Potentially Unwanted Programs or PUPs as we like to call them, are things like Toolbars, Search Agents, etc. Unnecessary junk for your desktop that usually involves monitoring your surfing/shopping habits and slowing down your system with their sub-par software that ends up hurting you much more than helping.
A recent and unfortunate discovery by some of our users revealed that some of these programs do more than just cover your desktop in ads, they also steal your systems resources for mining purposes.
I have written two blog posts in the recent past about Bitcoin Mining as well as the various types of cybercrime getting involved in the Bitcoin hype, either by installing miners to crunch numbers on an infected users system or otherwise stealing Bitcoins directly from online Bitcoin wallet services.
This time, however, we are taking a look at a PUP that installs a Bitcoin miner on the user system, not just for a quick buck but actually written into the software’s EULA.
This type of system hijacking is just another way for advertising based software to exploit a user into getting even more cash.
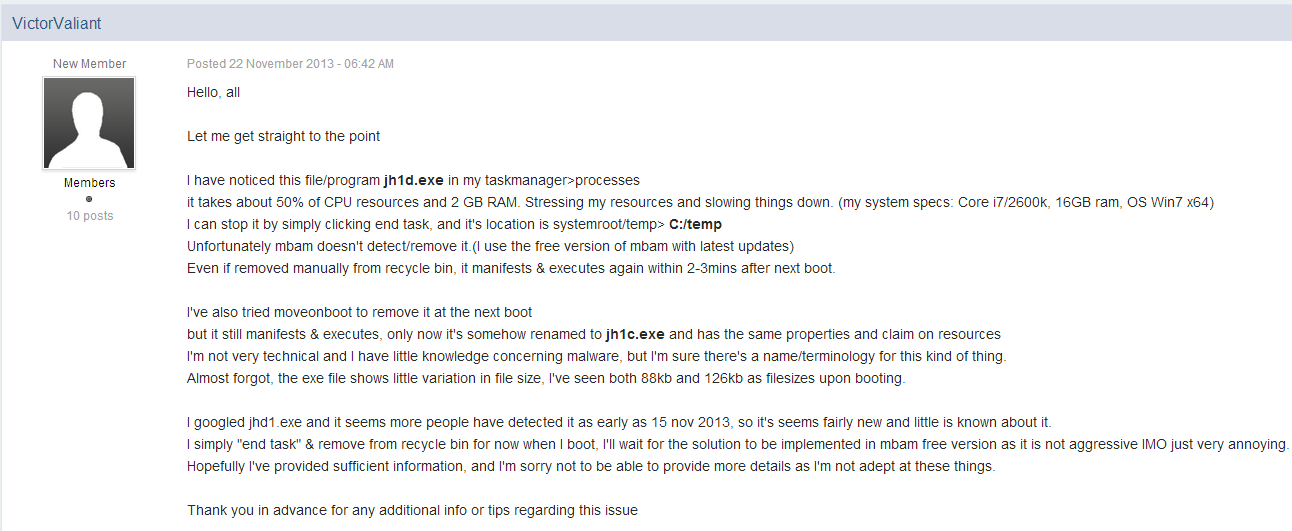
On Nov 22, we received a request for assistance from one of our users about a file that was taking up 50 percent of the system resources on their system. After trying to remove it by deleting it, he found that it kept coming back, the filename was “jh1d.exe”.
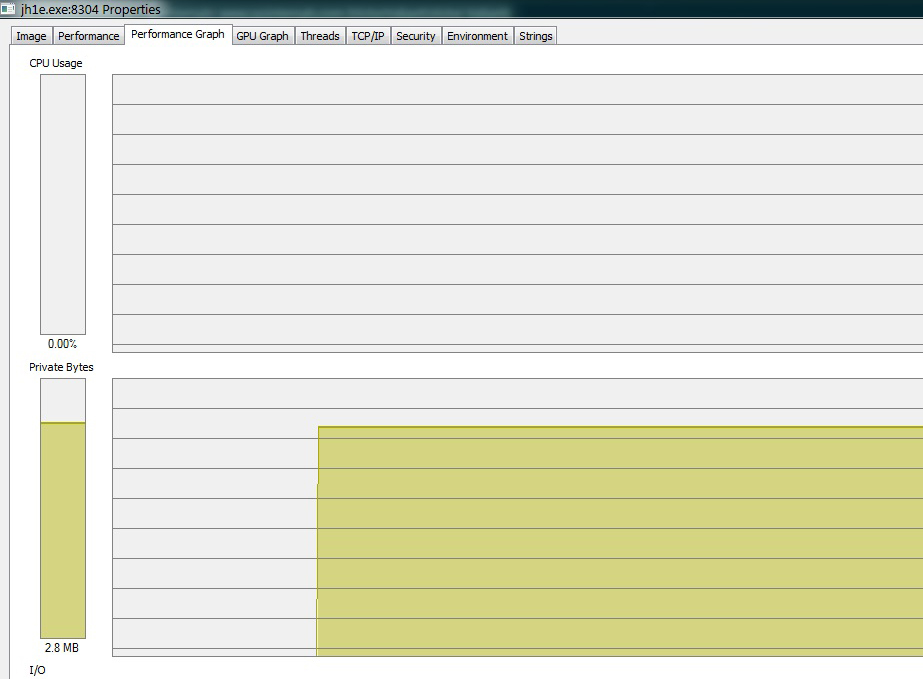
We did some research and found out that the file in question was a Protoshare Miner (similar to a Bitcoin Miner that uses CPU Memory rather than GPU) known as “jhProtominer”, a popular mining software that runs via the command line.
