A new Adobe Flash zero-day, the third one this year so far, has been found in the wild via drive-by download attacks, according to firm TrendMicro.
According to our telemetry, Malwarebytes Anti-Exploit has been blocking this zero-day since around December 10th, 2014.
Adobe released a security advisory and assigned the vulnerability as CVE-2015-0313 and rated it critical:
A critical vulnerability (CVE-2015-0313) exists in Adobe Flash Player 16.0.0.296 and earlier versions for Windows and Macintosh. Successful exploitation could cause a crash and potentially allow an attacker to take control of the affected system. We are aware of reports that this vulnerability is being actively exploited in the wild via drive-by-download attacks against systems running Internet Explorer and Firefox on Windows 8.1 and below.
Unsuspected users are redirected to the HanJuan Exploit Kit (thanks Kafeine) via the delivery.first-impression.com (EngageBDR) ad network:
We have tracked this malvertising on some major websites including:
- dailymotion.com
- theblaze.com
- nydailynews.com
- tagged.com
- webmail.earthlink.net
- mail.twc.com
- my.juno.com
The delivery mechanism is straightforward:
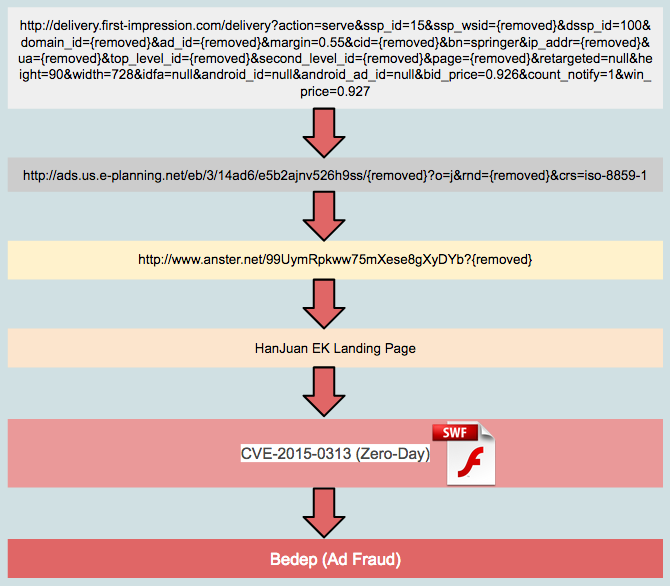
The malicious ad won the bidding process to get displayed for the small cost of $0.927 per impression.
The HanJuan Exploit Kit finishes the infection by exploiting CVE-2015-0313 (Flash 0day):
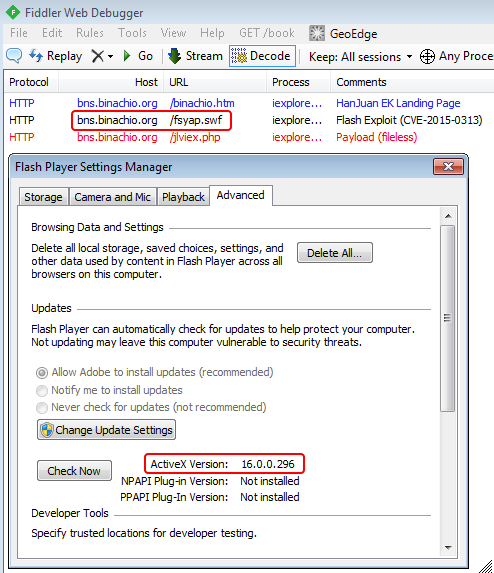
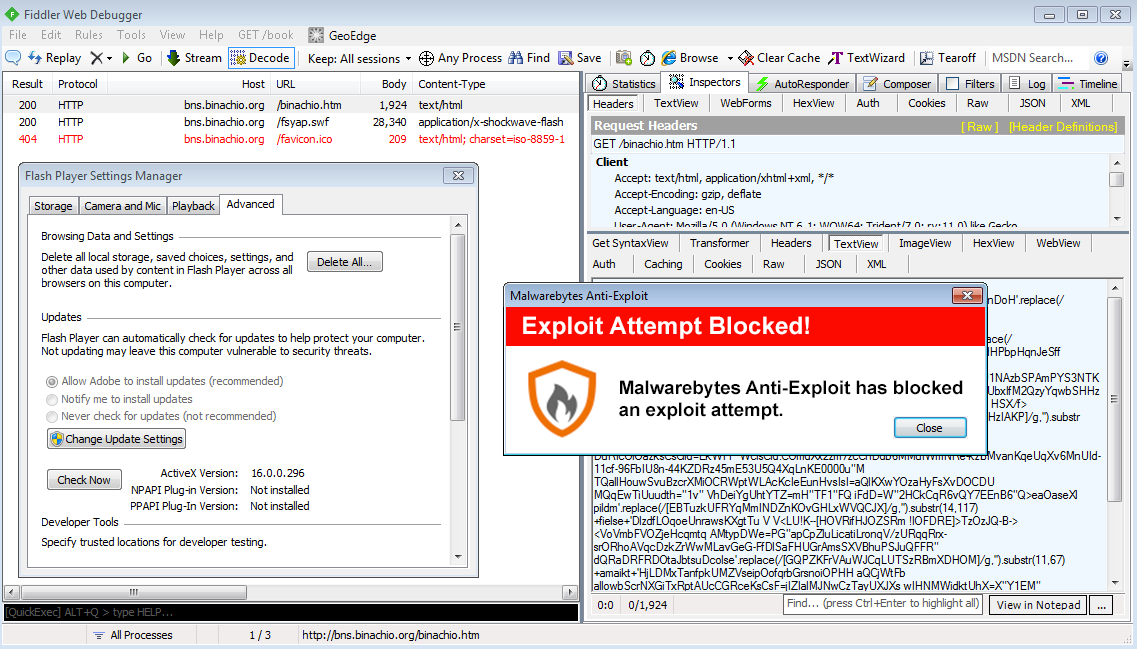
Malwarebytes Anti-Exploit users were safe thanks to our multi-layer, signature-less engine:
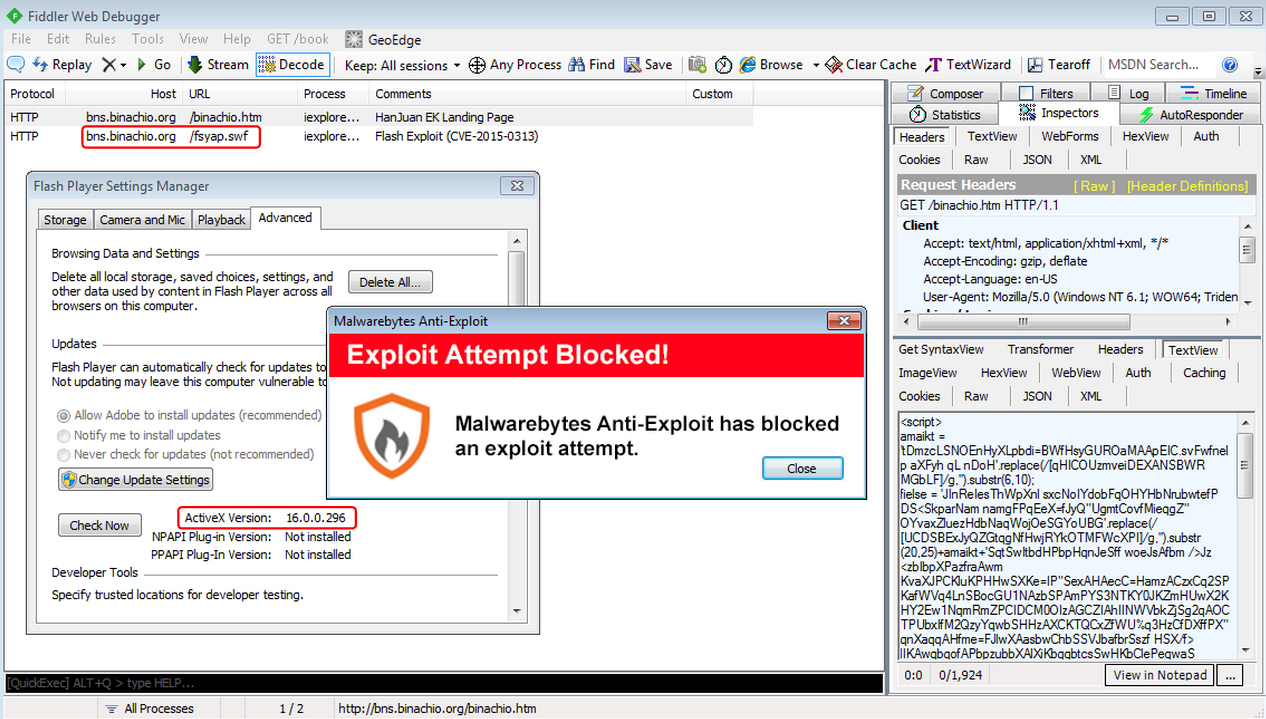
As mentioned earlier, this zero-day has been active and infecting people for some time (thanks Timo Hirvonen for the confirmation).
Adobe is aware of the vulnerability and working on a fix that it says it will release sometime this week.
Since this is an activate (and unpatched) threat, we advise extreme caution. Disabling Flash mitigates the risk but also degrades the browsing experience dramatically.
A combination of Malwarebytes Anti-Exploit and Anti-Malware remains one of the best lines of defence to defeat drive-by downloads and zero-days.