A recently patched Internet Explorer vulnerability (CVE-2015-2419) has already made its way into the top exploit kit on the market, Angler EK, according to security firm FireEye. The flaw affects Internet Explorer version 6 all the way to 11 and was rated critical by Microsoft in its July 22nd security bulletin.
Malwarebytes Anti-Exploit successfully blocks this attack:
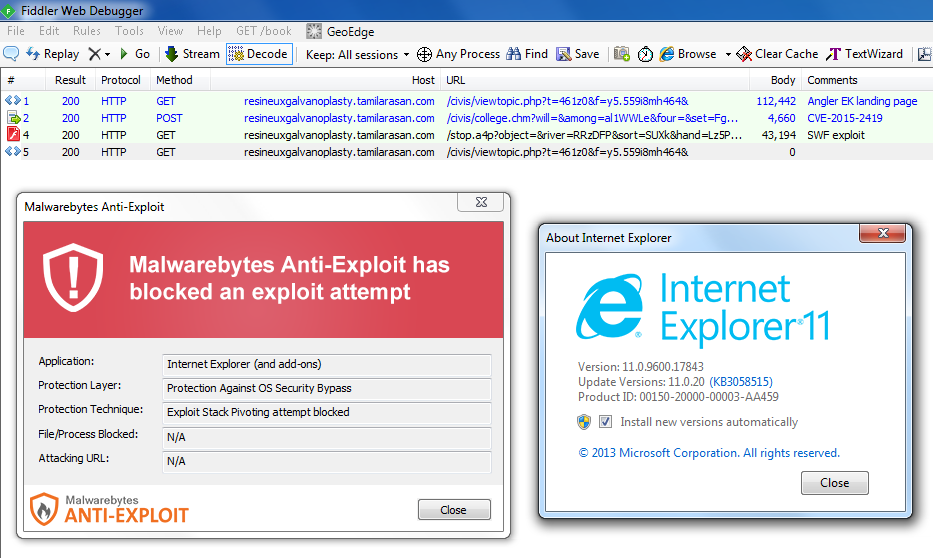
The Angler exploit kit keeps raising the bar higher and higher by not only adding the most potent vulnerabilities shortly after they are patched, but also by making it more difficult for security researchers to study the kit itself.
Angler uses a secret key exchange method to ensure that the infection will happen only once on the live machine being exploited. Efforts to replay the sessions later on using a packet capture will fail.
It’s interesting to note that the authors being Angler are not simply concentrating on Flash exploits, but also going directly for browser vulnerabilities. Indeed, given the recent attention the Flash Player has received, a slew of security updates have just been released, making exploitation more difficult.
The trend to go after browsers may get stronger as we saw recently a Firefox zero-day exploited in the wild and already a remote code execution in Microsoft’s newest browser, Edge.
We would like to thank Brad from MalwareTrafficAnalysis for sharing a reliable referer to test this new exploit.