Blackhole is one of the most popular crimeware toolkits serving browser-based exploits from compromised or malicious websites. Their end goal is to deliver malware (ransomware, banking trojans etc) onto unsuspecting visitors.
A few hours ago, a tweet from Maarten Boone, a security researcher at Fox-IT, a Dutch security firm didn’t go unnoticed:
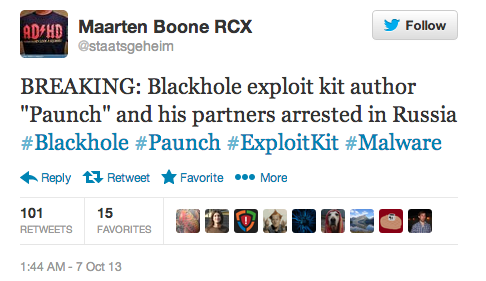
The news very quickly spread across social network that Paunch, the guy behind the infamous Blackhole exploit kit, had been arrested.
While there has not been an official statement released yet, we have observed some corroborating events in the wild.
crypt.am a service used to encrypt the exploit kit is down:
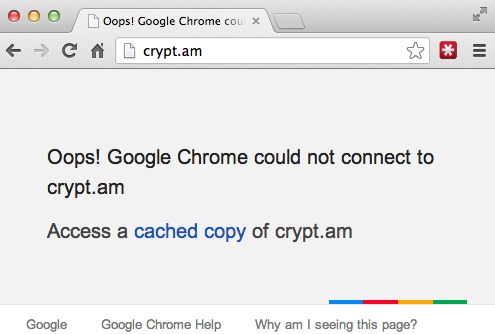
crypt.am down: a sign of something going on?
Security researcher Kafeine who has been documenting Blackhole for a long time, published this nice graphic showing how the malicious Java applet Paunch normally updates between once and twice a day, simply hasn’t changed for at least four days now.

Blackhole ecosystem (click to enlarge)
We confirmed the strong presence of the same Java file in the last 24 hours from our own honeypot collection:
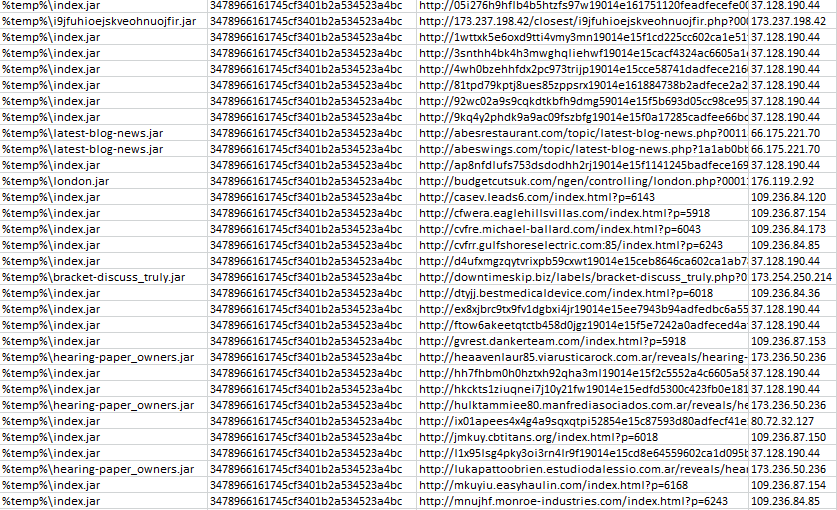
Same java exploit file, unchanged for 4 days (click to enlarge)
And here is the first instance of it we ever recorded (October 3rd at 10:52 PM PT):
Path and name: %temp%bracket-discuss_truly.jar
Size: 29253
MD5: 3478966161745cf3401b2a534523a4bc
Type: EK_Java_Exploit
Exploit URL: http://downtimeskip . biz/labels/bracket-discuss_truly.php?b1ab1010aa=bab000a0abb&1abbb1a01bb010bb1=aba1baa0abba111a0
IP address:173.254.250.214
Date: 2013-10-03-22-52-21
This may very well be the last update we see, unless somebody picks up the torch.
What can we expect in the next hours and days? Criminals that ‘rent’ the Blackhole exploit kit will no longer receive updates and eventually the exploit and payload are going to go stale.
Those that host the exploit kit themselves have more control in that they could (if savvy enough) make some alterations to the kit to “keep it alive”.
In all likelihood, we are going to see cyber-crooks migrate their infrastructure towards other exploit kits very soon. In fact, Kafeine already spotted that the Reveton distribution moved from a Cool EK (maintained by Paunch) to a Whitehole exploit kit.
This would be a major event in the exploit kit business, one that could trigger a chain reaction leading to more arrests and disruption. We can’t wait to hear the official news as well as if other gangs have been caught.
Update (1) 10/08: Security researcher Xylitol tweeted that a message had been posted on Darkode.com, a forum for cyber-criminals. This was published under the Blackhole’s author account (Paunch) and can be translated as “I will never go to jail! Do not worry friends.“
{edit} This turned out to be a fake message destined to fool security researchers.
Update (2) 10/08: Europol confirmed the arrest. You can read more in this post from David Gilbert of International Business Times.
Jerome Segura (@jeromesegura) is Senior Security Researcher at Malwarebytes.









