The Microsoft tech support scam has been going on for years, starting with cold calls originating from India. Over time fake websites and pop ups warning of infections for Windows, Mac, Android and even iOS users were created.
The vast majority of victims are from the U.S., Canada, the U.K., Australia, South Africa and New Zealand; in essence countries where English is the primary language spoken.
This is about to change though, as tech support scammers are tapping into brand new markets in Europe but also Japan. The first efforts to go after people in non-English countries were quite clumsy, as for instance with this case in Spain documented by David Harley over at ESET.
Security researcher Malekal also reported on a French version of the scam which was just terrible, and clearly the work of a non native speaker, but was nonetheless a first attempt.
The latest iteration we uncovered is targeting multiple new countries and considerable efforts were spent to make the templates look professional and authentic.
New targets
- France (population 66 M)
- Spain (population 46 M)
- Germany (population: 81 M)
- Japan (population: 126 M)
These fraudulent pages typically show up via malvertising campaigns or as part of a bundle within Potentially Unwanted Programs.
[soundcloud url=”https://api.soundcloud.com/playlists/135549732″ params=”auto_play=false&hide_related=false&show_comments=true&show_user=true&show_reposts=false&visual=true” width=”100%” height=”300″ iframe=”true” /]
Translation to English:
Warning! A virus has been detected on your computer. Please call the number provided immediately to remove adware, spyware and viruses from your computer. Seeing this message means that all your personal information, pictures, passwords and credit card details are at risk and vulnerable to attacks. Do not use the Internet, do not connect to any website or make any purchase until you call the phone number provided.
Actual native speakers
We called one of the numbers for the French campaign and talked with an agent that spoke fluent French. He turned out to be working from Québec, Canada, something that was given away in the scam page URL:
hxxp://8yrkjfmd.com/help/fra/9300bbd8382a4e91bb5a73fdf383fef3?subid=quebec-sot-EZxcgJli&subid2=w0QMBNDVCPVPNHUL0U27DTHI&transaction_id=f2599d8d-19be-4cc4-802c-24e7e0f1ff3f&random_page=300bbd8382a4e91bb5a73fdf383fef3&c=
The other versions of the scam (German, Spanish and Japanese) also featured people speaking the national language, with some degrees in how fluent they were.
We suspect that one or more organizations are outsourcing dedicated call centres in each country and have given them instructions on how to dupe customers who phone in.
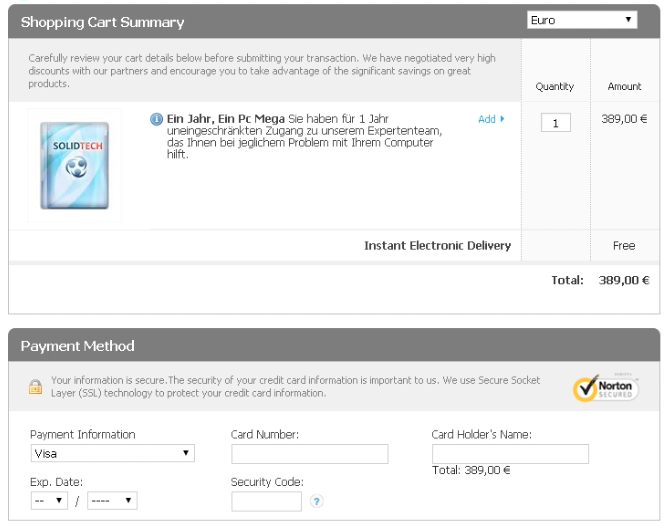
In the picture above, German customers are defrauded of 389 Euros (roughly USD$430) to remove non-existent problems from their computers.
Stealthy and flexible operation
All the domain names registered for this specific campaign were done via a Chinese registrar, while the actual registrant was hiding behind a proxy.
- Registrar: Nanjing Imperious Technology CO. LTD
- Registrar Country: China
- Creation Date: 06/10/15
- Host: Amazon Web Services
The source code for each page includes a special tag to prevent search engines from crawling or indexing any of the content:
NOFOLLOW,NOARCHIVE,NOSNIPPET,NOODP,NOYDIR">
The toll free number used in each pop up is dynamically generated using an API, a big change from amateur campaigns where the phone number is hardcoded as text or within an image:
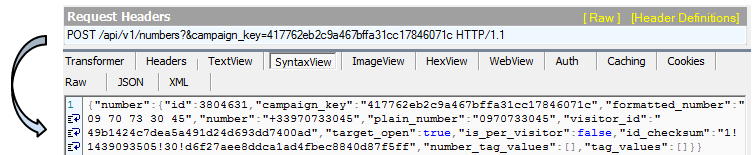
We cataloged over 400 different phone numbers used in the French version of the scam. Typically those toll free numbers are bought in bulk and can be discarded easily. It very much resembles blacklist evasion techniques used by malware authors with domain names.
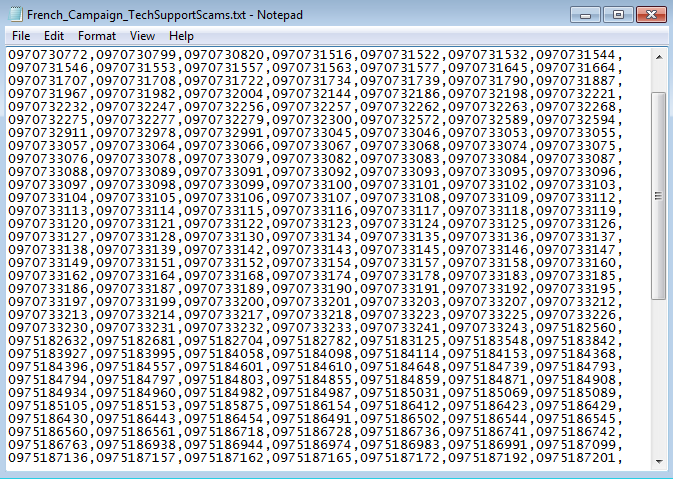
Based upon our investigation, several tech support call centres located worldwide are involved in this operation. It will take a concerted effort from multiple parties to take each down while we have no doubt the rogue actors will keep on moving and continue to defraud thousands of people.
Avoiding the scam
The best protection against these scams is awareness. Please pass the word around to family and friends, especially older ones or those not computer savvy. We also have a resource page with plenty of information that is well worth a read.
What we can say looking back at all these years since the tech support scams started is that crooks have been able to adapt the con, often times getting inspired by actual malware authors and their practices (i.e. Browlock, fake BSOD, etc…).
This latest twist is without a doubt going to have a serious impact on countries that have never really experienced tech support scams before. Not only are people not prepared for it, but also the fraudster will appear genuine by speaking the local tongue.
While non English speaking countries were mostly safe, scammers realized that millions of potential victims were within their reach, especially in European countries. But since the scam relies heavily on social engineering, they had to find a way to breach the language barrier. Well, they have done it.
Thanks @eN_Drop for the hat tip on the French landing page.
Japanese security bulletin (thanks @MalwareMustDie).










