We’ve seen the latest phishing campaign targeting current and potential Netflix users. It’s served on the squatted domain, nefixx[DOT]co[DOT]uk.
It is clear from the screenshots below that the phishing pages is identical to the campaign that Jérôme Segura, one of our senior researchers, found and documented last August.
On one hand, both campaigns have notable similarities, too:
- Domains were registered days before they were in the wild
- Domains were registered via the “Crazy Domains FZ-LLC” registrar (Note that the registrant’s name and address may be fake)
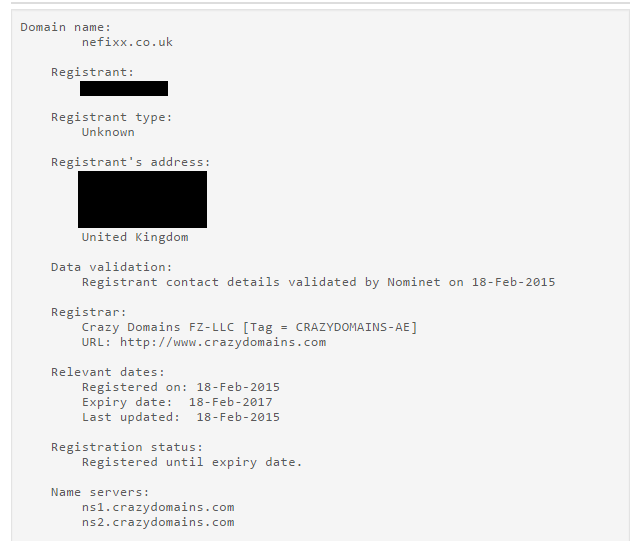
- Domains use long URLs, an effective tactic to trick users into believing that they are visiting a legitimate page when using devices with small screens
On the other, we have found some new things about the nefixx domain that are equally of note:
- Visitors of the domain are encouraged to sign up for a free trial of Netflix
- We believe that the primary targets of this campaign are UK and EUR users
- Domain retrieves the data of the site visitor’sGeoIP. We believe that it then uses this data to double-check if the visitor has been to the site before via the following request:
GET /email_identifier=71a605276e146b93e52b0c1bfb98ade285c337b0a6b7e5f3f560fd5bb11f1d1c/SecondVisit/index.php HTTP/1.1
- Domain then retrieves its list of banned or blocked IP addresses, we reckon, for comparison via the following request:
GET /email_identifier=71a605276e146b93e52b0c1bfb98ade285c337b0a6b7e5f3f560fd5bb11f1d1c/BanIP/BanIP.php HTTP/1.1
- Once confirmed that the visitor’s IP is already on the list, domain then prevents the page from loading
Again, dear Reader, please be wary of visiting pages appearing and claiming to be the real thing. Refrain also from clicking email links—usually the launchpad of a phishing campaign—when you receive offers that may be too good to be true, or you’ve just heard about. If you’re still not sure if what you received is bogus or not, best to contact Netflix.
Jovi Umawing










