
Malware authors are known to try various obfuscation techniques in order to hide their malware. The Unicode Right-to-Left trick (RLO), which has been known for quite some time, has been reported again by security firm F-Secure, showing its resurgence.
In their report, a signed Apple program was disguised to hide its true nature and install a piece of malware.
This prompted me to examine this technique in greater detail. This is a neat trick that deserves a proper explanation.
To understand how this works you need to know what Unicode is: an international encoding standard for use with different languages and scripts.
This allows computers, in our case, to display characters in special ways. The feature abused here is the “Right-to-Left” function. This would most commonly be used when displaying a language that is read in such a fashion, such as say Arabic, or Hebrew, to name a few.
This means that a cleverly named executable, manipulated in such a way, could be made to appear as something other than what it really is.
Windows XP requires specific configuration changes to enable support for this feature. We can use it to demonstrate what the file looks like, if an operating system does not know how to display RLO properly. This is useful to visualize where the flip point is inserted. Here is Windows XP, displaying my test file:

The white box in the filename is the RLO unrecognized, thus not reading from right to left. This makes it easy to spot our file as an executable. Once the flip occurs the “cod” will appear as “.doc” completing the illusion.
Native support for this feature has been present since Windows Vista. Here is the same file, on a Windows 7 system:

I chose a filename that completed the illusion but didn’t look suspicious. You could also have multiple RLO insertions to accommodate a different name that would not need to end in “exe.” I also took it a step further, by modifying the embedded icon of the executable, to make it appear as a word document. Another common file extension used with this technique is “.scr,” which is used for screen savers.
Although this particular example was crafted for the PC, on a PC, I decided to copy it over to other machines in our lab, to see how it would be displayed. Here is the same file, on a Linux machine:
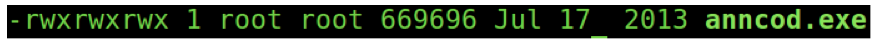
Since Linux cannot execute windows PE files, the threat is greatly reduced, but the file name is still being shown with the “.doc” file extension. Examining the same file from a command line environment reveals it’s true nature:
And again, on a mac:

As it was originally crafted for a PC, this doesn’t work very well. The OSX command line also displays the file correctly:
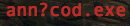
However the autocomplete feature built into the command line of OSX briefly shows the file the other way:
A common vector for such files would be via e-mail, and unless the file was compressed in a zip, executables are disallowed. I tried sending the file via Gmail, and received an interesting error:
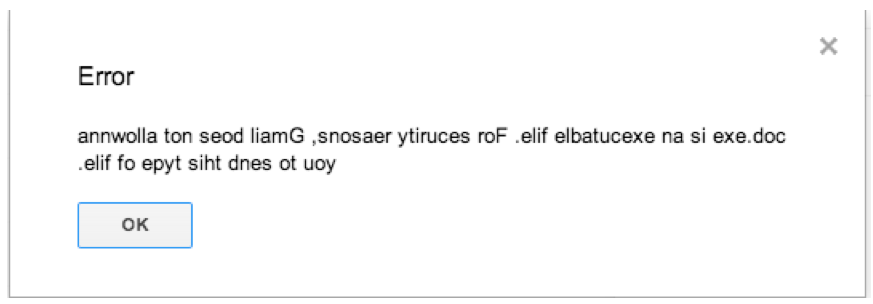
This message is Gmail, informing me that executables aren’t allowed.
And there you have it! Right-to-left functionality abused to try and cloak the file extension of an executable. This is by no means a new vulnerability, but still an interesting vector.









