URGENT: A few days ago a new zero-day vulnerability in Adobe Reader had surfaced. Details below are on Adobe’s blog.
ACTION: Unfortunately, a patch that fixes the issue is still in the works. In the meantime, Adobe suggests users with Adobe Reader 11 enable Protected View. This option can be found under the Edit > Preferences menu, then select Security (Enhanced). Toggle the radio button from Off to Files from potentially unsafe locations. If you’re using a Reader version that’s below 11, make sure you update to 11 first and then apply these settings.
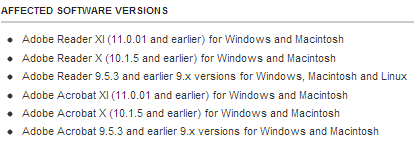
DETAILS: Adobe released an official security bulletin on their website that provides details stating there are two separate vulnerabilities, CVE-2013-640 and CVE-2013-641. With these vulnerabilities affecting Reader versions 9 through 11, many users will be exploitable.
Adobe products (i.e. Reader, Flash Player, etc) have a woefully long history of exploitations, surpassed only by Oracle Java. If you use Adobe software at home, make sure you have automatic updates enabled for all products, and check back often for any future updates.
_______________________________________________________________________________
Joshua Cannell is a Malware Intelligence Analyst at Malwarebytes where he performs research and in-depth analysis on current malware threats. He has over 5 years of experience working with US defense intelligence agencies where he analyzed malware and developed defense strategies through reverse engineering techniques. His articles on the Unpacked blog feature the latest news in malware as well as full-length technical analysis. Follow him on Twitter @joshcannell









