A variant of Android/Trojan.FakeApp is stealing the identities of popular applications (apps) such as TrueCaller and Torque Pro.
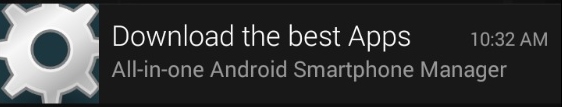
As soon as the FakeApp is installed a shortcut with an icon stolen from one of these popular apps is created, and a notification pops up. The notification also appears whenever the shortcut icon is clicked.
The code that creates the notification is pretty simple, and points to the domain apx.avazutracking(dot)net which redirects to another website.
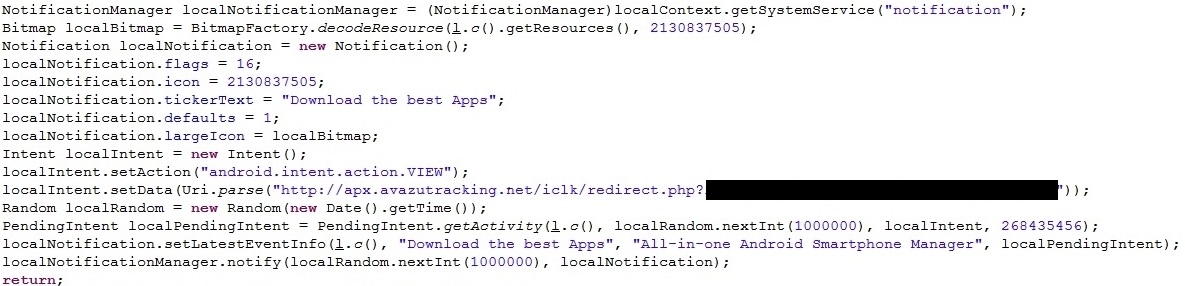
Click the notification and the redirect from apx.avazutracking(dot)net will send you through a list of several other redirects, which are all randomly determined by the last.
Some of these redirects are to ad sites so the scammers can gain a little revenue from pay-per-click browsing. Eventually the redirects end on a series of different websites. Sometimes it even ends on Google PLAY itself; pointing to the details page of a specific app to install. Here are some examples:
If a user installs the app offered the scammers get a little more revenue. If a user fills out the information for the sweepstakes they supposedly “won”, once again they get paid, but with the addition of a third-party gaining personal information about the user.
There are hundreds of variants of FakeApp like this out there being distributed thousands of times, and it only takes a small percentage of people to be tricked for the people behind it to make many.
Don’t get fooled by such shenanigans yourself; if it looks phishy, it probably is.










