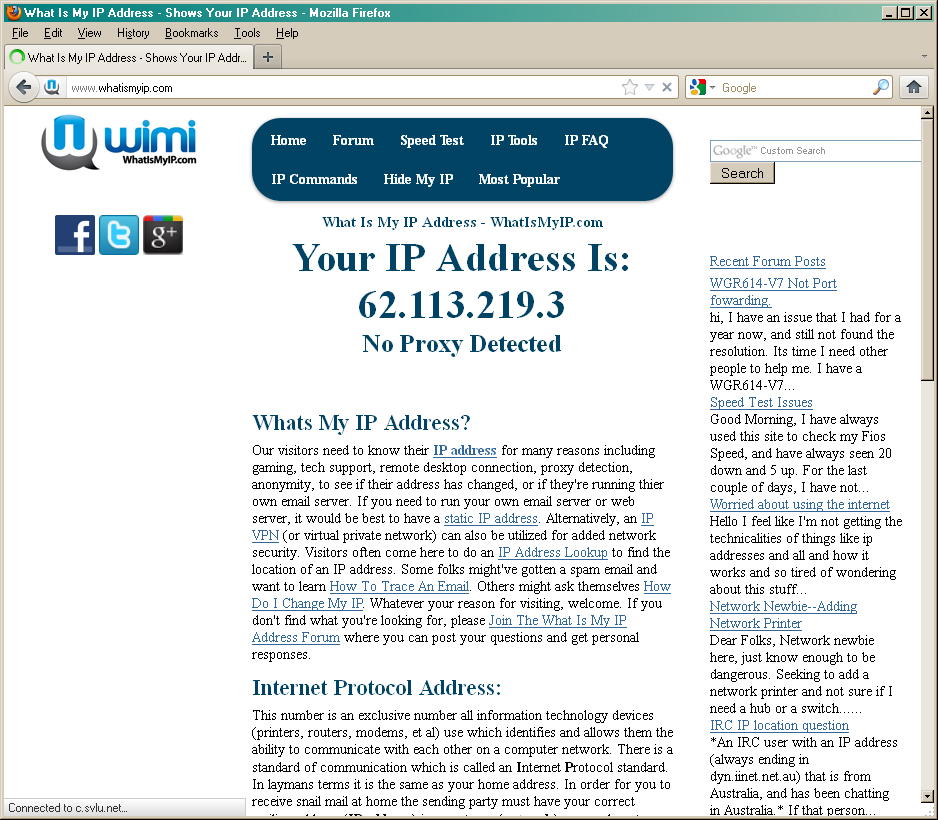
- Test the connection by opening a browser and do a Google search for “What’s my IP?” to make sure you are hidden.
- If it is not connected, check the IP address / DHCP settings for windows, then check to ensure the VPN is connected to Linux correctly and all the interfaces are working correctly. If all else fails, restart everything one at a time.
Explanations:
Q. What is a DHCP/DNS Server and what is DNSMASQ? A. DHCP stands for Dynamic Host Configuration Protocol, which basically hands out IP addresses dynamically to systems which join the network which the DHCP server is on. VMware has a built-in DHCP service available for any of its private networks (VMnet#’s). DNS is short for Domain Name System, and is a service which translates requests for hostnames, i.e. “http://www.mydomain.com”, into IP addresses and passes it back to the requester. DNSMASQ, is both a DCHP and a DNS service application which can be started and attached to a certain interface on a Linux system. When a new system comes onto the VMnet3 private network and it is configured to accept DHCP addresses, it will beacon out to the DHCP server asking to join. DNSMASQ responds to the request and issues the new system an IP address. Now the new system, in our case the Windows Analysis VM, is using the DHCP server as its gateway to the outside world, so when we make a request to Google.com through our browser in our analysis system, that requests goes to DNSMASQ where it routes it accordingly to find the answer and returns it to the Windows VM. DNSMASQ is so important for our use because it makes it possible for us to easily join and be configured into our anonymous network and it also handles our requests when communicating with JanusVM and the anonymous network. Check out these sites for more information on DHCP/DNS & DNSMASQ:
- http://en.wikipedia.org/wiki/Dynamic_Host_Configuration_Protocol
- http://en.wikipedia.org/wiki/Domain_Name_System
- http://www.thekelleys.org.uk/dnsmasq/doc.html
Q. What are IPTables? A. IPTables are chains and rules which configure how the Linux Kernel Firewall operates. The main use of them is to block or allow traffic from specific IP address or ports, however the way we are using them is just simply to forward traffic from one interface to the other. Check out the Wikipedia page on IPTables for a more detailed look:
Summary:
This last tutorial section is really only meant for hardcore malware analysts who have some technical background when it comes to networking and messing with Linux. However it can be employed by anyone who takes the time to learn a little bit more than they already know. This method ensures complete anonymity and the ability to capture traffic if Wireshark is launched on the Linux system, monitoring eth0, for a forced system restart or on the Windows analysis system otherwise.
In Conclusion
So this is the end of the tutorial, thank you for reading and I hope you enjoyed it and/or got some useful info out of it. Please let me know in the comments section if something wasn’t explained well enough or if you would like me to add anything. Also let me know if I had made any mistakes or there is an easier way of making this all work, I am no expert at Linux or dealing with things like IPTables and VPNs , so please give me feedback and I would be happy to modify the tutorials.
Here are some other anonymous surfing solutions you might be interested in:
- http://www.hidemyass.com – Web Interface anonymous surfing good for real quick stuff when you don’t have your Tor Browser handy.
- http://www.happy-vpn.com – A paid service which allows you to create a VPN connection to their secure network to hide all your traffic.










