The site called Putlocker may be at least familiar to anyone who have searched online for free, non-region restricted video streams of popular movies and television series.
We’ve also seen a number of its duplicate sites registered under various top-level domains (TLDs). It has grown quite popular after all.
Having the urge to binge on the classics like Airwolf may seem irresistible; however, think twice before giving in. Not only is piracy illegal in some countries, but you may also find that several streaming sites may lead to more than just free videos.
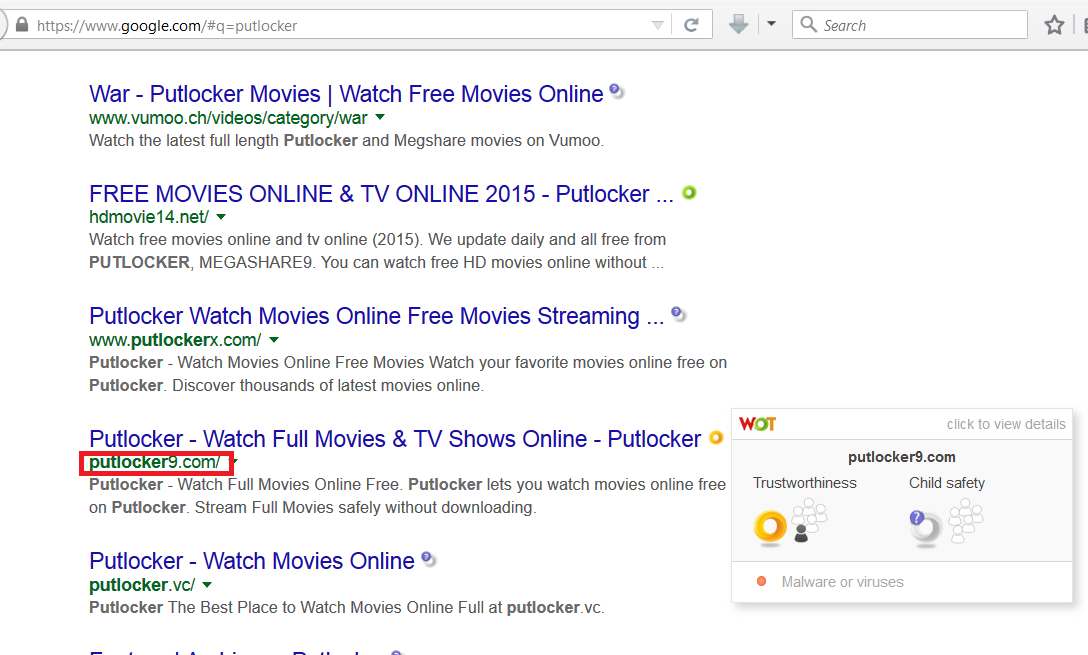
Case in point, we recently found putlocker9[DOT]com. If you have the Web of Trust (WOT) app installed in your browser, you may easily note that visiting this site could mean being exposed to danger. If you don’t have the app, then it becomes a matter of learning things the hard way.
click to enlarge
Visiting the aforementioned site loads up a replica of the real putlocker[.]is domain but with notably slight differences. I’m sure you can spot them yourself, dear Reader, if you look a little closer.
The difference between the .com and the .is site is more apparent if we look at their WHOIS data: the former is hiding behind the benefits of CloudFlare, a known tactic typical to online criminals in order to preserve their anonymity; the latter undoubtedly has more useful info to look at and consider.