However, it wasn’t the miner recreating its own file and executing but a parent process known as “monitor.exe.” Monitor.exe was created by a company known as Mutual Public, which is also known as We Build Toolbars, LLC or WBT.
We were able to find out the connection between WBT and Mutual Public thanks to an entry in the Sarasota Business Observer.
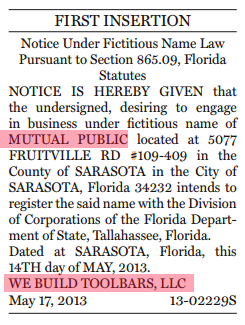
Another product belonging to Mutual Public is known as Your Free Proxy.

The website for YourFreeProxy is also owned by WBT LLC, according to a lookup of their domain name.
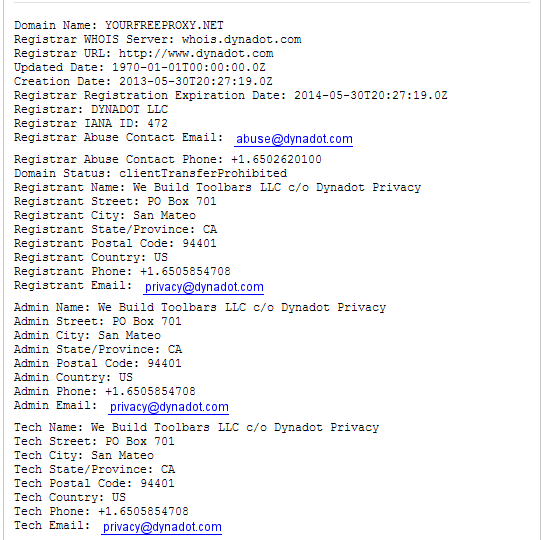
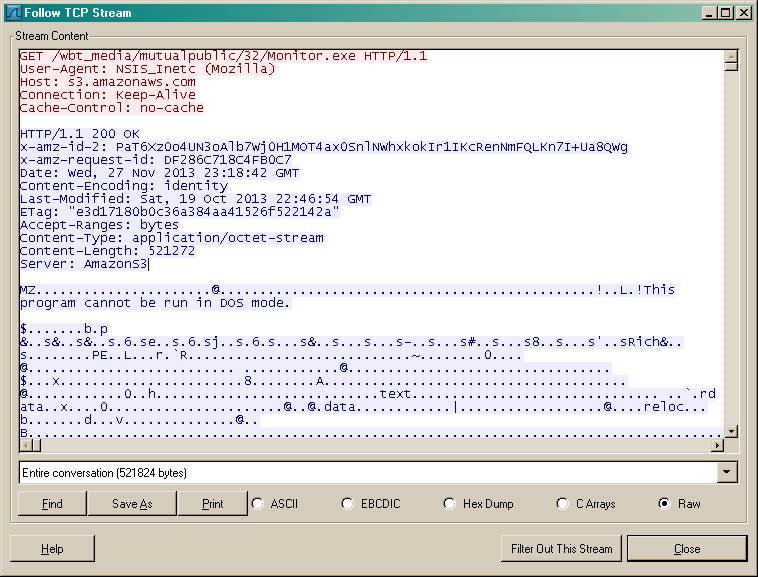
Your Free Proxy uses the Mutual Public Installer (monitor.exe), obtaining it from an Amazon cloud server.
