Here’s a really weird Apple phish, which seems to want to limit the amount of people who actually fall for it – much less read it at all.
For years, scammers have walked a razor’s edge of trying to look legitimate while claiming to be some sort of distant relation to the wallet inspector. Most thieves will take a chance and include a “be wary of phish mails, we take your security seriously” message in their missives because it’s what we expect to see (especially in banking emails and related websites).
However, this one may be going a little too far with regards efforts to stop you from opening their spam mail:
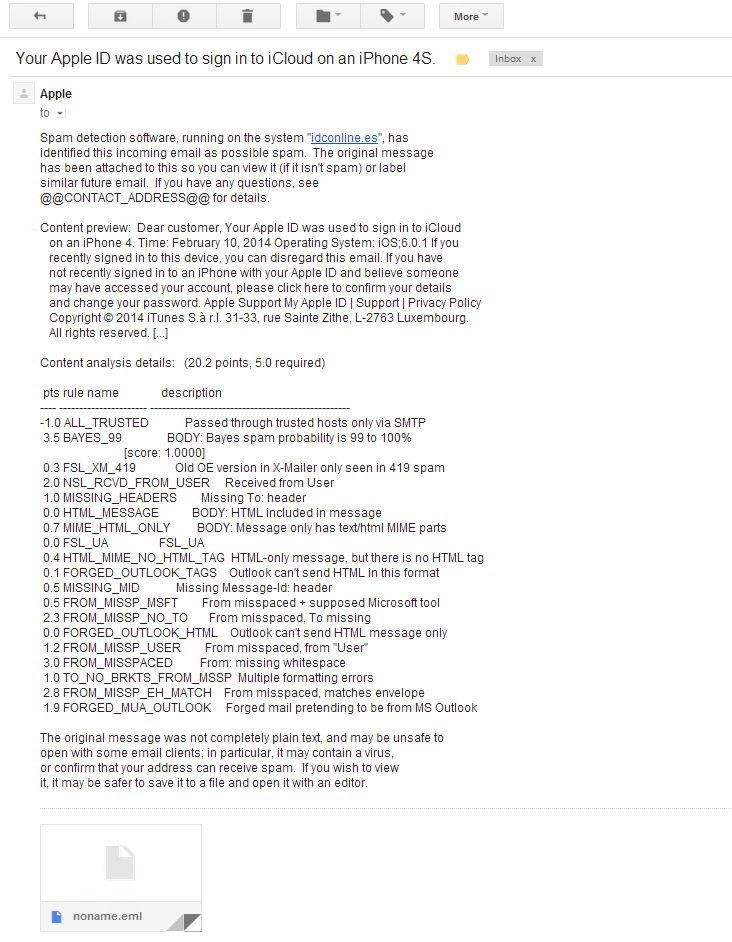
“Spam detection software, running on the system “[url]”, has identified this incoming email as possible spam. The original message has been attached to this so you can view it (if it isn’t spam) or label similar future email. If you have any questions, see @@CONTACT_ADDRESS@@ for details.”
That’s a weird way to open a spam message, right? They continue with the content of the supposed email, which is unformatted and a mess to read – I doubt many people will bother to even look at it.
Then things get even weirder, with the following “content analysis” of the email:
Content analysis details: (20.2 points, 5.0 required)pts rule name description —- ———————- ————————————————– -1.0 ALL_TRUSTED Passed through trusted hosts only via SMTP 3.5 BAYES_99 BODY: Bayes spam probability is 99 to 100% [score: 1.0000] 0.3 FSL_XM_419 Old OE version in X-Mailer only seen in 419 spam 2.0 NSL_RCVD_FROM_USER Received from User 1.0 MISSING_HEADERS Missing To: header 0.0 HTML_MESSAGE BODY: HTML included in message 0.7 MIME_HTML_ONLY BODY: Message only has text/html MIME parts 0.0 FSL_UA FSL_UA 0.4 HTML_MIME_NO_HTML_TAG HTML-only message, but there is no HTML tag 0.1 FORGED_OUTLOOK_TAGS Outlook can’t send HTML in this format 0.5 MISSING_MID Missing Message-Id: header 0.5 FROM_MISSP_MSFT From misspaced + supposed Microsoft tool 2.3 FROM_MISSP_NO_TO From misspaced, To missing 0.0 FORGED_OUTLOOK_HTML Outlook can’t send HTML message only 1.2 FROM_MISSP_USER From misspaced, from “User” 3.0 FROM_MISSPACED From: missing whitespace 1.0 TO_NO_BRKTS_FROM_MSSP Multiple formatting errors 2.8 FROM_MISSP_EH_MATCH From misspaced, matches envelope 1.9 FORGED_MUA_OUTLOOK Forged mail pretending to be from MS Outlook
In other words, “This is fake, that’s fake, the thing over there? Take a wild guess”. And then, finally, they talk about the email proper…by telling you that they likely sent you a scam or a virus, but you can still open it up and take a look regardless:
The original message was not completely plain text, and may be unsafe to open with some email clients; in particular, it may contain a virus, or confirm that your address can receive spam. If you wish to view it, it may be safer to save it to a file and open it with an editor.
