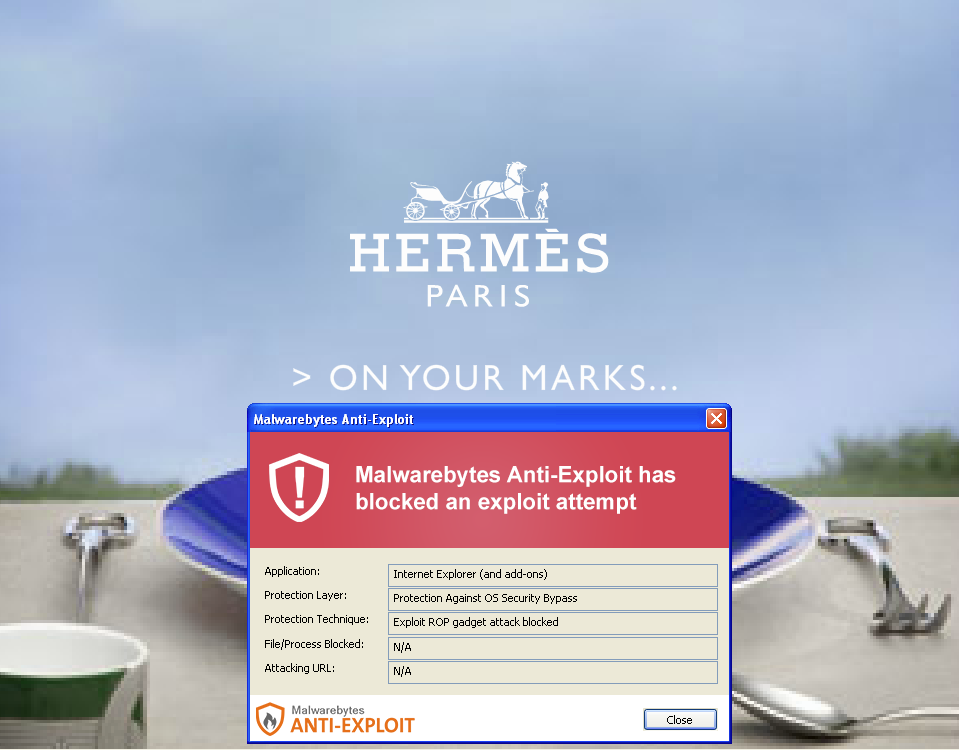
A few days ago, we blogged about a malvertising attack on the HuffingtonPost website via a major ad network which took advantage of a vulnerability in the Flash Player.
This campaign was stealth and did not last long thankfully, but another major attack was also being carried on around the same time, most likely by the same gang.
Working with ClarityAd, we quickly confirmed the malicious activity around 04/11 which showed a well-known ad network (merchenta) with direct ties to Google’s DoubleClick being caught in a large malvertising incident.
The latest malvertising attack was carried through merchenta, a company that provides a platform for ad exchange and direct integrations with top publishers. They boast a 28 billion monthly impressions for the US alone and work directly with top tier ad networks such as Google’s DoubleClick.
The criminals posed as an advertiser, infiltrated the platform via a third party and managed to house a malicious advert directly on merchanta’s ad platform which was fed into Google’s DoubleClick channels.
Although DoubleClick is not directly responsible for loading the malicious ad, it starts the chain of trust with the publisher, which unfortunately has little control over the subsequent transactions taking place.