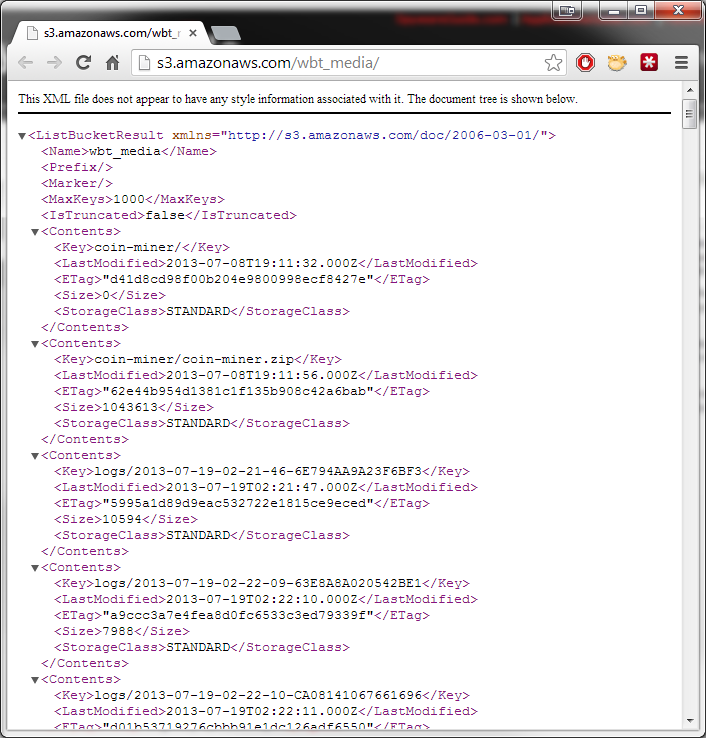
We checked out this cloud server and found monitor.exe but also some additional interesting files, notably multiple types of “silent” installers and a folder called “coin-miner.”
Monitor.exe beacons out constantly, waiting for commands from a remote server, eventually downloading the miner and installing it on the system.
So now that we have proof that a PUP is installing miners on users systems, do they do it without ever letting the user know? Well not exactly, their EULA specifically covers a section on Computer Calculations: COMPUTER CALCULATIONS, SECURITY: as part of downloading a Mutual Public, your computer may do mathematical calculations for our affiliated networks to confirm transactions and increase security. Any rewards or fees collected by WBT or our affiliates are the sole property of WBT and our affiliates.
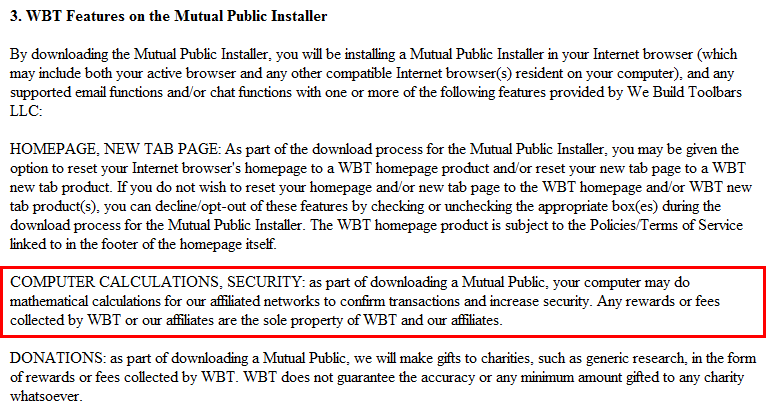
Their explanation is basically the purpose of Bitcoin Miners and that they will install this software on the system, run it, use up your system resources and finally keep all rewards from the effort YOUR system puts in.
Talk about sneaky.
In my opinion, PUPs have gone to a new low with the inclusion of this type of scheme, they already collected information on your browsing and purchasing habits with search toolbars and redirectors.
They assault users with pop-up ads and unnecessary software to make a buck from their affiliates. Now they are just putting the nails in the coffin by stealing resources and driving user systems to the grave.
Though are Bitcoin Miners bad? Are they always used by malicious ne’er do wells? No way! When used legitimately by willing participants, they help the Bitcoin network run more efficiently and make some extra cash for those willing to put in the effort.
The unfortunate side is that while anyone can run a miner, anyone can also force a miner to run on a system, even if it isn’t their own.
So take note if your system is running especially slow or if a process is taking up massive amounts of your processing power; it might be malware or even a PUP running a miner on your system.
We at Malwarebytes are putting our foot down and detecting these threats as what they are, giving our users the option to remove them and never look back. A special thanks to Rich Matteo, Dave Nelson, Steven Burn, VictorValiant and Hammerhode for bringing to attention this threat and the efforts made to put an end to it.
UPDATE: Dec 02,2013: Looks like an Independent Security Researcher, Ashkan Soltani, wrote about a similar incident on 25 Nov, concerning the gaming company E-Sports, where the state of New Jersey sued the company for installing BTC miners on users systems. Looks like everyone is getting Bitcoin fever =/.
——————————————————————————————————–
Follow Adam Kujawa and all of his zany opinions on Twitter @Kujman5000











