Security company VUPEN revealed a vulnerability in Java’s Preloader in early July that’s quite likely the same one being integrated into cyber criminals’ exploit kits.
According to VUPEN’s report, the vulnerability is “caused by a design error in the Java click-2-play security warning when the preloader is used, which can be exploited by remote attackers to load a malicious applet (e.g. taking advantage of a Java memory corruption vulnerability) without any user interaction.”
The flaw which affects Java version 7 update 21 and earlier bypasses the traditional security warning displayed before an applet is allowed to run:
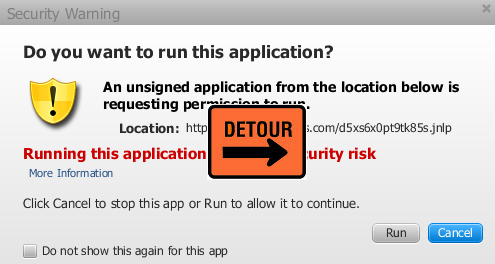
In essence, the exploit will be delivered silently and the user will never see the security prompt.
French security researcher @Kafeine blogged about this last week when he identified the vulnerability being used in at least three exploit kits: Cool EK, Sakura and Nuclear Pack.
The Click2Play bypass is coupled with CVE-2013-2460 which in itself is not able to directly infect the victim without a security prompt.
Having both Click2Play bypass and CVE-2013-2460 together guarantees the highest infection rates since anybody running Java 7 update 21 or earlier will get infected.
When it comes to drive-by attacks, Malwarebytes users can rely on a double layer of protection: our flagship Malwarebytes Anti-Malware and our new Malwarebytes Anti-Exploit.
The first layer of defense, Anti-Exploit, proactively blocks unknown threats coming from your browser or common applications, before they infect your system.
Anti-Exploit is not based on a list of CVEs or malware signatures and that is one of its strengths.
To prove that point we went ahead and tested this attack with a year-old version of the software, when it was still called ExploitShield.
As you can see in the video below, the threat was stopped in its tracks.
A few months ago, ExploitShield became part of the Malwarebytes family and re-branded as Malwarebytes Anti-Exploit.
The following video shows how easy it is to install it and be protected immediately:
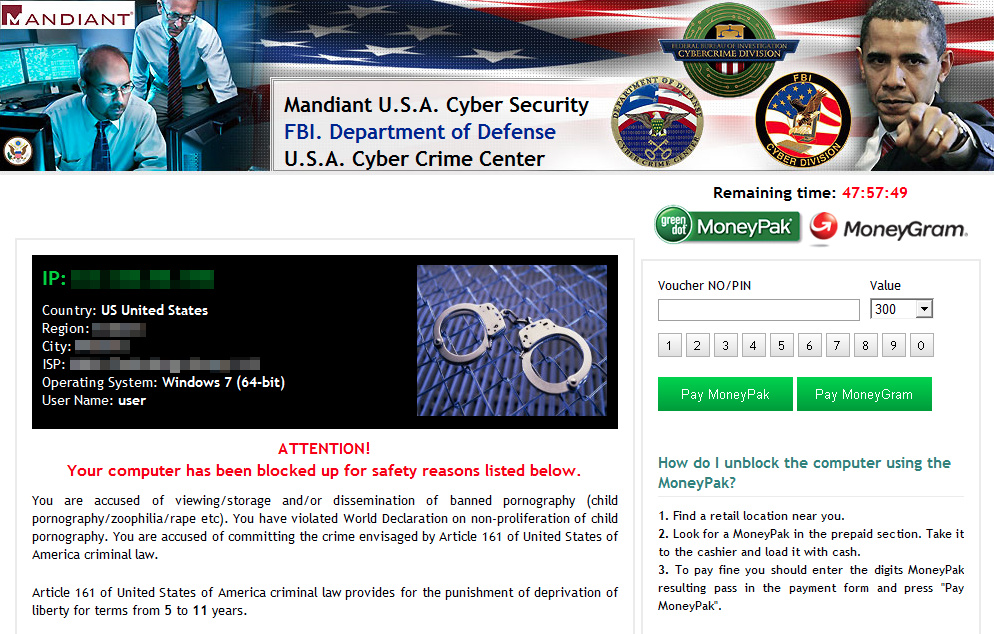
If you weren’t running Anti-Exploit and got infected, you most likely got hit with Ransomware or Fake AV.
Urausy Ransomware for US residents:
Fake AV (Antivirus Security Pro):
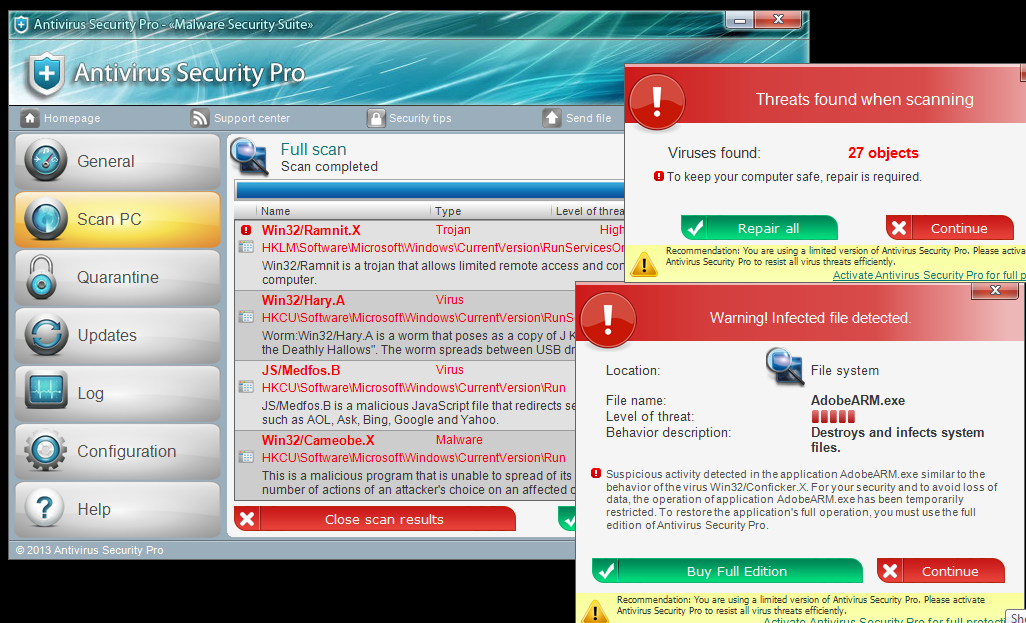
Screenshot courtesy of Malware don’t need coffee
On an already infected system we recommend Malwarebytes Anti-Malware. If you can’t get it to install, there is a utility called Chameleon designed specifically for those tricky situations where malware is preventing you from running removal tools.
It goes without saying that stopping an infection as early as possible is the best way to go. With a layered defense, you are keeping your system more secure against web threats.
While Anti-Exploit will protect up-to-date as well as outdated systems equally (it will block zero days and existing vulnerabilities), it still makes sense to apply some basic security principles such as opting in for Windows automatic updates, applying third-party software patches, etc.
With regards to Java, because it is such a big target in all exploit kits, we recommend that you disable the browser plugin, or if you feel you don’t need it at all, to uninstall it altogether.
Reducing the attackers’ surface of attack on your system is one of the simplest and most effective things to do.
Jerome Segura (@jeromesegura) is Senior Security Researcher at Malwarebytes.









