It has been a while since we pushed out “A .Gov Media Player? Not Exactly…”, a blog post about arcadia-fl[dot]gov at the time of its compromise and serving a binary file, and “Philippine Government Site Infected with Spam Code”, which is about da[dot]got[dot]ph pages that is found to contain hidden Blackhat SEO spam links. Recently, we’ve noticed a number of .gov URLs that were broken into to host different pages.
Our first domain, one from Taiwan, has served a “Hacked by…” page which we normally see hackers put up to show that they’ve “owned” it.
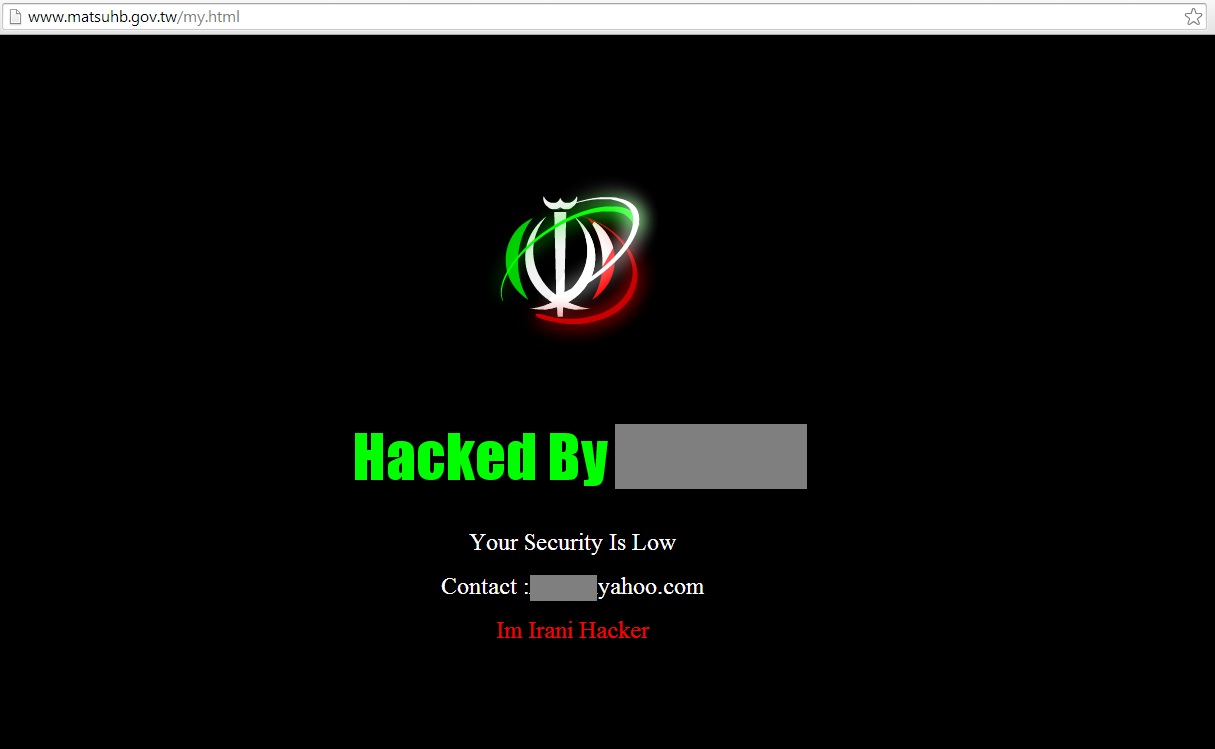
click to enlarge
Doing a quick search of the email address leads to other compromises done by this particular hacker. The image above the big, green text is actually a Flash media file hosted on a Russian server that is also known to serve malware.
We also found that a lot of pages hosted on this domain have spammy content revolving around Viagra, gambling, and student loans, among other else. For the complete list of spammy pages, here‘s the scan result page from Unmasked Parasites.
For our second domain, a Ukrainian government site, has served a Google Drive phishing page.

click to enlarge
Both pages are now down.
With the number of .gov sites we have seen that are insecure, it pays for users to be careful of potential risks they may encounter when visiting them. As they remain vigilant with this, so, too, should admins with hardening site security and keeping pages free from spammy, phishy, and malicious content.
Jovi Umawing