Fantastic.
On top of that lot, we also have the attachment itself which is an .eml file and typically opened with Outlook Express. If you don’t have that installed, you could open it with (say) Thunderbird, or rename it as a .html document and look at the code. If you really wanted to. Which you probably don’t.
Now that they’ve managed to reduce their potential victim pool through error, outdated information and lots of hoop jumping to maybe six people, we should see what exactly is in there:
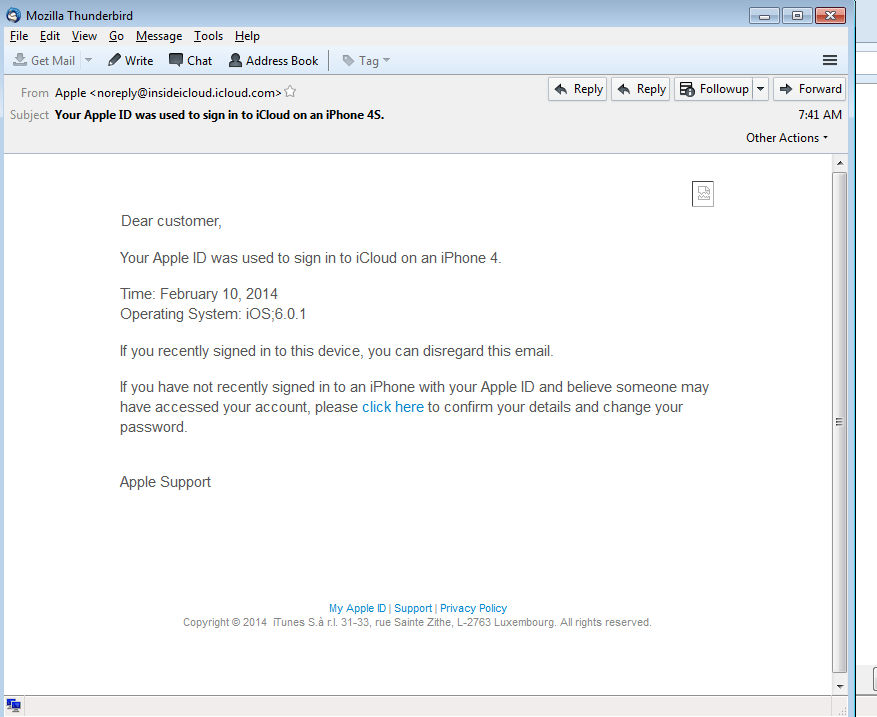
Dear customer, Your Apple ID was used to sign in to iCloud on an iPhone 4.Time: February 10, 2014 Operating System: iOS;6.0.1
If you recently signed in to this device, you can disregard this email. If you have not recently signed in to an iPhone with your Apple ID and believe someone may have accessed your account, please click here to confirm your details and change your password. Apple Support
Another “We really couldn’t be bothered trying with this one” mistake, in the form of the date: February 10? Oh dear, someone didn’t tweak their fake email dates.
Clicking the link takes the end-user to a page that’s currently offline. Looking at the state of play up to now, I wouldn’t be surprised if it’s a large gif of a police siren wailing while “Danger, Will Robinson” flashes up in size 50 font.
Sometimes scammers get it right and pull off extremely clever and subtle phish attacks. Other times, they get it wrong and you’re left scratching your head and wondering what on earth happened.
This is most definitely a case of the latter.
Christopher Boyd