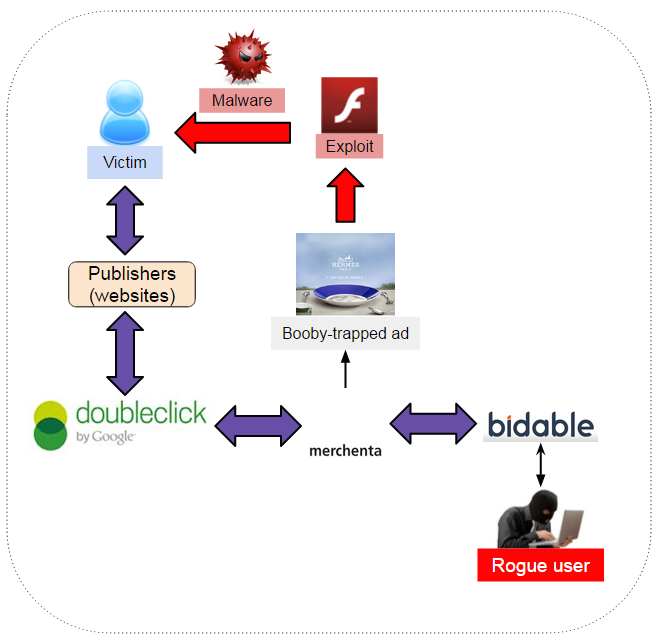
Upon contacting merchenta, we received a quick response. According to them, the account used belonged to Bidable.com (another real-time bidding company) and it was one of their clients that was fraudulent.
According to merchenta, the account was terminated by 10 AM UTC April 15.
Technical details
The initial DoubleClick URL:
http://googleads.g.doubleclick.net/pagead/ads?client=ca-pub-9446401110326037&format=300x250&output=html&h=250&slotname=2167943057&adk=876131117&w=300&lmt=1428791820{shortened}
Real-time bidding (read more about RTB here) takes place and goes through the merchenta advertiser:
api.merchenta.com/merchenta/analytics?campaignCode=BIDABLE-PF2AL-HERMESeaster-1&eventType=LOADED-RENDERING&stereotype=IMPRESSION&userHash=null&auctionId=GD5529a21200085e2b-abc9a029e006b7a_1_0
api.merchenta.com/merchenta/trackAuction?n=GD&c=BIDABLE-PF2AL-HERMESeaster-1&b=VSmiEgAIXisKvJoCAABrenpp7Z-Y6yb76gBLgw&a=GD5529a21200085e2b-abc9a029e006b7a_1_0&u=null
Finally, the malicious ad is directly loaded from the same advertiser’s website:
cdn3.merchenta.com/static/adlet/BIDABLE-PF2AL-dbf0f4fd9875ec824aa00a1f9bbfa4467a4335aa.swf
Exploit analysis
The Flash exploit that was used in this attack is exactly the same as the one we documented in the recent Huffington Post malvertising.
It is worth noting that this malicious SWF had zero detection on VirusTotal when it was first submitted.
It consists of the same ActionScript 3 :
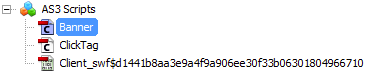
It builds up an array with shellcode in order to exploit the vulnerability via ROP gadget:
Malwarebytes Anti-Exploit blocks the malicious Flash advert from releasing its payload.
We did not collect the payload in this case but the one we observed in the other campaign was Cryptowall.
All ad networks have been informed, but the attack did last for a few days most likely infecting a significant number of people.
This latest example is yet another reminder of one of the big weaknesses with online advertising. Ad networks rely on third parties and the chain of trust can easily be broken when one rogue actor joins in.
I recently had a talk with someone who shared a very interesting story about how rogue advertisers are able to subvert security checks.
These crooks essentially pose as working for a fortune 500 company and submit a clean advert. The ad network is very interested because that will be a big customer and so they make sure to accommodate the client as much as they can.
The advert still goes through quality assurance and security tests before finally getting ready for prime time. Right before that happens, the rogue advertiser sends a new version of the ad (with only a minor change they claim) and the ad network, not wanting to lose a client, skips the checks that were already done.
It turns out that the new version of the ad is malicious and yet as full clearance to be displayed via major networks. This is just one of the many tricks rogue advertisers will use to insert themselves in the chain.
We would like to thank ClarityAd for their assistance in this matter.