We recently stumbled upon a malvertising incident on a large British newspaper site which we decided to investigate in greater details.
As with many attacks we have found lately, the line between legitimate advertisers and rogue ones is getting finer and finer. Indeed, in many cases ad networks simply cannot tell them apart without actual proof of malicious activity.
As we outlined it in our recent research paper entitled “Operation Fingerprint“, replaying those attacks can be extremely difficult, and without the smoking gun, one cannot simply close a case.
To illustrate this point, we will check out this incident and show that there is a proliferation of rogue advertisers using clever disguises to push booby-trapped adverts.
Malvertising Flow:
- dailymail.co.uk
- adclick.g.doubleclick.net
- track.bridge.systems (Russian RTB?)
- cdn.exeterquads.com (Fake ad server)
- geraeuschvollste.ciderstore.co.uk (Angler EK landing)
At first sight, exterquads.com looks like a legitimate business (which it is) located in the UK. However, the subdomain (the ‘cdn‘ preceding the main domain) was registered via criminals who managed to steal the registrant’s credentials in order to create a rogue URL that points to their own server. This is called domain shadowing.
Legitimate domain:
Hostname: exeterquads.com IP address: 5.196.39.216 Running on: Microsoft-IIS/8.5Rogue (shadowed) sub-domain
:
Hostname: cdn.exeterquads.com IP address: 5.63.145.76 Running on: nginx/1.0.15
The crooks also stole the graphics from this legitimate business to create an ad banner which looks rather convincing but is meant to be a decoy for the real motivation behind this attack. Indeed, alongside the banner, an innocuous 1×1 pixel image is served (supposedly for tracking purposes).
This is where fingerprinting happens. The rogue code hiding in the image can be decoded to reveal a nefarious intent to identify real victims and eliminate those running security tools, the latter being of no interest to the criminals.
The final part of this rogue code is to launch the exploit kit URL, which for all these campaigns has been Angler EK.
Because this campaign was aimed at people living in the UK, we searched for additional rogue advertisers abusing other businesses. We found quite a handful of them that have been used in recent attacks.
The below ad banners were all made up from scratch, respecting the logos and colour schemes of the legitimate brands they exploit, while their respective owners had absolutely no idea about it.
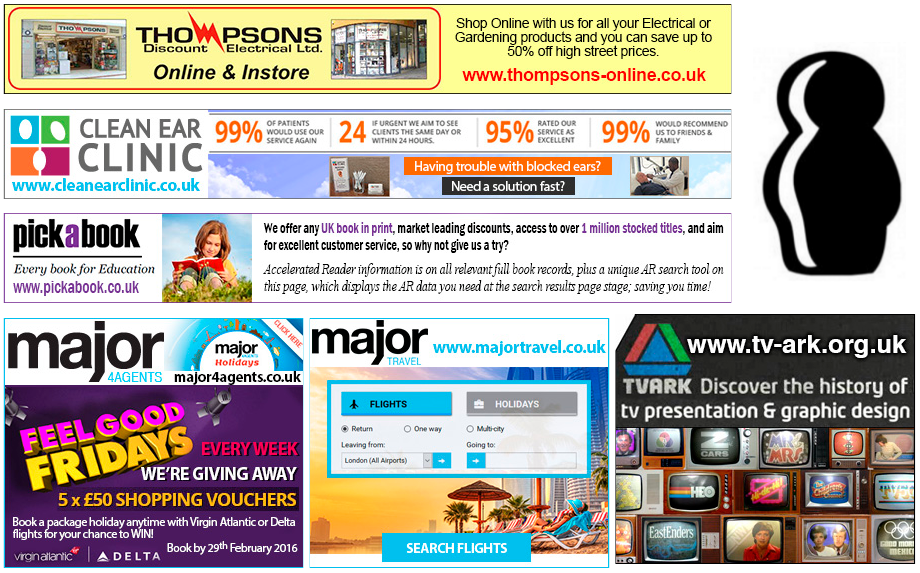
List of sub-domains:
- ads.thompsons-online.co.uk
- banners.cleanearclinic.co.uk
- st.pickabook.co.uk
- front.major4agents.co.uk
- pix.majortravel.co.uk
- promo.tv-ark.org.uk
As mentioned above, one way to determine whether an advertiser is legit is by checking the domain info and seeing if there are any discrepancies between the main domain and sub-domain.
Also, many of those rogue subdomains use free SSL certificates, while the core domain doesn’t.
Perhaps the ultimate proof is the presence of the fingerprinting code. Although it is not easy to spot it in a live capture, it is by far the most convincing argument to bring up when reporting malvertising cases to ad networks.
The UK malvertising campaign is of a rather large size, just after the US one. We have also spotted specific campaigns targeting Canadians, Australians and the French with a similar modus operandi. The amount of work spent forging legitimate brands and advertising under such disguise is really astonishing.
We managed to get in touch with one company whose brand had been abused and they clearly were none the wiser when asked whether they were aware of this ad banner residing on a sub-domain. However, they managed to find out the source of the problem once they talked with their hosting provider.
Malwarebytes: I imagine this is not one of your sub-domains, correct? We see these kinds of attacks more and more where rogue advertisers are creating ad banners and using subdomains to fool ad networks.
Victim: Thanks for the heads up. I have talked to my hosting provider and there was in fact a breach. How did you come across this? BTW I have used (and still use) your software, it is fantastic.
This kind of attack is a reminder of just how many different ways a website can be compromised or leveraged to fulfill certain goals. It also shows how difficult it can be for ad networks to vet new customers and weed out malicious ones.










