The battle between the hacking group known as Impact Team and Ashley Madison operator Avid Life Media rages on in spectacular fashion as the hacking group delivers yet another round of serious blows to the “online cheating website” by releasing a 2nd torrent containing 20GB of proprietary company data.
No sooner had we finished discussing the original leak, containing over 32GB of confidential and often very personal information of a reported 37 million members, when another trickle of online snippets began to appear detailing the newest release.
Quantum Magazine, an online magazine accessible only via the dark-web client known as TOR, was first to get the scoop on the newest release. The online publication provides not only links to download the information, but also PGP security keys to help validate the authenticity of the data.
The newly released cache of files lacks the impact to customers that was seen with the first disclosure, but still contains a wealth of information which could prove valuable to future attackers.
The information contained within the torrent primarily revolves around source code for various Avid Life Media websites. Information surrounding the detailed workings of major brands such as Ashley Madison, CougarLife, EstablishedMen, and SwapperNet can all be found within the trove of information. While not nearly as interesting, the data contained within this release will be poured over by attackers looking for vulnerabilities allowing additional attacks against the company infrastructure and additional harm to the company brand.
For those looking for more damning information against the site’s executive staff, the most interesting bit of data may come with the release of a 13GB archive purportedly containing the email of CEO Noel Biderman. The archive, titled ‘noel.biderman.mail.7z’ is larger in size than all of the extracted source code directories combined. This would suggest that there is a great deal of information within the compressed file.
In what may be the only bit of good luck Avid Life Media has been able to tout all week, it appears as though the archive containing Mr. Biderman’s personal communications was damaged sometime during the compression of the data. To no avail, a number of attempts were made at repairing and extracting the archive. Despite these best efforts, the data contained within the file is inaccessible. This seems to be a common problem as others have also posted about their struggles in trying to repair the damaged file.
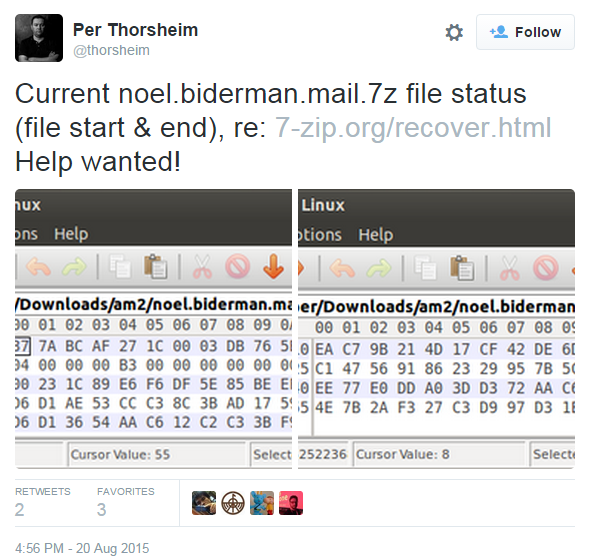
This combination one-two punch has been devastating to the reputation and credibility of the company responsible for negotiating the extra-marital affairs of individuals seeking a bit of spice in their sex life.
Savvy computer programmers are already working to develop searchable databases containing names, email addresses, locations, personal sexual desires, and chat histories of the site members, and new compilations of the data are being posted by the hour. Efforts are being made around the clock to parse, analyze, and post the stolen data to help others who are curious to determine if their loved-ones have been utilizing the service. The sort of community hacktivism (if you will) being demonstrated is allowing anyone with the skill-set to compile a few lines of code the ability to lend resources in what they feel to be the fight against moral turpitude. This isn’t something that typically occurs with large, notable security breaches where financial prosperity is the primary motivator.
If the meticulous level of consideration demonstrated by Impact Team in the release of this information offers any insight into the OPSEC employed by the group throughout the course of the breach, it may prove a difficult task for law enforcement and security researchers to track down the identity of the person (or persons) responsible.
The claims made in the original demand letter allude to the fact that the group has been present within the company infrastructure for ‘the past few years’. If this information is to be believed (and considering the accuracy of the other claims made by the group, there is little reason to give doubt) it could be an act in futility to try and uncover originating attack vectors or suspicious internet traffic as the necessary log files and/or server logs could have been disposed or misplaced. If this is the case, we may never learn the identity of the group known as Impact Team, and may never learn the vector that was used for infiltration.
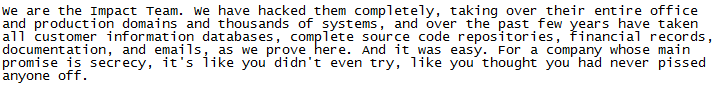
While it’s yet to be seen if Impact Team will provide additional dumps of Avid Life Media company data (there’s still that 13GB email file that no one can seem to open), it’s a fair bet to say that this won’t be the last time that we see the sort of purist-philosophy which has been demonstrated in this attack.
Companies should all take note (especially those in more questionable lines of work) of the dangers that can occur when company data is stolen and posted to the internet.
It can’t be stressed enough the importance in securing intellectual property to help mitigate a potential breach. Ensuring that systems are kept up-to-date with the latest updates and software patches is also vital in securing internal systems. The use of a reputable antivirus and anti-malware product, such as MalwareBytes Anti-Malware provides the additional layers of protection necessary to help stop unwanted programs from wreaking havoc on internal systems.
While these security suggestions are not a fail-safe to prevent all security breaches, following all available industry standards and maintaining a security best practice will provide many of the necessary protections to help mitigate potential losses from compromised systems.
Don’t say we didn’t warn you!










