Cydia is a program for iOS that allows you to install software packages on your Jailbroken iPod / iPhone / iPad that aren’t normally available on Apple’s App Store.
Cydia helps you manage various software sources (also known as repositories or repo) via its friendly user interface.
While many repositories are legitimate, there are just as many that let you download pirated apps for free. Beyond the copyright infringement issue, there is also the risk of downloading an infected app and getting more than what you bargained for (you can read this post about Android security which also talks about unknown sources and reputable markets).
Whether a Cydia source is legitimate or not, it remains a potential security issue simply because we don’t always know how well it may be maintained. Today, we take a look at a popular repository called iHacksRepo which had its website compromised and was leveraged to serve the Redkit Exploit Kit.
This exploit takes advantage of outdated Java software to install malware on the visitor’s (Windows) machine. So as far as we can tell, this will not compromise your mobile device.
The drive-by download attack, provided by the Redkit Exploit Kit, was also reported on urlquery.net. This particular Exploit Kit is known to use many intermediaries/redirections and make it look like the malicious files are coming directly from the compromised website.
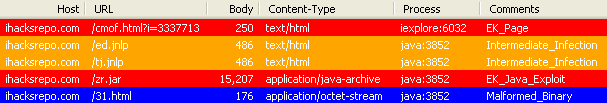
In fact, the payload is served through a php shell script that downloads a malicious landing page and Java applet from the Exploit Kit’s command and control server. The final malware payload consists of an encoded stream decrypted by the malicious jar file, something we have talked about before (Redkit does the splits).
Most site hacks are automated with scripts scanning for vulnerabilities in Content Management Systems (CMS) and core server programs like Apache, PHP, and MySQL. There are also brute force attacks to gain access easily when passwords are weak, not to mention credentials harvested directly from site owners by typical password stealers.
This particular website is perhaps more interesting than your average compromised personal blog in that it contains apps for download.
If the server is compromised, bad guys could do more damage by gaining root level access and go after something valuable like software packages which, in theory, could be altered to include malware. Unsuspecting users would then download malicious apps onto their devices.
Feeling like playing some Angry Birds? An innocuous game could hide a nasty program that steals your contact list, sends costly SMS messages and more, all without your knowledge.
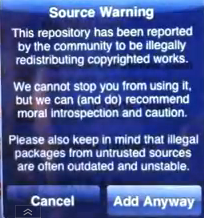
In some cases, you will get a warning message when adding a repository known to distribute pirated materials which is one thing, but unfortunately many users may not be aware of the danger with apps coming from third parties. That isn’t to say that the official App Store is immune, but at least there is usually better quality control, and safeguards are in place. If you do own a Jailbroken device, you want to make sure the apps you are going to download have not been tampered with. Choosing a well-known and trusted repo helps but is no guarantee you won’t end up with some malware on your device.









