Virtual machines are a great tool to run untrusted piece of software and analyzing the network activity. Most of the time, the default networking configuration uses a bridge to allow VMs to communicate. One caveat about this approach is that both the VM and the host will access the same network (like a personal trusted LAN for instance…), something definitely not desirable.
Multiple solutions exist to isolate the untrusted VMs from the host LAN. A few years ago we spoke about JanusVM which is no longer maintained and not so easy to set up. A more recent solution uses VirtualBox, Tor, and Whonix alongside Wireshark and is pretty quick to set up without bothering with DHCP or other network protocols.
Whonix is an OS designed to run as a set of VMs with pre-installed and configured applications. Among other features, it uses Tor for all network connection thanks to Whonix-Gateway, a VM dedicated to be used as a gateway between Whonix VMs to the Tor network.
However, please note that UDP traffic won’t work due to Tor limitations. DNS queries will use Tor DnsPort on the Whonix Gateway to avoid leaks.
- Download Whonix-Gateway (look for Download Whonix-Gateway link),
- Download the associated signature, and the SHA512 file (also provided with its signature),
- Check them both,
- On VirtualBox, simply import the .ova downloaded above with File > Import Appliance,
- Leave the default settings untouched, read and agree the agreement,
- Start Whonix-Gateway VM and follow the initial instructions,
- You may want to activate the auto-update when prompted,
- For the VMs you want to redirect the traffic, go to Settings, Network and select Internal Network. Set Whonix as name.
Once Whonix-Gateway has been configured, you get the following network configuration:
auto eth1 iface eth1 inet static address 10.152.152.10 netmask 255.255.192.0 Thus, you can assign your VMs in the range 10.152.152.10 /18. For instance, the following static IP configuration is used for a first VM:
IP: 10.152.152.11 Mask: 255.255.192.0 Gateway: 10.152.152.10 Primary DNS server: 10.152.152.10 All the traffic will now be isolated from your host LAN, and will only use Tor (including DNS queries). In order for this setup to work, whenever you want to connect one of your VM, the Whonix-Gateway has to be up.
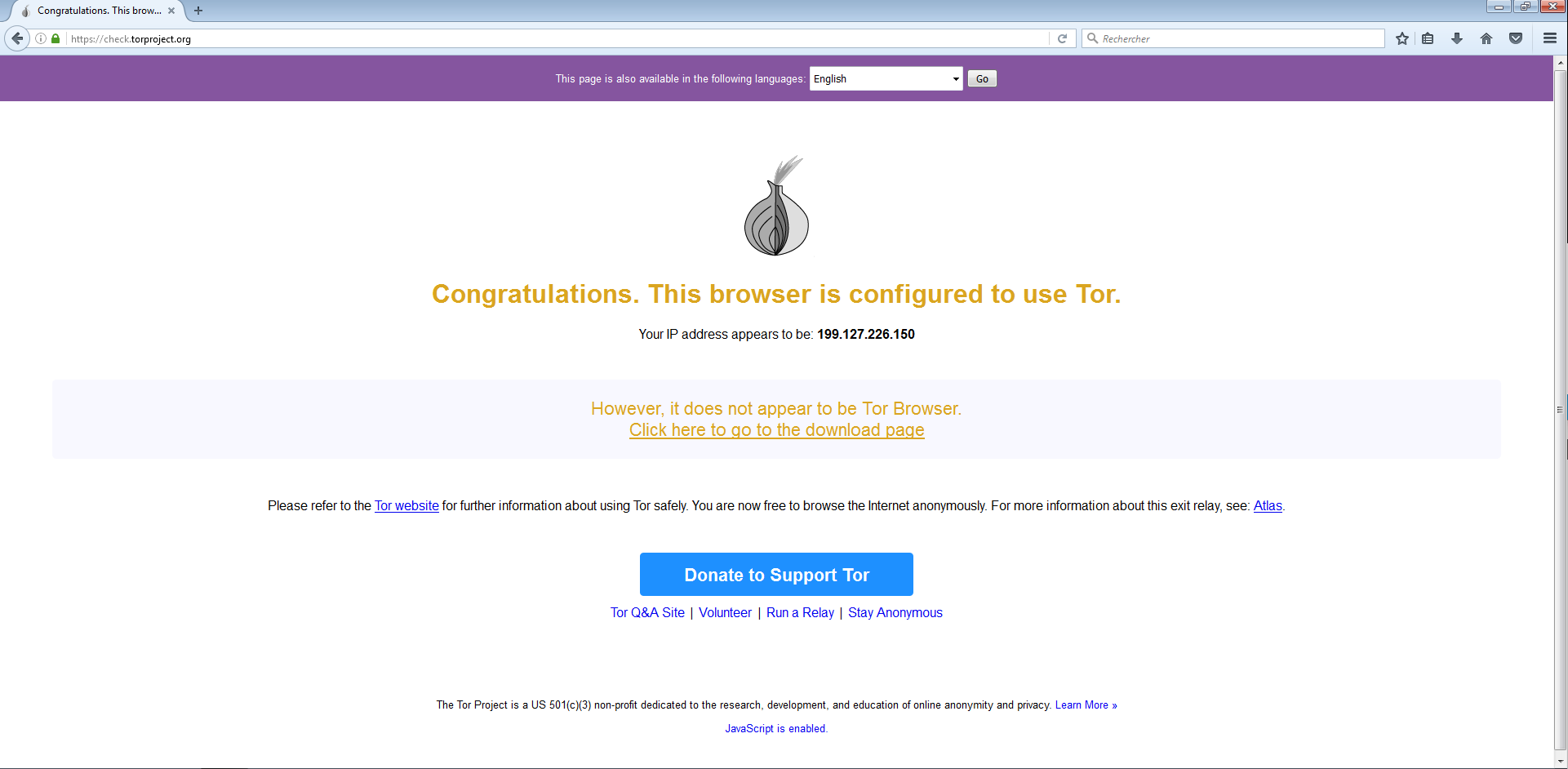
check.torproject.org status page
A visit on check.torproject.org from inside a VM using Whonix-Gateway should confir that the setups is working as expected.
