
If you’ve been reading the news lately, you’ve probably noticed the New York Times (NYT) website was defaced just two days ago on August 27th. On that same day, The NYT made comments concerning the attack in their blog after the website was restored.
In that post, the NYT states that their domain name registrar, MelbourneIT, was hacked. A registrar is a service where one can purchase a domain name that will be placed in a Domain Name registry.
The hackers, better known by the public as the Syrian Electronic Army, managed to gain control of MelbourneIT’s admin control panel. From there, they updated the addresses of the NYTimes.com name servers, which were then pushed to the name registry for the .com TLD that’s operated by Verisign.
The Domain Name System (DNS) is a very crucial part of the internet, responsible for converting domain names into IP addresses. In this scenario, the DNS lookup process was tampered with, and traffic intended for the NYT was instead routed to the attacker’s server.
The Syrian Electronic Army has gotten a lot of publicity lately, taking an interest in hacking American media outlets. Back in April, they claimed responsibility for hacking the Twitter accounts of both The Guardian and Associated Press, both achieved through phishing emails. Then, just a few weeks ago, the Washington Post’s website was hacked, to which the SEA are also credited for the attack, also reportedly caused by phishing emails.
While the method of the attack on the NYT was initially uncertain, one day later an article from USA Today shed light on the situation, stating that MelbourneIT delegated control of Internet Traffic to the NYT to several ISPs, including one in India.
In the article Bill Conner, CEO of the identity management firm Entrust, states that “The SEA focused on the weakest link, executing a spear-phishing attack that successfully obtained the user name and password of at least one administrator at the Indian ISP.”
Apparently, the Syrian Electronic Army likes to phish.
And for good reason. Social Engineering attacks like phishing have proven to be a very powerful. Once a hacker gets a ‘bite’ per se, he or she can use a compromised account (even a less privileged one) to gain a foothold in your internal network.
Many companies offer training to their employees to help them identify possible phishing threats, but that doesn’t solve the problem entirely. Unfortunately, as is the case with many things, one weak link can bring a whole body down.
It is not entirely certain who the individuals involved in these attacks are—the members of the SEA, that is. However, American Security Journalist Brian Krebs has performed some research and may have a lead on that answer.
Krebs managed to use an email address acquired from a hack against the SEA’s website and trace it to a particular individual: Mohammed Osman. According to Krebs’ writeup, Osman recently relocated to Turkey, and has experience as a front end developer. Shortly after posting the article, Krebs received an email from Osman, denying any involvement with the SEA.
Image: Krebs on Security
In that same article, Krebs references a piece from Vice.com about another possible suspect, named Hatem Deeb. According to the report, Deeb had been identifed as “ThePro”, a name used by one of the SEA hackers. The connection was made when Deeb had listed his name on a receipt for a Virtual Private Server (VPS) that was rented for use by the SEA. Vice.com also reports that The Pro, who is presumed to be Deeb, also maintains a blog where he lists his achievements.
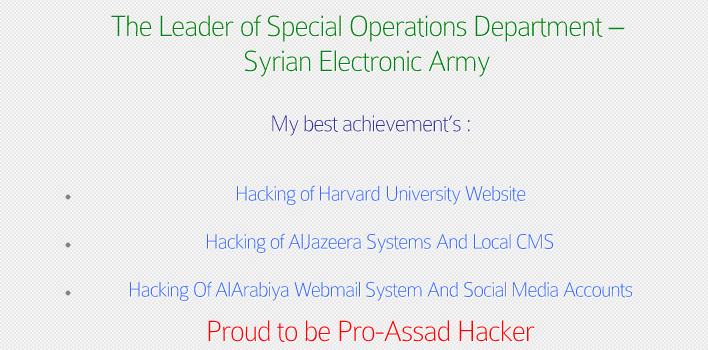
Image: Vice.com
Like Osman, ThePro replied to these allegations, claiming that he was not Deeb, but instead it was the name of an “SEA friend”.
Wow, that’s an original one.
While we may not be 100% certain that Osman or Deeb are in fact SEA members, it seems like it’s only a matter of time before all the pieces come together.
To close, it is interesting to note that many security researchers believe the SEA are mere amateurs due to their phishing tactics; however, does their prevalence in the mainstream media (or taking down thereof) suggest otherwise? Notwithstanding the simple attack method involved, it appears the SEA has been successful against an array of high profile websites. Food for thought.
Feel free to share your thoughts in the comments below, and stay tuned for any new developments.
_______________________________________________________________________________
Joshua Cannell is a Malware Intelligence Analyst at Malwarebytes where he performs research and in-depth analysis on current malware threats. He has over 5 years of experience working with US defense intelligence agencies where he analyzed malware and developed defense strategies through reverse engineering techniques. His articles on the Unpacked blog feature the latest news in malware as well as full-length technical analysis. Follow him on Twitter @joshcannell









