We have been observing a very large malvertising campaign affecting dozens of top adult sites over the past week. All these attacks have a common element, a Flash based infection via a rogue advertiser abusing the AdXpansion ad network.
Readers of this blog may remember another instance of malvertising via AdXpansion and Google shortened URLs late last year, which was leading unsuspecting users to the Angler exploit kit.
No click necessary
Now this particular campaign is quite noticeable due to the number of sites affected and their popularity. According to stats from SimilarWeb.com, these adult portals account for a combined 250+ million monthly visits.
- drtuber.com 60.2 M
- nuvid.com 46.5 M
- hardsextube.com 43.7 M
- justporno.tv 32.5 M
- alphaporno.com 24.9 M
- eroprofile.com 18 M
- pornerbros.com 16.6 M
- pichunter.com 6.6 M
- iceporn.com 6.4 M
- tubewolf.com 6.2 M
- winporn.com 5.4 M
- …
As we have seen lately, more and more malvertising attacks are self-contained. The same fraudulent Flash advert is also used as the exploit, making it much more streamlined and sometimes hard to pinpoint.
The advert displaying sexual enhancement drugs, is loaded with malicious code that will immediately attempt to exploit the visitor, regardless of whether they click on the ad or not:
Technical details
The infection scenario starts when someone visits one of the aforementioned adult sites. The AdXpansion network loads an external advertiser URL:
hxxp://cs.adxpansion.com/public/ads.php?out=frm&zone_id={anonymized}&url=http://www.nuvid.com/video/28920/russian-mature&{removed} 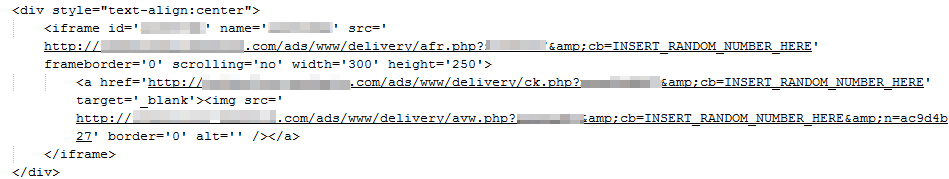
This advertiser is clearly not legitimate as the sole purpose of their platform is to deliver the malicious Flash-based advert/exploit:
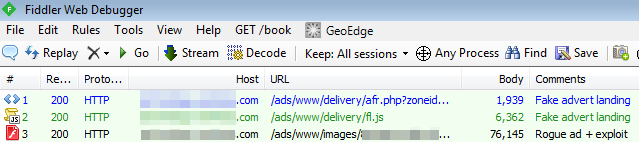
Flash exploit
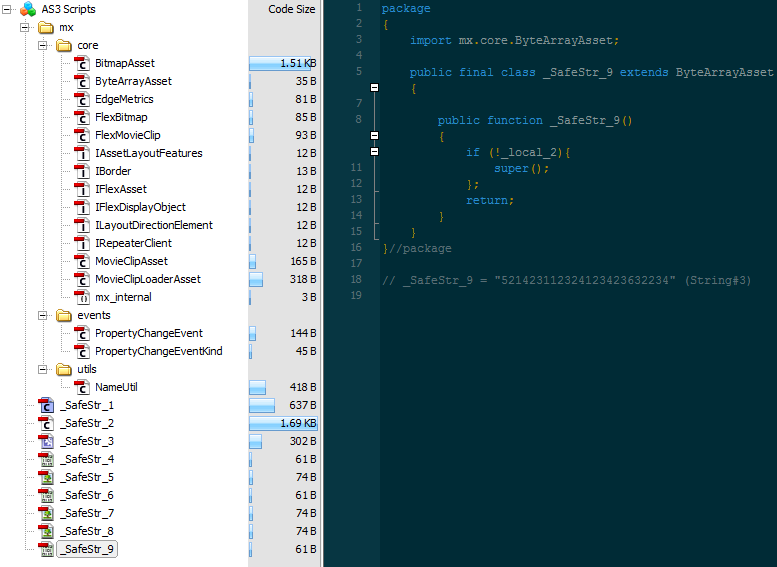
It consists of ActionScript3 code containing deceiving module names (i.e. _SafeStr_1). This Flash file is also quite different from most Flash exploits we see and could easily be overlooked as legitimate.
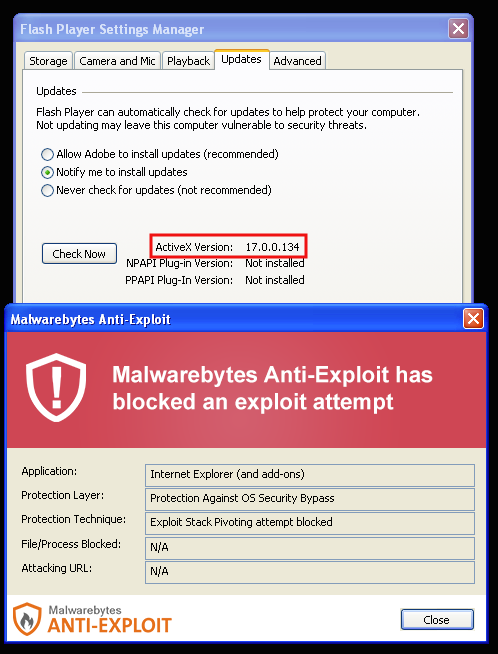
The bogus advert can exploit Flash Player up until version 17.0.0.134, released less than two months ago. Users of Malwarebytes Anti-Exploit are already protected:
The malware payload may vary but could result in multiple different malicious binaries dropped via a Neutrino-like EK (credit Kafeine).
It is interesting to see the trend of exploit kits taking the appearance of advertisers by leveraging Flash for serving the ‘creative’ and exploit in one single package. It is a minimalist type of approach which seems to work quite efficiently.
We have notified AdXpansion and they told us that the advertiser in question has stopped. We will monitor the situation and update if necessary.










