Image File Execution Options (IFEO) are used for debugging. Malware, however, does not only check if there are debuggers active, but it’s also known to use the features IFEO has to offer to their own advantage.
Intention
IFEO settings are stored in the Windows registry. The intention of creating the IFEO registry key is to give developers the option to debug their software. This is relatively easy to do. Developers can attach any program to any executable using the registry key—
HKEY_LOCAL_MACHINESOFTWAREMicrosoftWindows NTCurrentVersionImage File Execution Options{name of the executable}—and adding the value
“Debugger”=”{full path to the debugger}”For example, if you use Process Explorer, there is an option to “Replace Task Manager”:
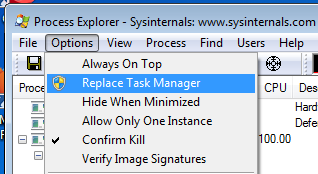
The above action results in the corresponding key and value below:
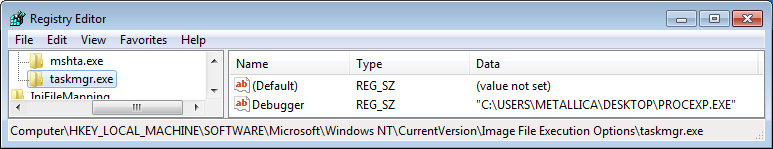
As a result, if you use Ctrl-Alt-Del and “Start Task Manager” or any other method that normally opens Task manager, Process Explorer opens as well.
Analysts
It won’t be hard to imagine the use this option can have for malware analysts. For example, you can use it as a breakpoint if you know the malware you are working on starts another executable like cmd, powershell, or iexplore. And it’s really easy to check which arguments are used since these are passed to the debugger.
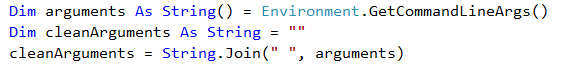
Malware
For malware authors, there are several reasons to be interested in IFEO:
- First, it offers a starting point for your code. You can attach your executable to a popular Windows executable (preferably one that runs by default) and yours will get run as well. Userinit.exe and iexplore.exe are examples that were used often in the past.
- Secondly, you can interfere with protective software by attaching a debugger to the main executable of said software. An “ancient” example is Ushedix, which used this method to disable a host of security programs that were popular at the time.
- And last but not least, malware can check if there are any non-default entries under the IFEO key(s) as a way of determining if it has landed on an analysts machine and change its behavior accordingly.
Some extra background information
As pointed out earlier these options were intended for debugging, but since there is no check if the program listed in the “Debugger” value really is a debugger, the possibilities are legion. On the other hand the application that you select to intercept has to be an executable. You can interfere with the normal behavior of DLLs as well, but you would have to use the value BreakOnDllLoad to accomplish this. Which handles quite differently as it does not pass on to another executable or DLL. The only options for that value are “on” and “off”.
Malwarebytes Anti-Malware checks the IFEO key for malicious entries, generically detects them as Security.Hijack or PUP.Optional.IFEO and is able to remove them.
Summary
Image File Execution Options are used to intercept calls to an executable. The intended use is for debugging or for replacing applications, but using it as a means to simply stop the executable from executing altogether has been common practice as well.
Pieter Arntz