Please keep in mind that this setup should not be trusted to provide serious anonymity guarantees.
Once the VMs are setup, simply install Wireshark or tshark. Configure them to listen on eth1… and profit!
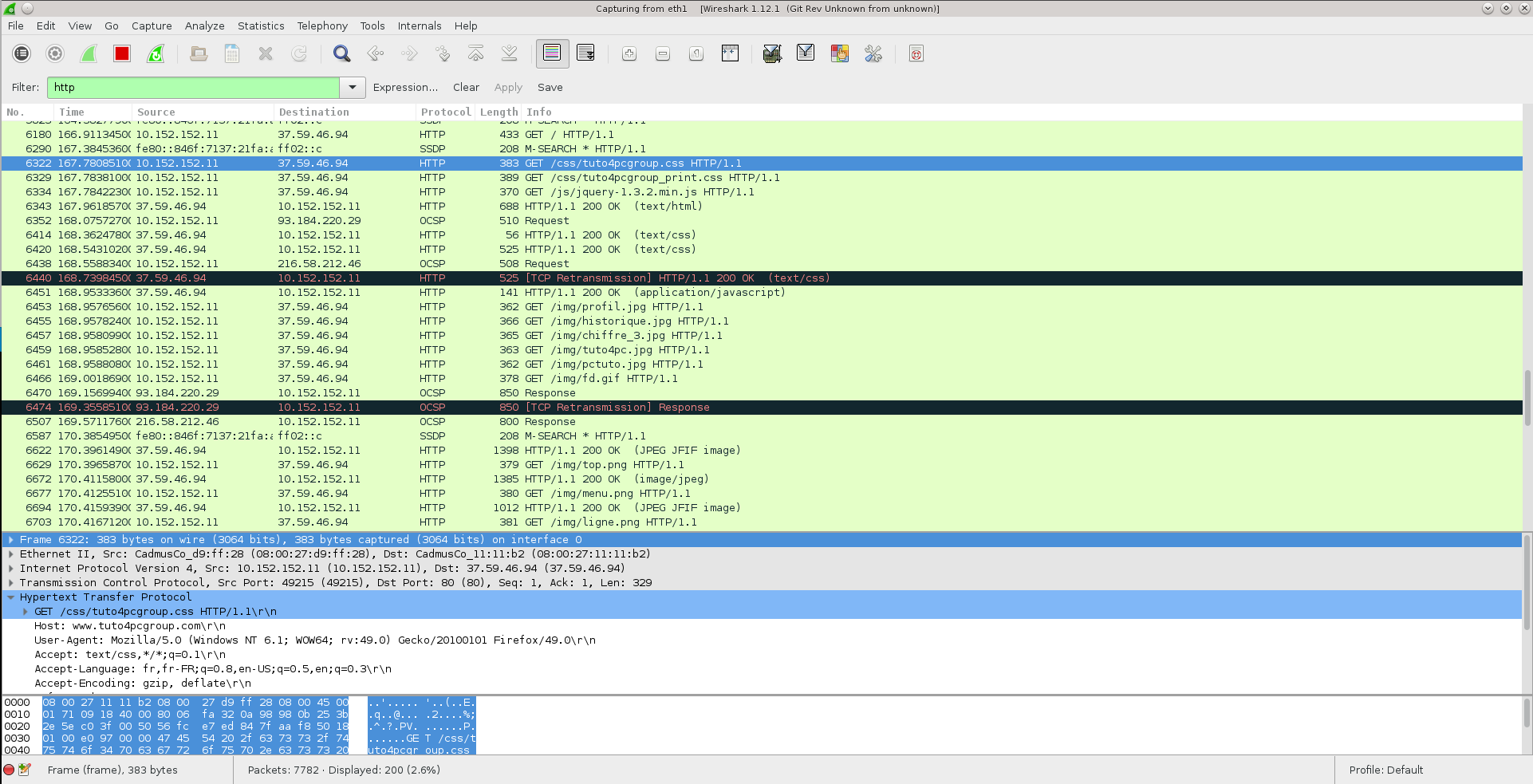
Wireshark listening on eth1 on the Whonix Gateway.











