Update (04/19): AdsTerra reached out on Twitter but we are still waiting for a point of contact to send information. AdsTerra also requested that we removed their logo from this blog post for copyright purposes, which we did.
The Magnitude EK has been on the forefront of most of the malvertising-driven attacks we have seen in the past few weeks. In fact, the intense activity it is generating is overshadowing other exploit kits and distribution methods such as compromised websites.
Magnitude EK recently showed some signs of additional refinements, first with the implementation of a fingerprinting gate before the exploit kit landing page as well as the integration of a new Adobe Flash Player zero-day, albeit not fully taken advantage of.
The direct reason for this flood of Magnitude EK activity is the use of ad networks that are responsible for malvertising on a large scale. By far, the majority of incidents have come from AdsTerra (AKA TerraClicks) which we have contacted but have not heard back from.
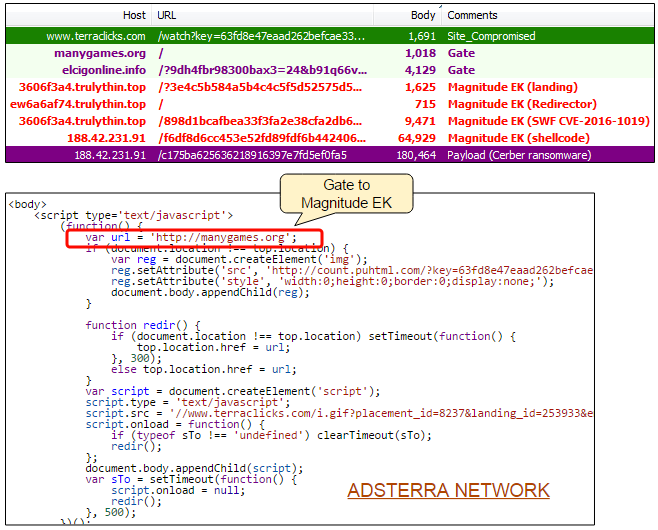
In the past two weeks, we have documented over 400 unique malvertising incidents coming out of AdsTerra. These malicious advertisements were displayed on a variety of adult sites and torrent portals and the ultimate payload was the Cerber ransomware.
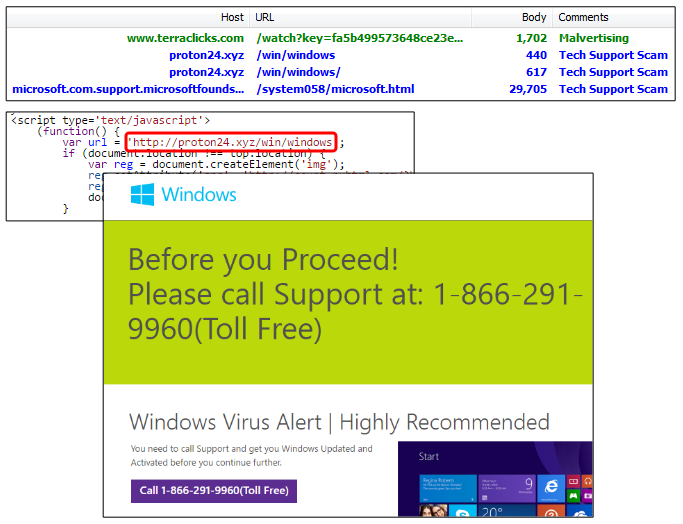
Those that do not get redirected to the Magnitude EK are likely to run into the infamous tech support scams:
To protect our users (Malwarebytes Anti-Malware Premium), we have decided to blacklist the terraclicks[.]com domain which will effectively block any ad coming out of AdsTerra and prevent infections and scams.