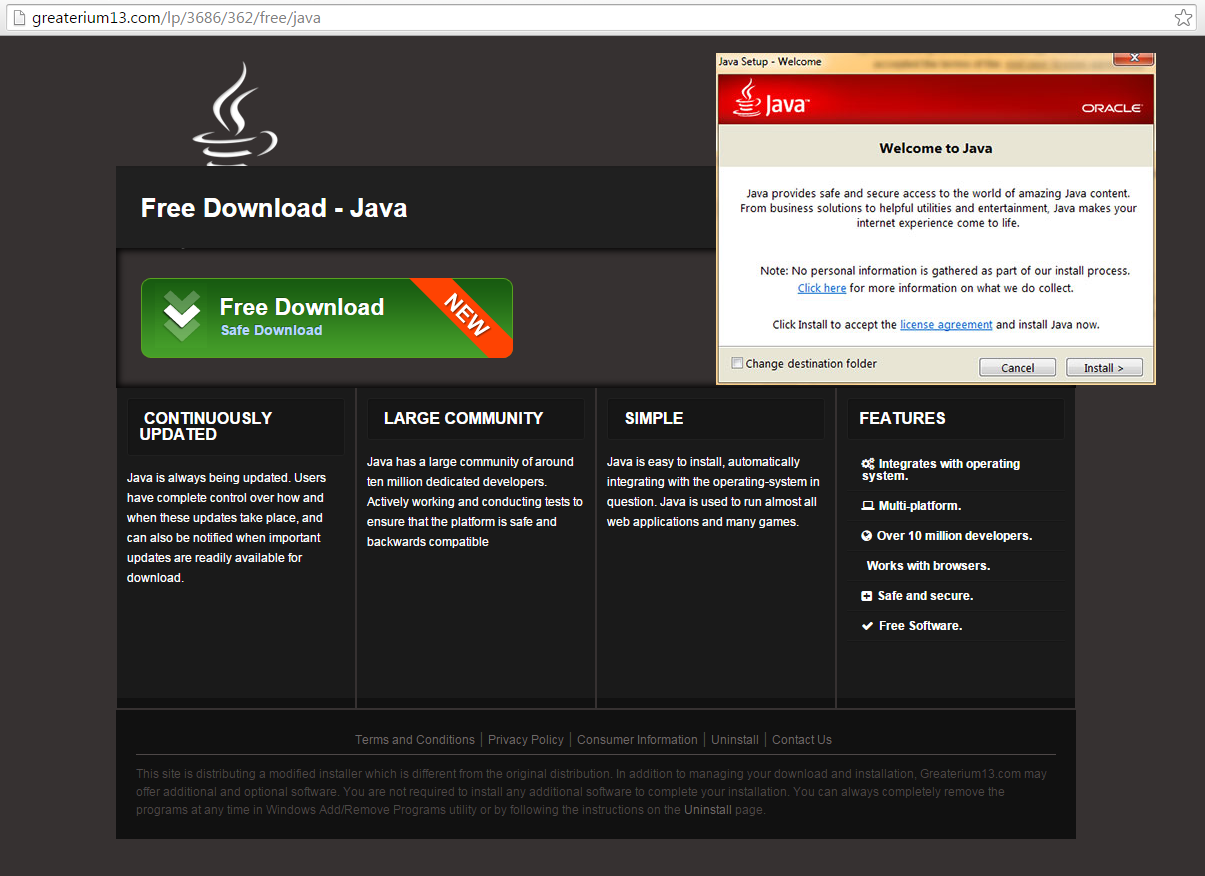
Users who accidentally click on any part of putlocker9[DOT]com will notice that a new browser tab opens, direct them to random sites offering various tools or with prompts of software updates, such as one for Java.
click to enlarge
Clicking the green “Free Download” button directs to another page. Below is the slideshow of events that follow and an overview of the downloaded file, which is setup.exe:
Needless to say, this file is a potentially unwanted program (PUP), and Malwarebytes Anti-Malware users are protected from it.
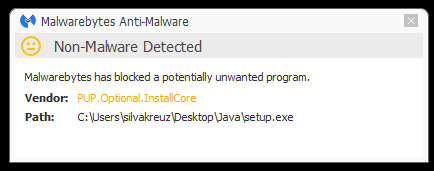
Our software also blocks dodgy URLs mentioned in this blog and the destinations users may be directed to when they visit the .com site.
Java prompt lookalikes are not uncommon; however, we may see more of them popping up after Oracle released a critical patch early last week. It’s possible that this is a campaign similar to what one of our researcher documented not so long ago. To echo his words: save yourself the hassle and get protected.
Jovi Umawing (Thanks to Steven)









